Ransomware has long been a formidable threat, but a new, insidious twist is emerging that amplifies its danger: the integration of Large Language Models [...]
Unmasking the “Contagious Interview”: North Korea’s Latest Code-Abuse Cyber Espionage The digital battlefield is constantly shifting, and North Korean threat actors are once again [...]
The digital landscape is a constant battleground, where the convenience of cutting-edge technology often walks hand-in-hand with unforeseen security risks. Microsoft Copilot, an AI assistant [...]
Unmasking DragonForce: A Deep Dive into the Latest Ransomware Threat and Its Decryptor The digital landscape is a constant battlefield, and emerging ransomware operations [...]
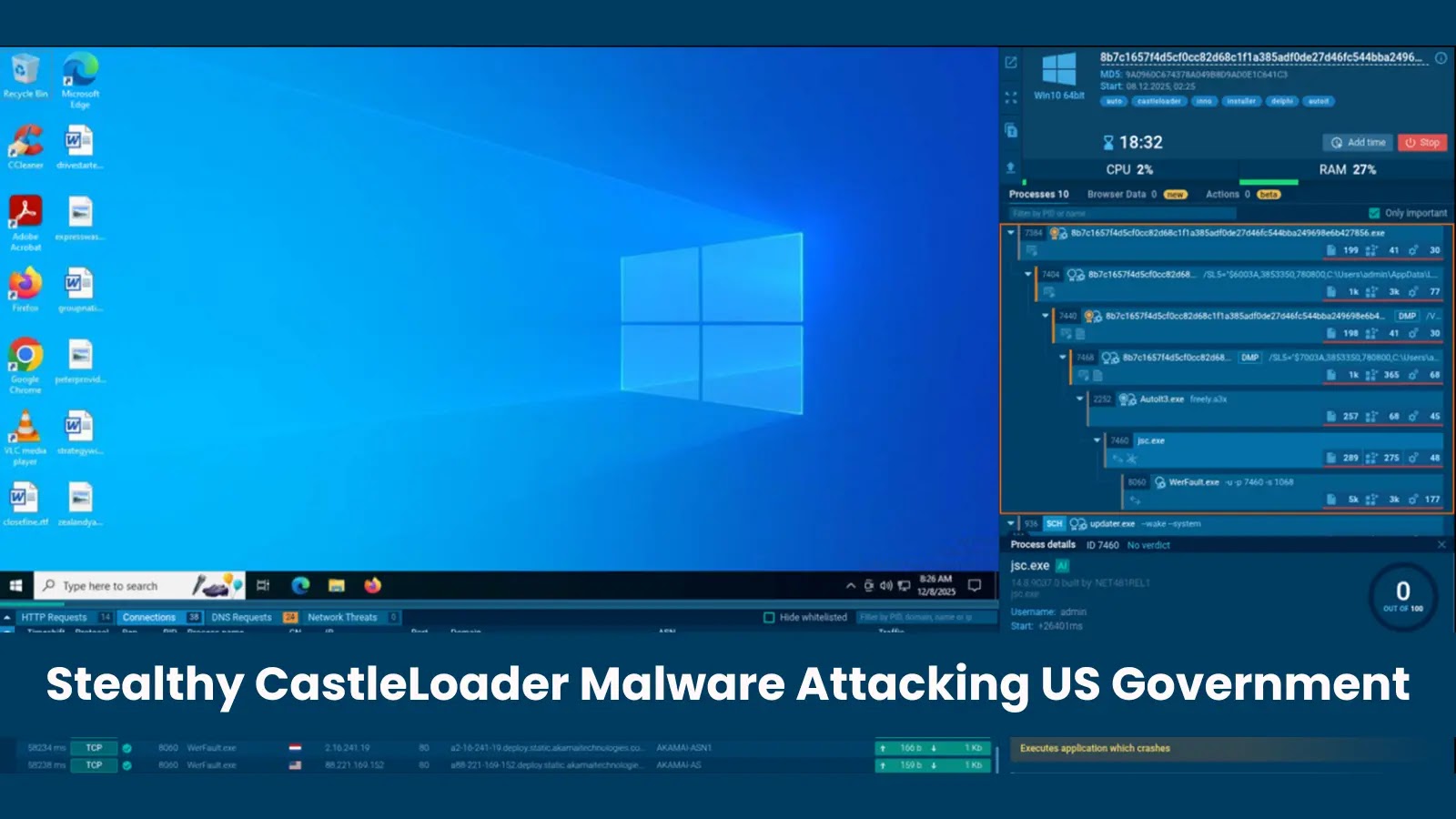
Stealthy CastleLoader Malware: An Evolving Threat to US Government and Critical Infrastructure The cybersecurity landscape has recently witnessed the emergence of a highly sophisticated [...]
A significant security flaw has recently come to light in Microsoft SQL Server, posing a substantial risk to organizations leveraging this widely used database [...]
Palo Alto Networks Firewall Vulnerability: A Critical Threat to GlobalProtect Services In the intricate landscape of network security, the integrity of your firewall infrastructure [...]
The digital threat landscape is perpetually shifting, and recent intelligence highlights a deeply concerning development: Chinese threat actors have established a colossal network of over [...]
In the interconnected landscape of modern networking, the security of infrastructure devices is paramount. A recent disclosure by Hewlett Packard Enterprise (HPE) has cast a [...]
A severe security alert has recently impacted the WordPress ecosystem, specifically targeting installations utilizing the Modular DS plugin. A critical unauthenticated privilege escalation vulnerability, [...]