The Silent Sabotage: How Stolen Data Can Corrupt AI Models The integrity of Artificial Intelligence (AI) models is paramount. From critical infrastructure management to [...]
The landscape of cyber threats continues to evolve at an alarming pace, with threat actors constantly devising novel methods to compromise digital security. A [...]
Urgent Alert: Proof-of-Concept Exploit Released for Critical Android/Linux Kernel Vulnerability CVE-2025-38352 The cybersecurity landscape has been significantly impacted by the public release of a Proof-of-Concept [...]
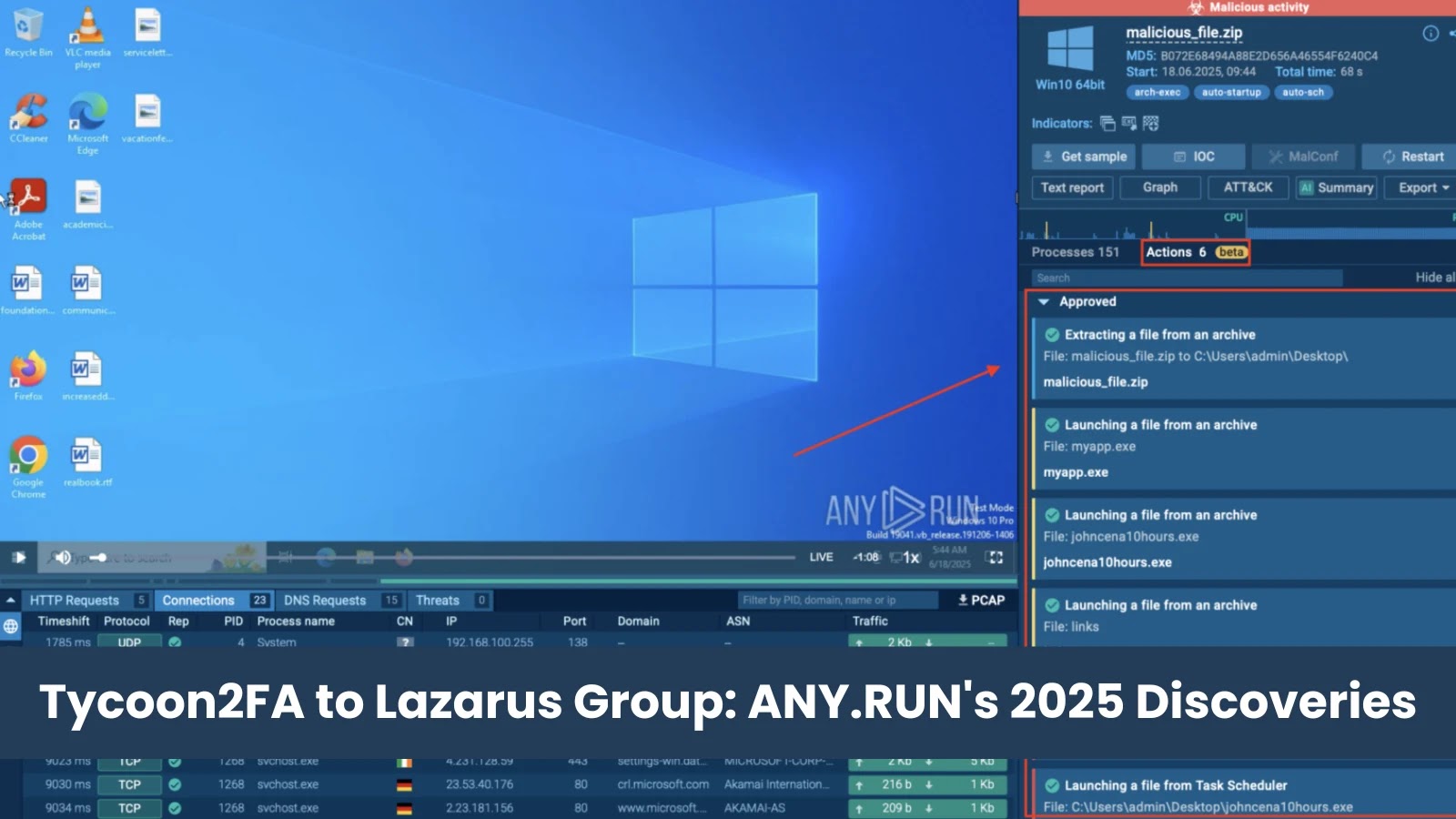
Unveiling 2025’s Cyber Landscape: ANY.RUN’s Definitive Impact The digital realm is a constant battleground, where new threats emerge with alarming speed. For cybersecurity professionals, [...]
The silent, relentless hum of Linux servers underpins much of the internet’s infrastructure. From hosting websites to managing critical databases, these machines are powerhouses. [...]
ownCloud Users Urged to Strengthen Security with MFA After Credential Theft Incidents The digital landscape demands robust security measures, and sometimes, the most effective [...]
The Relentless Pursuit: CrazyHunter Ransomware’s Attack on Healthcare The healthcare sector, a bedrock of societal well-being, finds itself under relentless siege from a new [...]
In the relentless battle against sophisticated cyber threats, a new adversary has emerged, casting a shadow over our digital landscape. A potent Windows packer, [...]
In the relentless cat-and-mouse game of cybersecurity, attackers constantly innovate, finding new ways to exploit trusted mechanisms. A recent and particularly insidious phishing campaign has [...]
The digital frontier is under constant siege, and a new, sophisticated threat has emerged, targeting the foundational infrastructure of many organizations: VMware ESXi instances. [...]