In the relentlessly evolving landscape of cyber threats, businesses, particularly small to medium-sized enterprises (SMBs), face a constant barrage of sophisticated attacks. While individual security [...]
The rapid adoption of Infrastructure as Code (IaC) has revolutionized how organizations deploy and manage their cloud environments. Empowering teams with unprecedented automation and scalability, [...]
In the high-stakes world of cybersecurity, the integrity of Data Loss Prevention (DLP) solutions is paramount. These tools are the digital guardians of sensitive organizational [...]
A critical flaw in Google Chrome’s WebView component has necessitated an urgent security update, highlighting the persistent challenges in maintaining robust application security. This vulnerability, [...]
A silent, yet widespread digital threat is actively compromising systems across Central and Eastern Europe and beyond. The cybersecurity landscape has been rattled by [...]
The Holiday Phishing Onslaught: DocuSign Spoofing and Identity Theft Questionnaires The festive season, a time typically associated with cheer and goodwill, has unfortunately brought with [...]
Microsoft’s ambitious integration of artificial intelligence (AI) features into Windows 11 has certainly stirred the pot. While these new functionalities, like Copilot and Recall, promise [...]
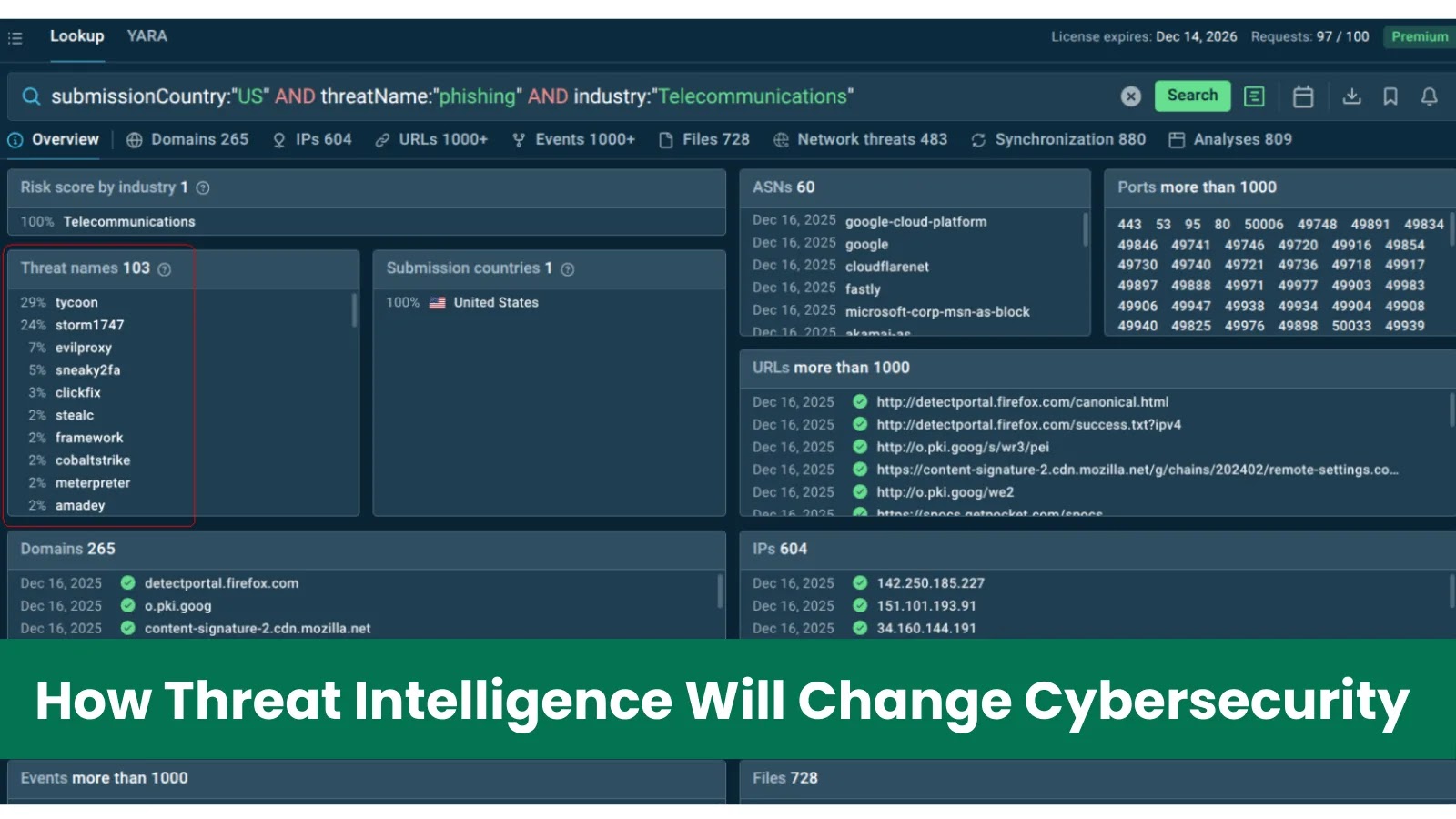
The Shifting Sands of Cyber Defense: How Threat Intelligence Will Redefine Cybersecurity by 2026 The cybersecurity landscape is in constant flux, a relentless battle [...]
NordVPN: Clearing the Air on Dark Web Data Breach Claims The digital shadows of the dark web frequently harbor unsubstantiated claims that can send [...]
Critical Dolby Codec Vulnerability Threatens Android Devices A significant security flaw has recently emerged, putting millions of Android devices at risk. Google’s January 2026 [...]