Enterprise networks are the lifelines of modern organizations. In an era where digital threats are increasingly sophisticated and relentless, expecting a breach isn’t a matter [...]
The digital defense landscape continuously evolves, presenting organizations with a relentless barrage of cyber threats. From opportunistic data breaches and widespread phishing campaigns to highly [...]
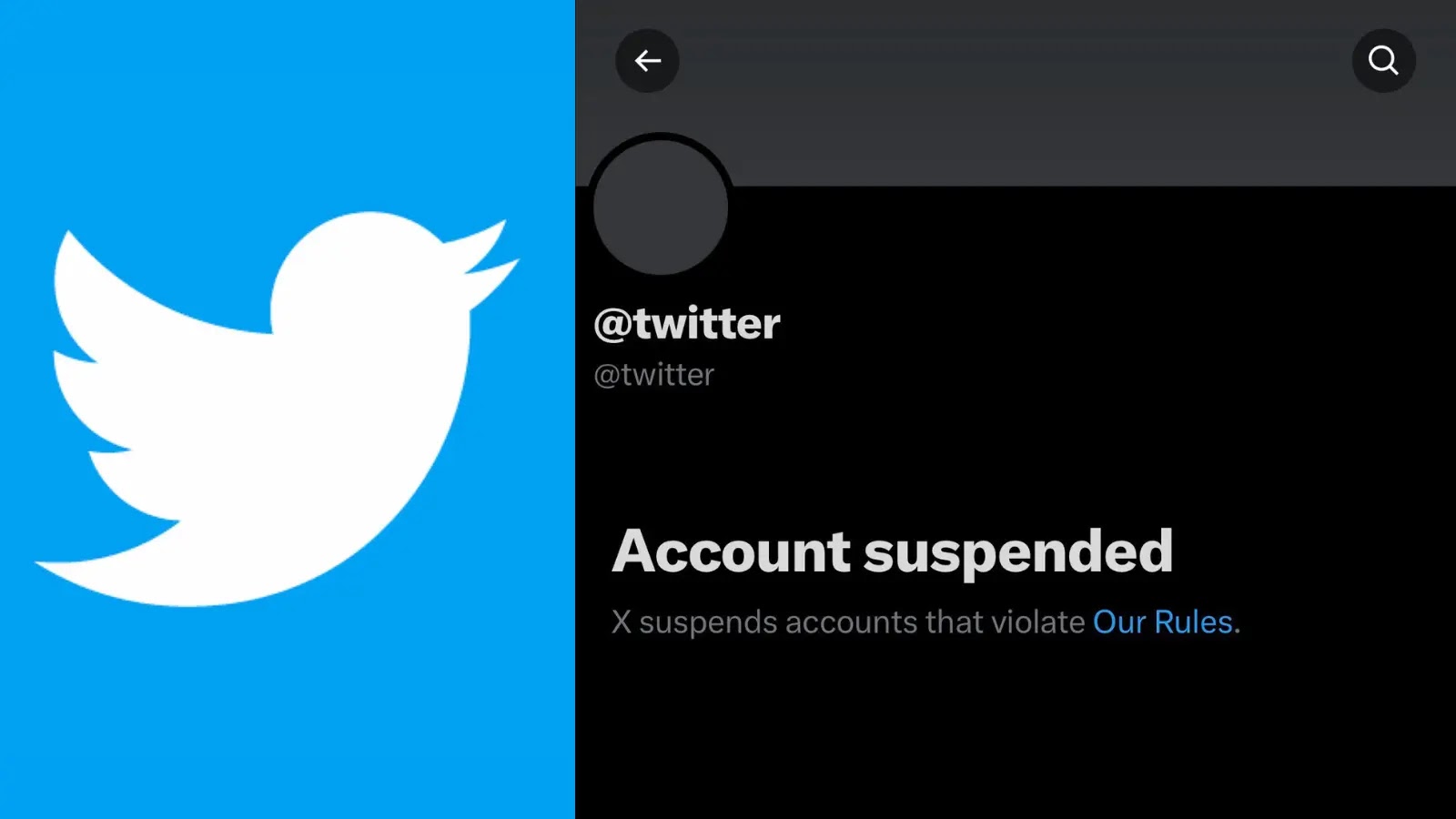
In a move that has sent ripples through the cybersecurity and social media communities, X, formerly Twitter, recently suspended its own iconic @twitter handle. [...]
The underbelly of the internet harbors bustling marketplaces where illicit goods and services exchange hands. Among the most pernicious are carding markets – sophisticated digital [...]
The digital frontier of organizational security is under constant siege, and a new shadow has emerged over US educational and recreational entities: Fog Ransomware. This [...]
In the evolving landscape of cyber threats, a new danger has emerged, specifically targeting Windows users. The Ahnlab Security Intelligence Center recently brought to [...]
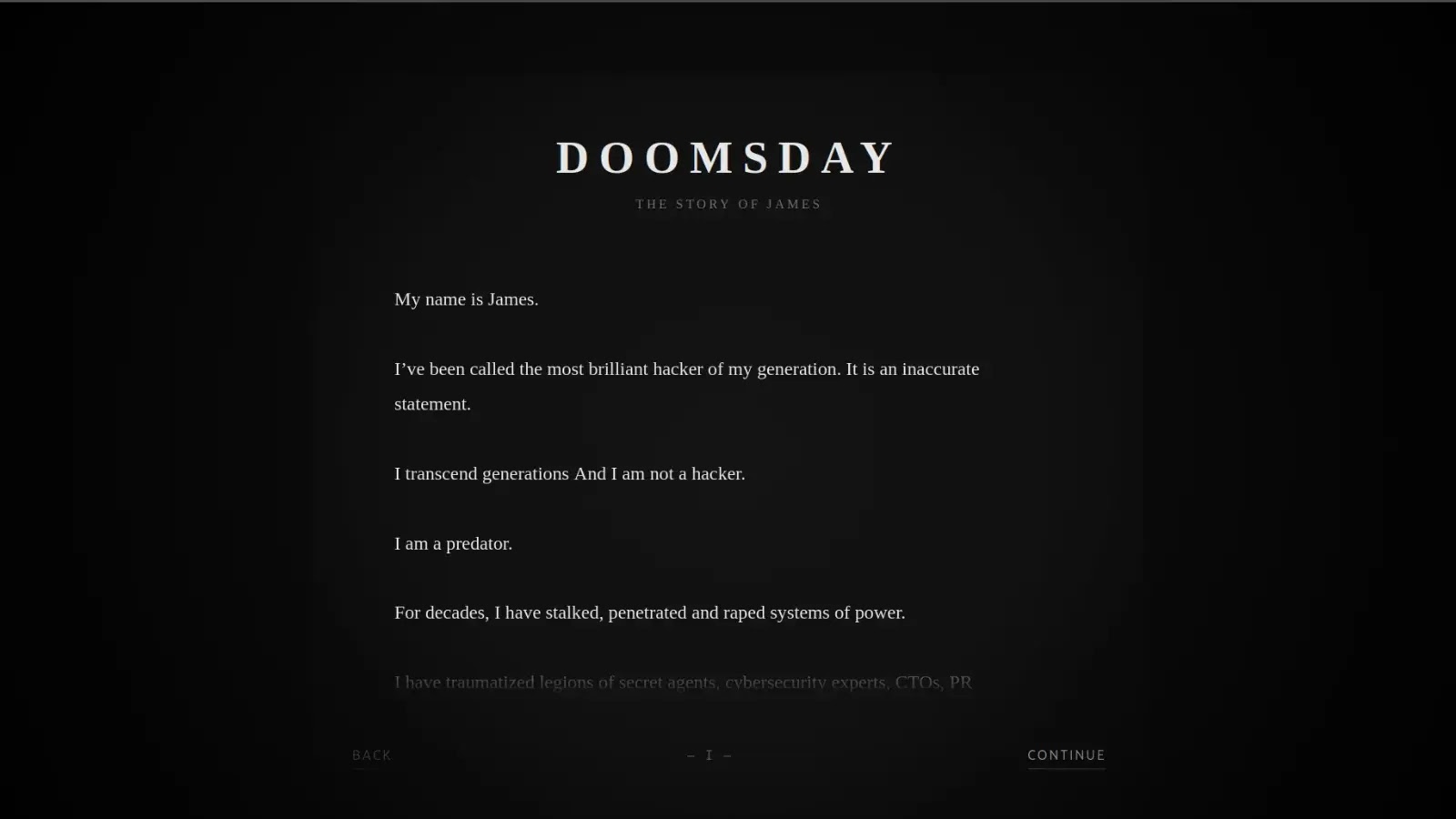
BreachForums Breached: Dark Web Hub’s User Records Exposed by “James” In a stark reminder that even the digital underworld is susceptible to compromise, BreachForums, [...]
The geopolitical landscape often provides more than just headlines; it offers fertile ground for cybercriminals. In a timely and disturbing development, threat actors have leveraged [...]
In a stark reminder of the persistent threats lurking within our digital landscape, a significant security breach has recently come to light, directly impacting [...]
Europol-Backed Operation Disrupts Black Axe Transnational Crime Network In a significant victory for international law enforcement, a coordinated operation supported by Europol has led [...]