—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Command Injection Vulnerability in D-Link DSL Routers Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Systems Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Google ChromeOS Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Google ChromeOS [...]
Organizations worldwide rely on robust endpoint protection and centralized security management platforms to defend against increasingly sophisticated cyber threats. Trend Micro Apex Central is [...]
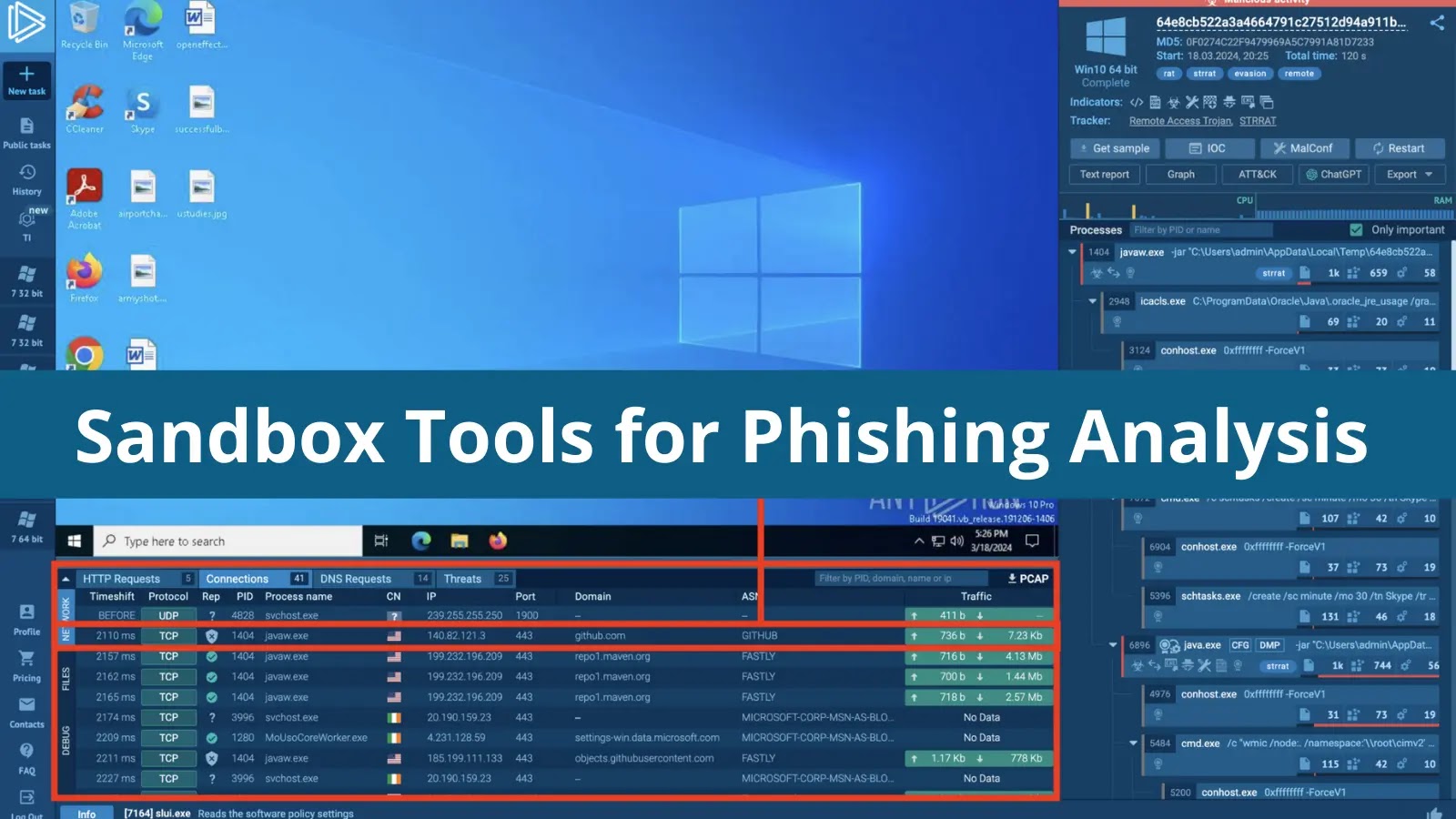
Navigating the Phishing Frontier: Essential Sandbox Tools for 2026 Phishing attacks continue to evolve in sophistication, bypassing traditional defenses and posing significant threats to [...]
Unveiling Email Security Gaps: Why SMTP Testing Matters More Than Ever in 2026 Email remains a cornerstone of digital communication, but its underlying infrastructure, [...]
Navigating the Automated Storm: Why Bot Protection is Non-Negotiable in 2026 The digital landscape of 2026 presents an undeniable truth: automated bot attacks have [...]
Vulnerability scanning underpins any robust cybersecurity strategy. It’s the critical process of pinpointing and patching flaws before their exploitation leads to devastating breaches. For organizations [...]
Securing Your Wireless Perimeter: Why Automatic WiFi Security is Non-Negotiable in 2026 The digital landscape of 2026 presents an increasingly complex threat environment, particularly [...]
Critical OWASP CRS Vulnerability Exposes Web Applications to Charset Bypass Attacks In a significant development for web application security, a critical vulnerability within the [...]
For CISOs, CTOs, and IT Managers, the landscape of technology management is increasingly complex. The demand for robust, scalable, and secure IT infrastructure, coupled [...]