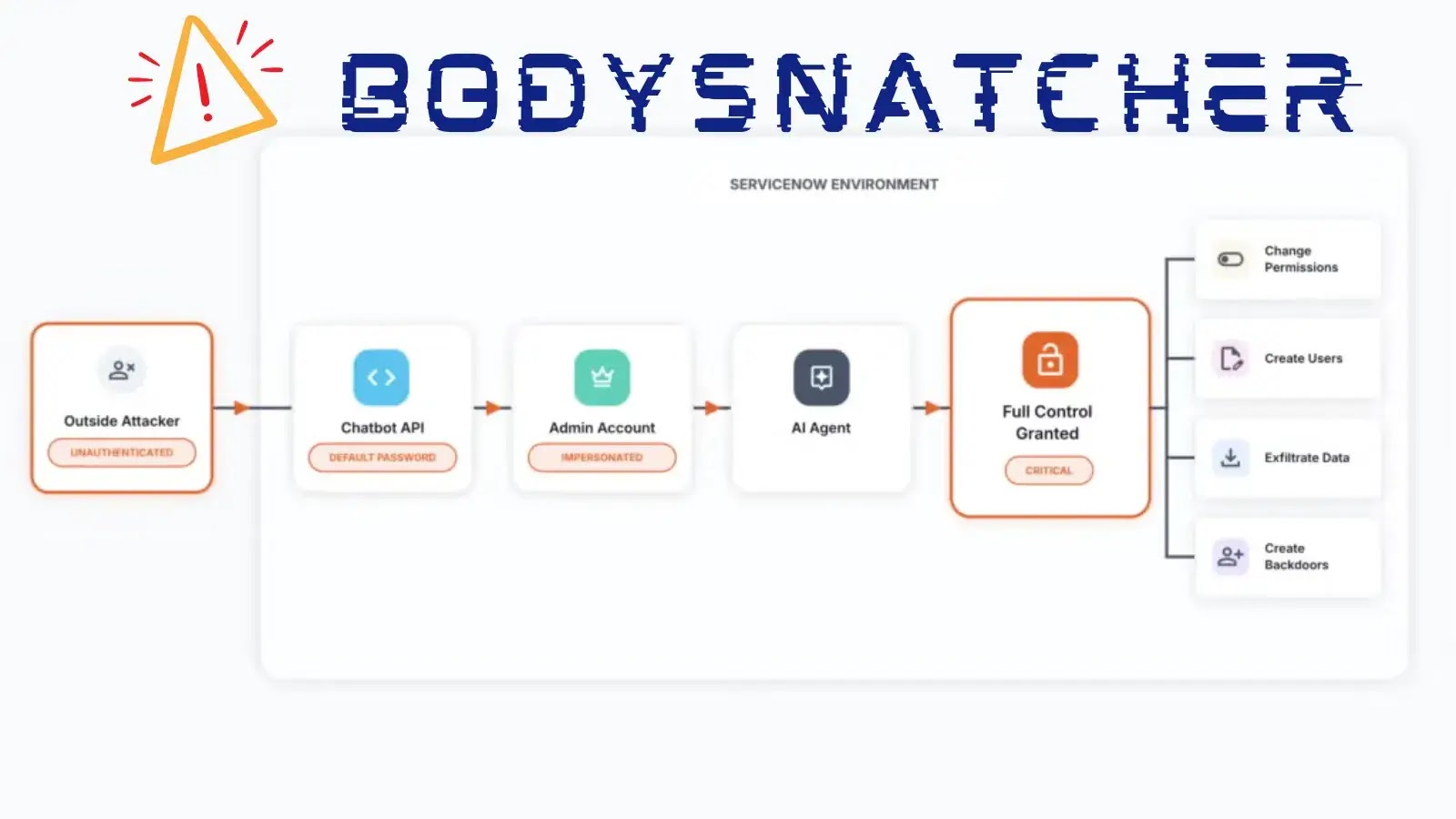
In a compelling demonstration of how seemingly minor misconfigurations can unravel vast criminal enterprises, recent cybersecurity research has unveiled a critical vulnerability in a [...]
Unmasking GhostPoster: A Browser Extension Threat Stealing User Data The digital landscape is a minefield, where even seemingly innocuous browser extensions can harbor malicious [...]
In a concerning development for users of Xiaomi’s popular Redmi Buds, security researchers have unearthed critical vulnerabilities within the earbuds’ firmware. These flaws, which [...]
A silent threat lurks within the heart of many enterprise networks, capable of turning a seemingly minor flaw into a full-scale Active Directory compromise. [...]
Browser extensions are often touted as tools to enhance productivity, block ads, or improve privacy. However, a recent and alarming discovery by cybersecurity researchers [...]
Active Directory environments are the backbone of countless organizations, and securing them is paramount. However, a significant new threat has emerged that exploits a subtle [...]
Imagine a scenario where an unauthenticated attacker, without needing any login credentials, could seamlessly step into the shoes of any employee within your organization’s [...]
A fundamental expectation of any operating system is its ability to power down reliably. Yet, a recent security update for Windows 11 has introduced a [...]
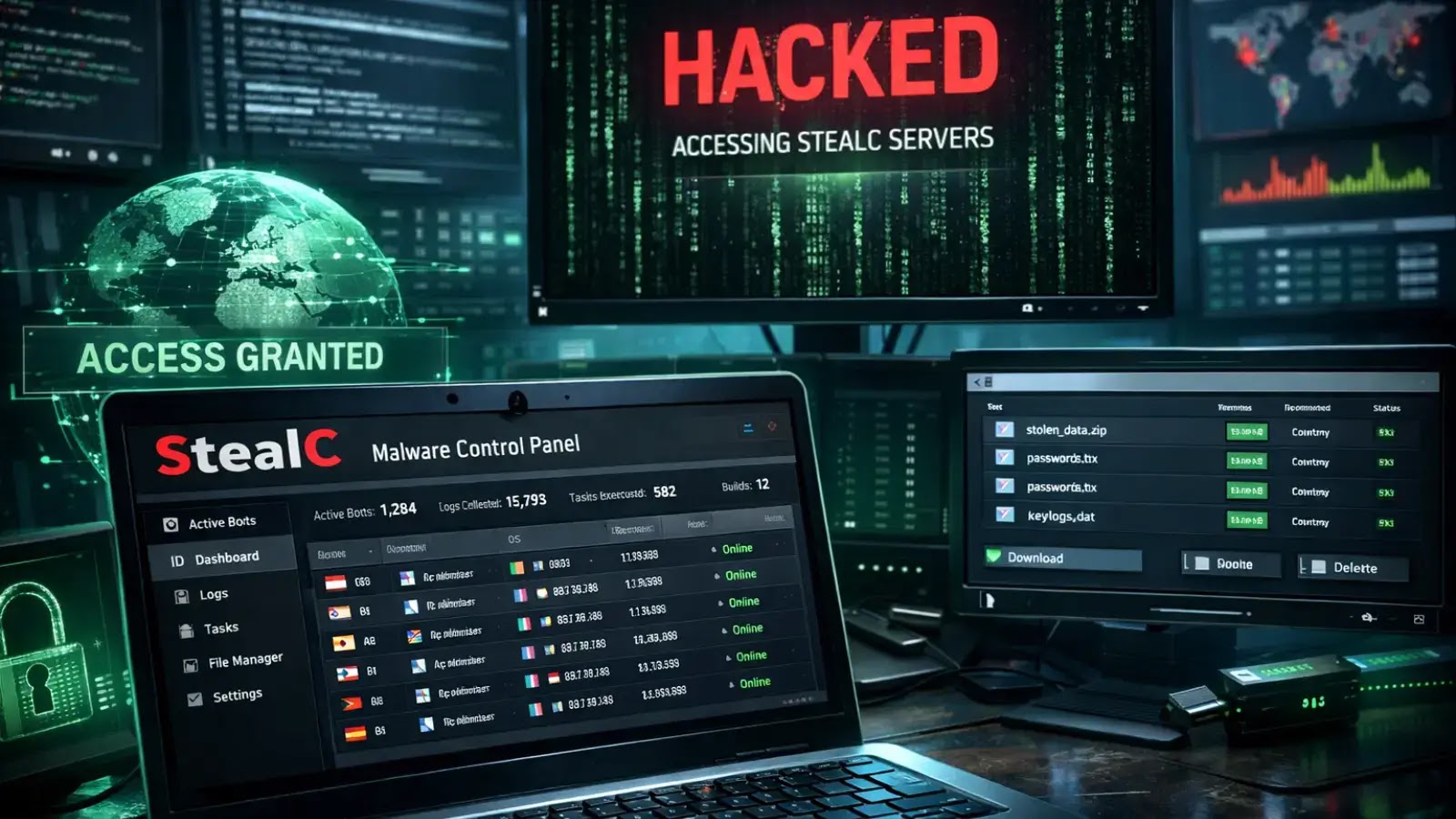
Unmasking the Threat: Researchers Infiltrate StealC Malware C2 Infrastructure In a significant win for cybersecurity, security researchers have successfully breached the command-and-control (C2) infrastructure [...]
The landscape of cloud security is constantly shifting, presenting new challenges even within highly sophisticated platforms. A recent disclosure by XM Cyber researchers has brought [...]