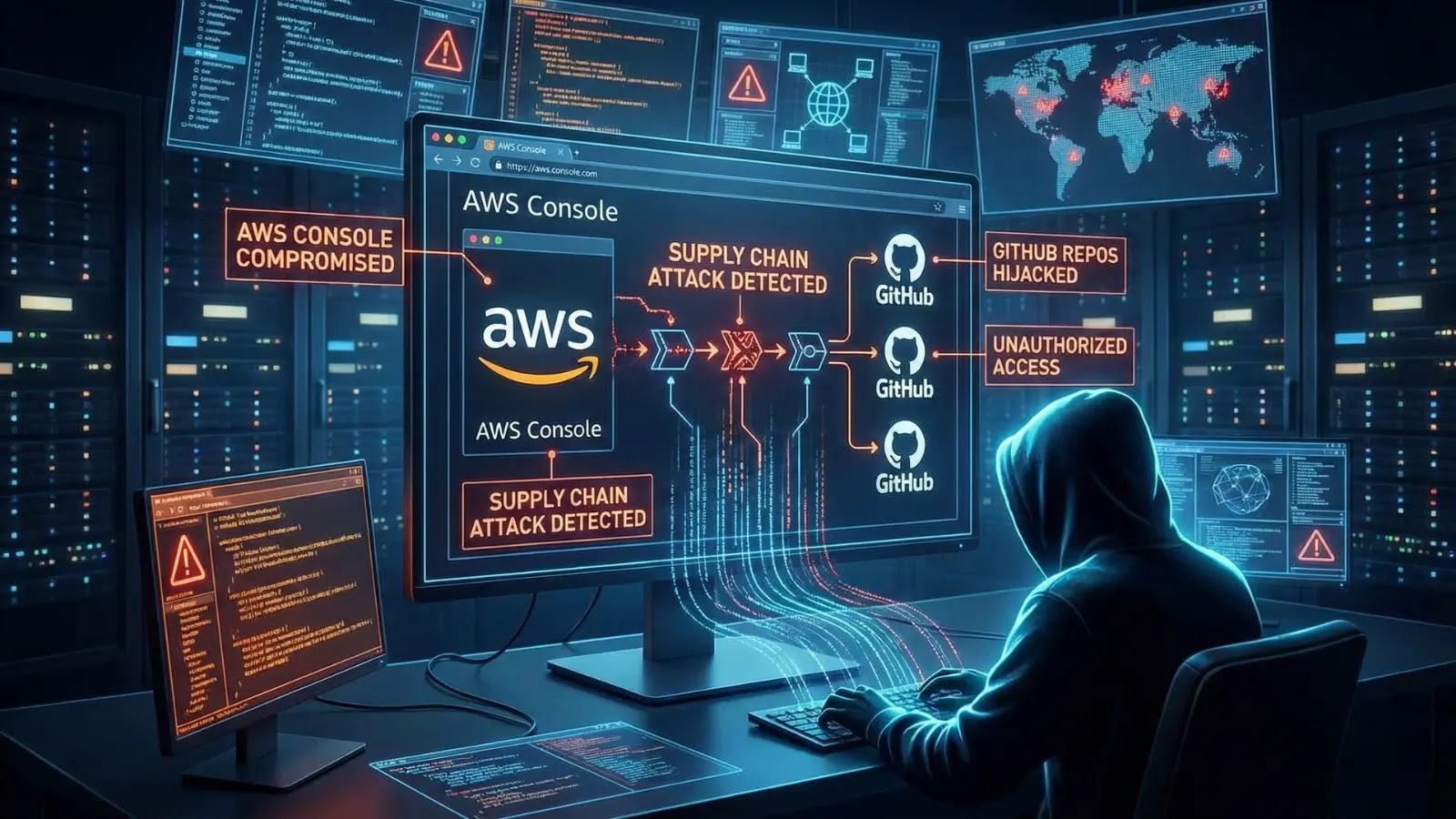
Unpacking the AWS Console Supply Chain Attack: A Deep Dive into Compromised GitHub Repositories The digital supply chain is a ubiquitous yet often underestimated [...]
Betterment Breach: A Deep Dive into Sophisticated Social Engineering The digital age, for all its convenience, consistently reminds us of its inherent vulnerabilities. Recently, [...]
The relentless cat-and-mouse game between cyber attackers and defenders has never been more intense. As threats evolve, so too must our strategies for both [...]
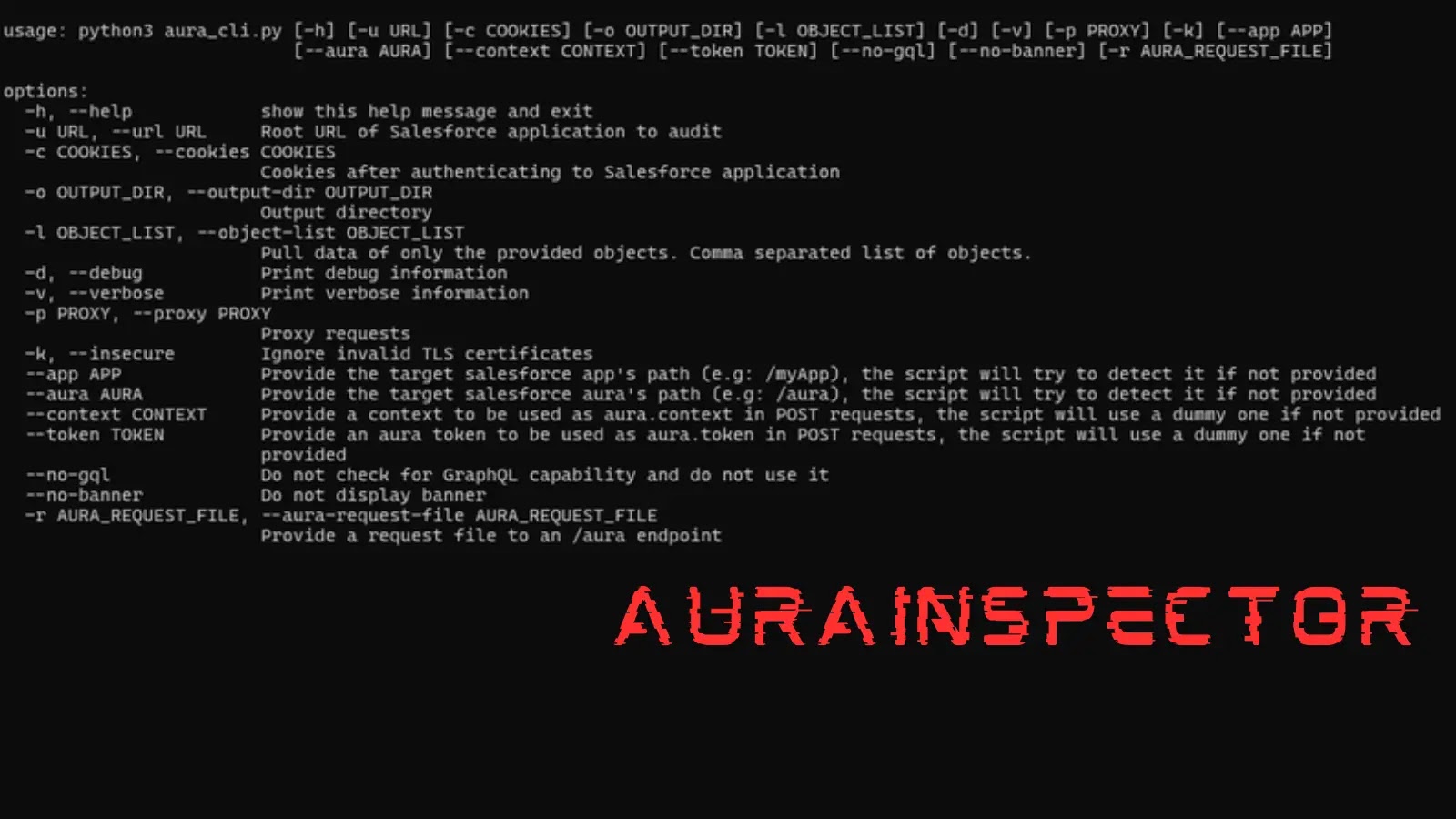
Unmasking Hidden Threats: Introducing AuraAudit for Salesforce Security In the expansive and often complex landscape of enterprise cloud solutions, Salesforce stands as a foundational [...]
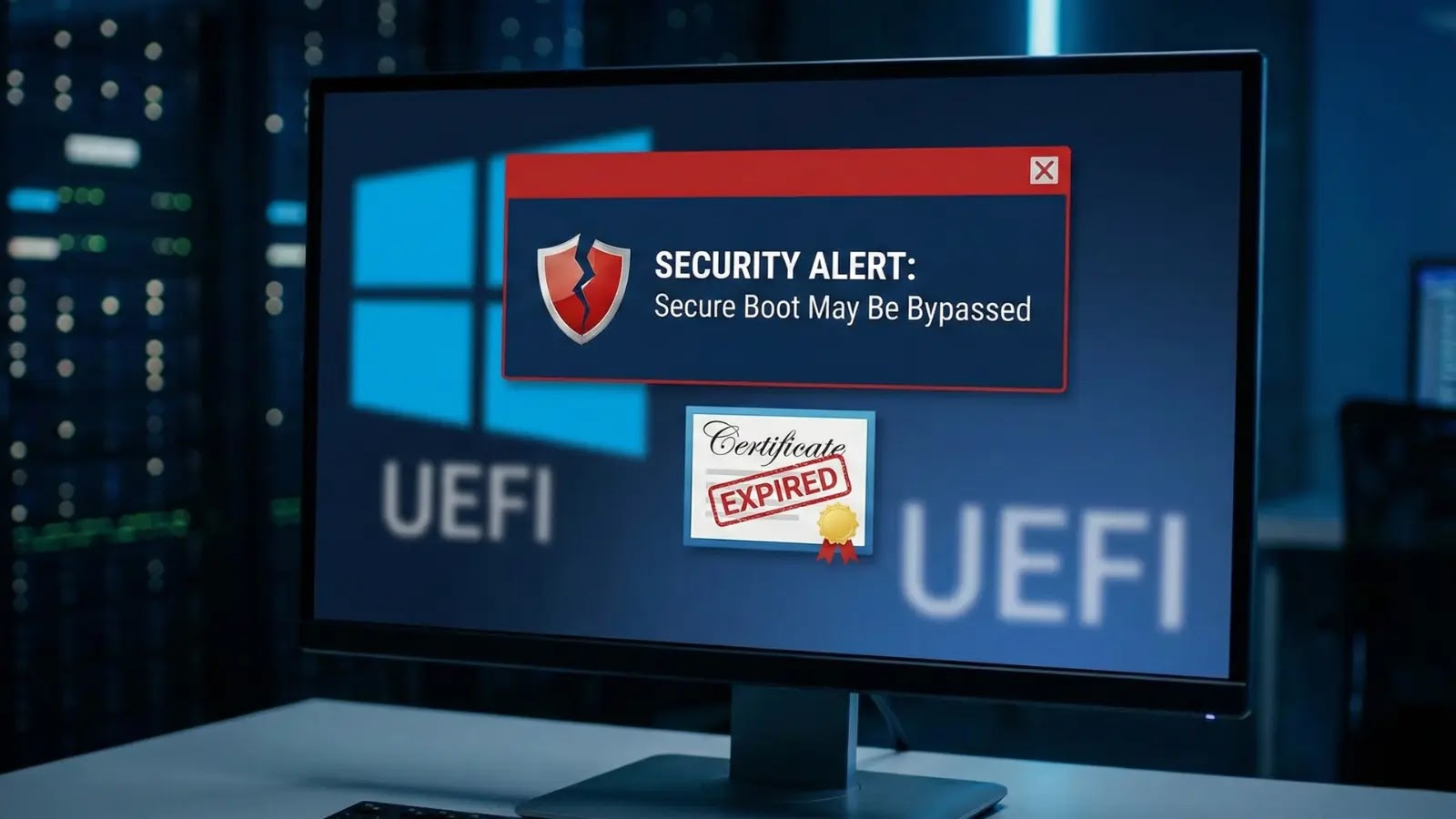
A silent threat has emerged from the foundational layers of Windows security, threatening the integrity of countless systems. Microsoft has issued a critical warning [...]
In the relentlessly evolving landscape of cyber warfare, threat actors continually refine their tactics, blurring the lines between humanitarian aid and malicious intent. A [...]
Discord Users Under Attack: VVS Stealer Targets Credentials and Tokens The digital landscape often mirrors a constant battleground, and for millions of Discord users, [...]
The Unseen Threat: Why Third-Party Vulnerabilities Are Forcing a Security Modernization Sprint The digital landscape is a complex tapestry woven from interconnected systems, applications, and [...]
Unpacking the Critical FortiSIEM Vulnerability: A Deep Dive into CVE-2025-64155 The cybersecurity landscape is constantly shifting, with new threats emerging that demand immediate attention [...]
Ransomware has long been a formidable threat, but a new, insidious twist is emerging that amplifies its danger: the integration of Large Language Models [...]