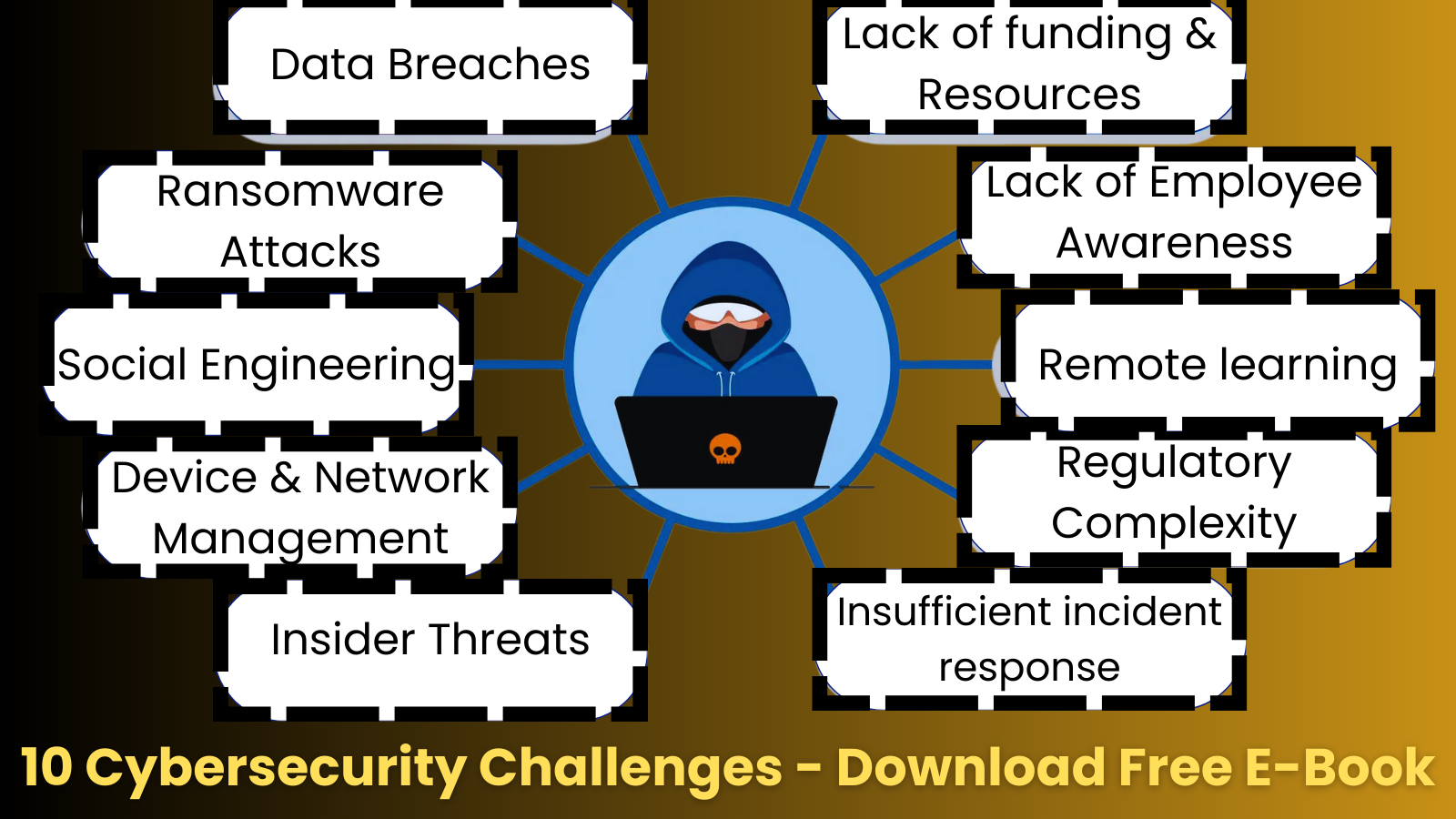
Securing Our Students: How U.S. K-12 Schools Can Conquer Top Cybersecurity Challenges The digital landscape of U.S. K-12 education is a complex and often perilous [...]
A disturbing new strain of malware, dubbed “Boto Cor-de-Rosa,” has surfaced, presenting a significant threat to Windows users, particularly those engaging with WhatsApp Web. This [...]
A critical security vulnerability has been uncovered within the Undertow HTTP server core, a pervasive component in numerous Java applications, including WildFly and JBoss [...]
Imagine this: You’re a responsible IT professional, using a legitimate, widely-recognized open-source tool for system activation, only to have your flagship security solution flag it [...]
Unmasking Ghost Tapped: A New Android Threat Exploiting NFC The digital landscape is constantly shifting, with threat actors continuously innovating new methods to compromise [...]
The AI Frontier: Under Attack and Exposed The promise of Artificial Intelligence (AI) has rapidly transformed industries, bringing unparalleled efficiency and innovation. Yet, this [...]
A severe pre-authentication remote code execution (RCE) vulnerability, identified as CVE-2025-52691, has sent ripples through the cybersecurity community. This critical flaw, discovered in SmarterTools’ [...]
Imagine your critical network infrastructure grinding to a halt, not due to a sophisticated cyberattack, but a fundamental service within your essential network hardware. This [...]
A significant security flaw has recently surfaced in Cisco’s Identity Services Engine (ISE), a critical component for network access control in many organizations. This vulnerability [...]
Network security is a constant battle, and even our most trusted detection engines can harbor hidden vulnerabilities. Recently, critical weaknesses surfaced within Cisco’s Snort [...]