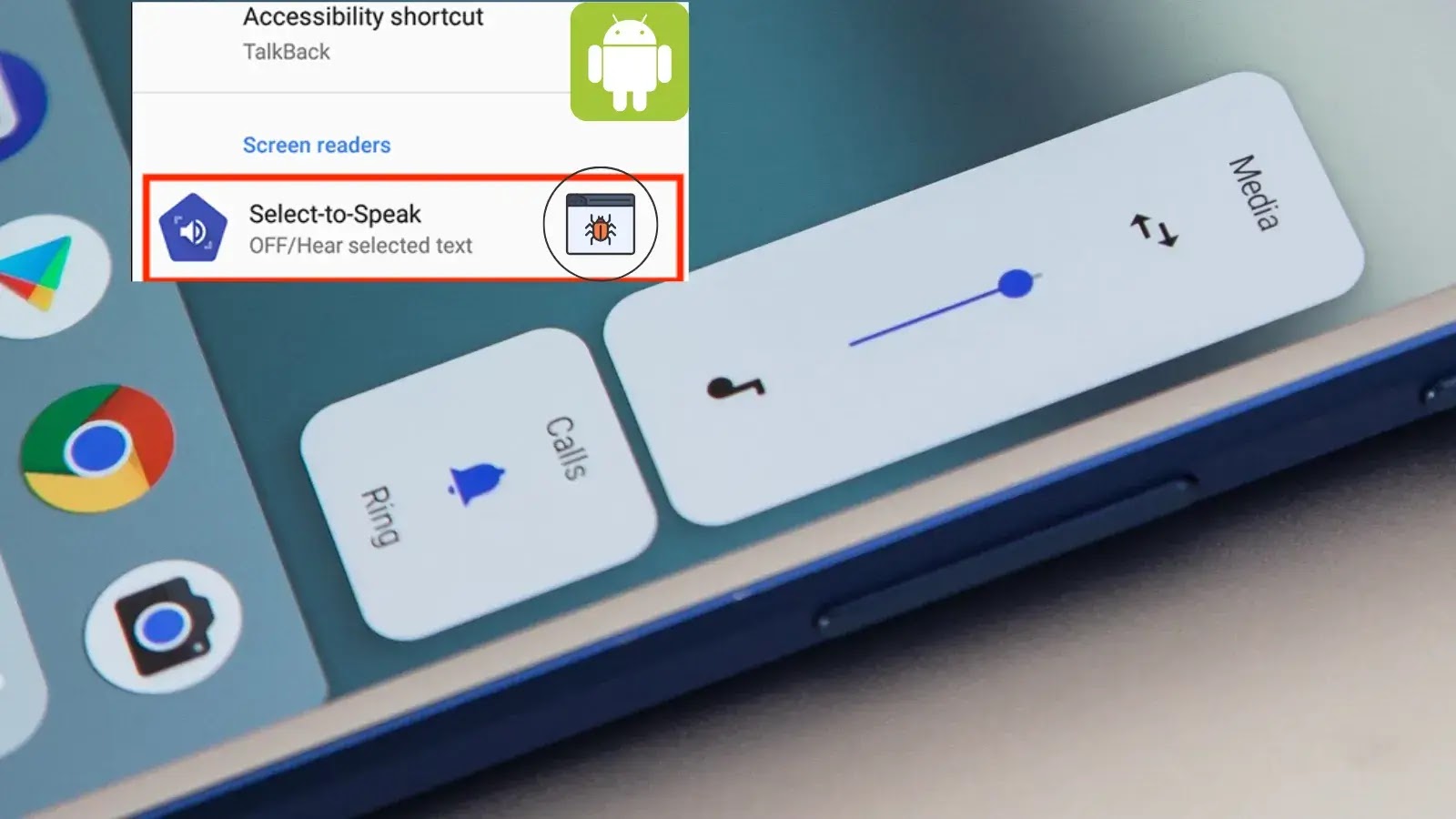
A recently identified critical bug affects Android devices, specifically impacting the functionality of volume buttons when the “Select to Speak” accessibility feature is enabled. This [...]
The digital storefronts we rely on for everything from groceries to gadgets face a persistent and evolving threat: web skimming. A new variant of this [...]
The eCommerce landscape is a digital goldmine, but for every legitimate transaction, there’s a cyber threat lurking. With the sector’s explosive growth, the necessity for [...]
Navigating the Evolving Landscape of Financial Data Security in 2026 The financial services sector operates at the nexus of trust and vulnerability. Handling vast [...]
The insurance industry, by its very nature, is a custodian of some of the most sensitive personal and financial data imaginable. From health records to [...]
Navigating the Cloud Security Landscape for Healthcare in 2026 The healthcare sector faces a unique and escalating challenge: safeguarding incredibly sensitive patient data within increasingly [...]
In the rapidly expanding landscape of enterprise IT, where cloud applications proliferate and user access demands escalate, Single Sign-On (SSO) has transitioned from a [...]
The landscape of cybersecurity is in perpetual motion, with threats evolving at an alarming pace. For organizations, staying ahead means not just reactive defense [...]
In the relentless landscape of cyber threats, robust defense mechanisms are not merely an advantage; they are an imperative. As organizations face an increasingly sophisticated [...]
Unveiling Digital Footprints: Top OSINT Tools for Pen Testers in 2026 In the evolving landscape of cybersecurity, thorough intelligence gathering is the bedrock of [...]