Europol-Backed Operation Disrupts Black Axe Transnational Crime Network In a significant victory for international law enforcement, a coordinated operation supported by Europol has led [...]
MacSync’s Evolution: A New Threat Bypassing macOS Gatekeeper with Signed Applications In the dynamic landscape of macOS threats, a new variant of the MacSync [...]
Texas Gas Station Operator Suffers Data Breach: 377,000+ Customers Affected A recent cybersecurity incident has cast a concerning shadow over the personal data of [...]
Recent reports of Instagram users receiving unsolicited password reset emails sparked widespread concern and speculation about a potential large-scale data breach. In an era [...]
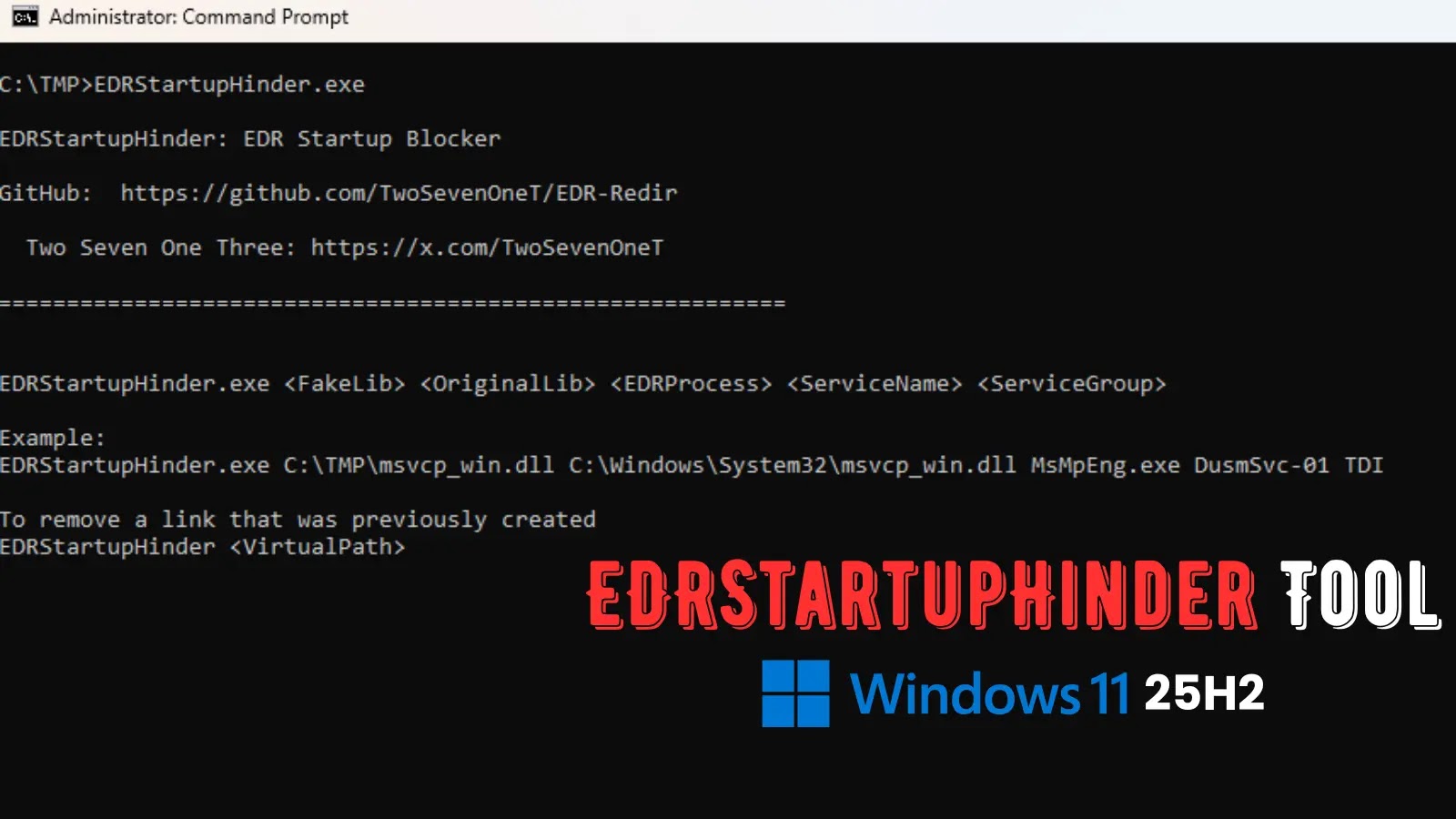
EDRStartupHinder: A New Threat Disables Antivirus at Windows Startup The landscape of endpoint security is constantly shifting, with adversaries developing new methods to evade [...]
The digital underworld is constantly innovating, and a disturbing new trend has emerged that significantly lowers the barrier to entry for criminals seeking to [...]
The Evolving Threat Landscape: Over 240 Exploits Before Ransomware The landscape of cyber threats is in constant flux, with threat actors continuously refining their tactics [...]
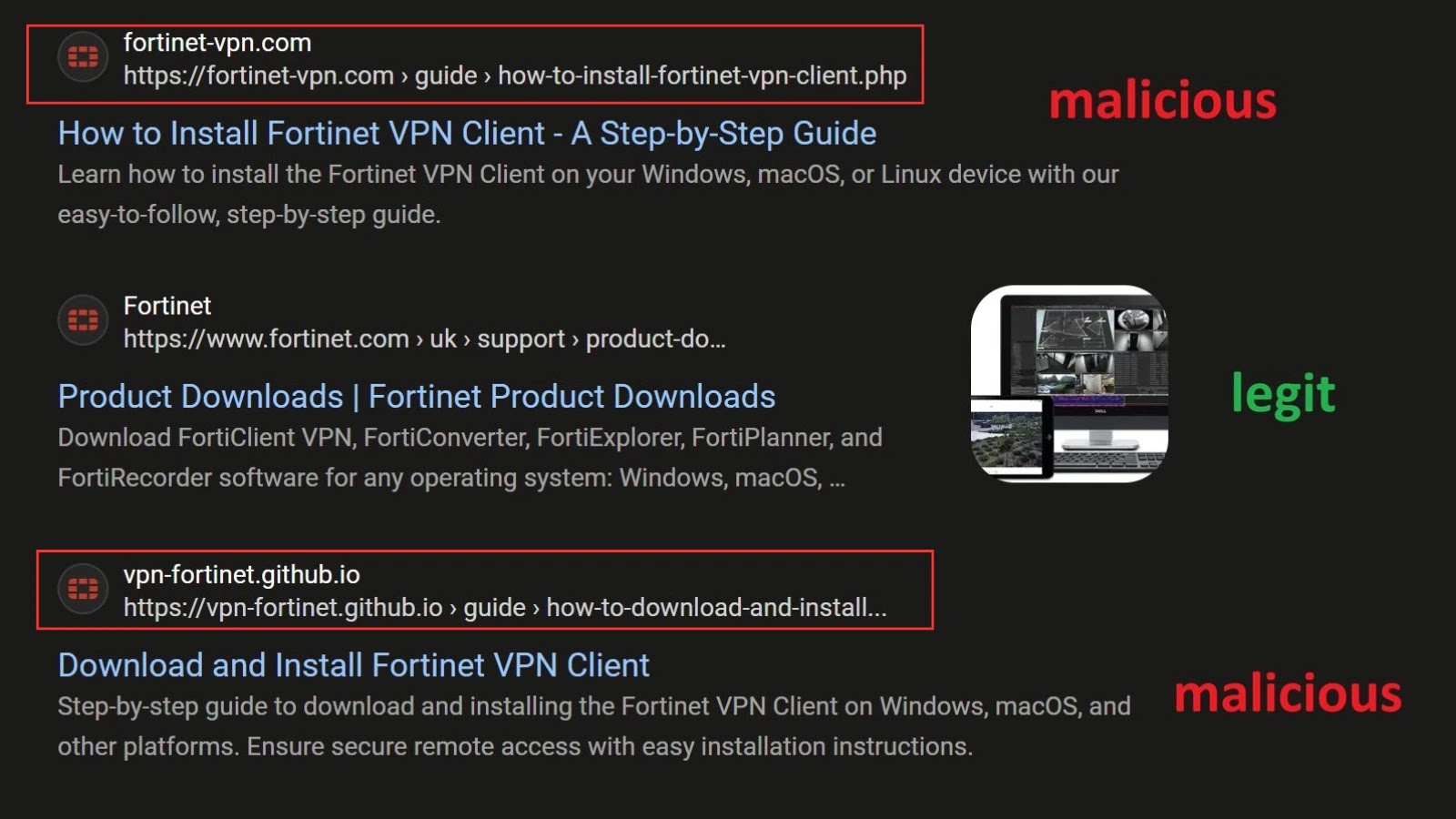
The digital frontier demands constant vigilance, especially when it comes to the tools safeguarding our remote access. A cunning new phishing campaign has emerged, directly [...]
The Escalating Threat Landscape: Initial Access Brokers Fueling Ransomware in Australia and New Zealand The digital defenses of Australia and New Zealand are under unprecedented [...]
The digital landscape is a constant battleground, where legitimate tools are frequently weaponized by malicious actors. A concerning new threat has emerged, exploiting the widespread [...]