The landscape of digital communication is undergoing a significant transformation. With over 3 billion users relying on Gmail daily, any fundamental shift in its [...]
Unmasking the Threat: One-Click Telegram Flaw Exposes Real IP Addresses The digital landscape often promises anonymity, especially when users leverage tools like proxies to [...]
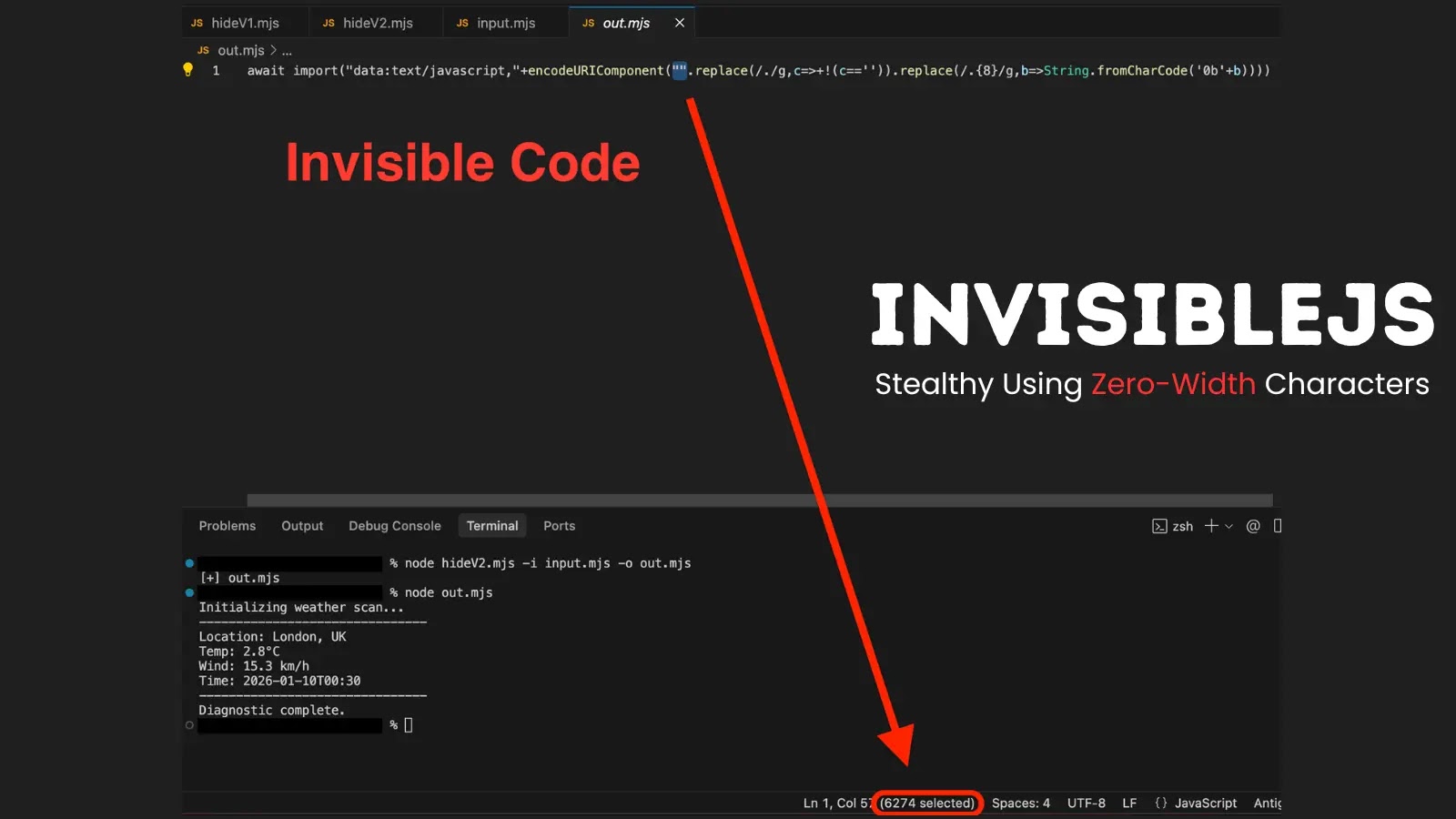
InvisibleJS: How Invisible Code Hides Dangerous Payloads in Plain Sight The digital landscape is constantly evolving, with new threats emerging that challenge conventional cybersecurity [...]
When Community Trust Turns Treacherous: The n8n npm Package Infiltration The digital supply chain, an increasingly interconnected web of software components and third-party integrations, [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Security Restriction Bypass Vulnerability in Microsoft Edge (Chromium-based) Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Veeam Backup & Replication Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Local File Inclusion / Path Traversal Vulnerability in jsPDF Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Red Hat JBoss Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Systems Affected JBoss [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Information Disclosure Vulnerability in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Systems Affected Cisco ISE [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Systems Affected Open Source Snort [...]