A silent threat is evolving, shifting its gaze towards new horizons. The nefarious GlassWorm malware, once primarily a concern for Windows environments, has undergone a [...]
The integrity of the cybersecurity profession hinges on trust and ethical conduct. When those entrusted with safeguarding digital assets betray that trust, it sends [...]
The landscape of cybersecurity continually evolves, pushing the boundaries of offensive and defensive strategies. As threats grow in sophistication, so too must the tools wielded [...]
The Looming Threat of AI-Enhanced Metamorphic Crypters The cybersecurity landscape perpetually reshapes itself, often driven by the relentless innovation of threat actors. A stark and [...]
Critical Apache StreamPipes Vulnerability: A Gateway to Admin Control A significant security flaw has recently come to light within Apache StreamPipes, a widely used data [...]
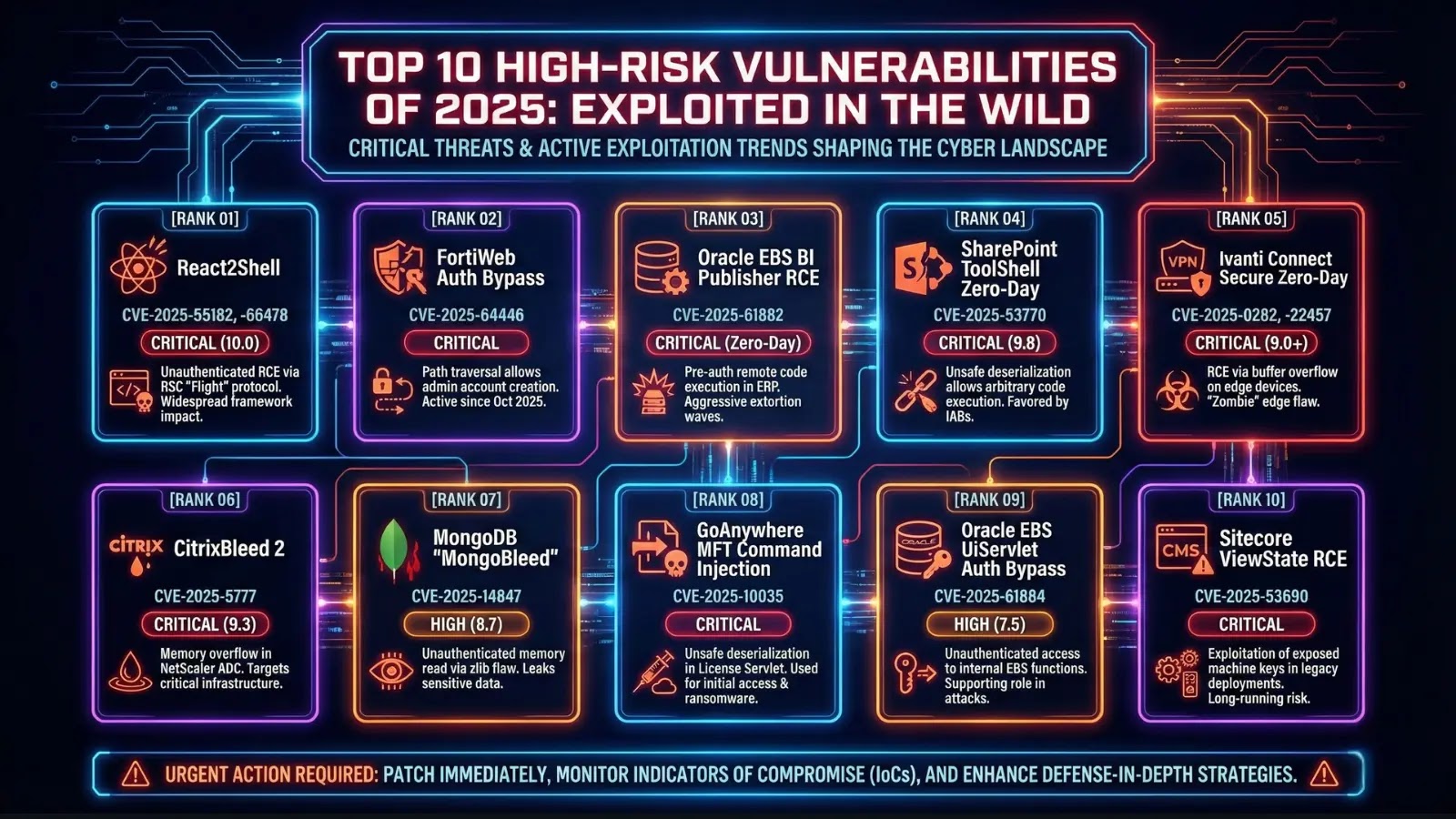
The cybersecurity landscape has always been a dynamic battleground, but 2025 has amplified this reality to unprecedented levels. With an astounding 21,500+ CVEs disclosed in [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Authentication Bypass Vulnerability in IBM API Connect Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
AdaptixC2 Unleashed: Bolstering Red Team Operations with Enhanced Stability and Speed In the dynamic realm of cybersecurity, penetration testers and red teams rely on robust [...]
Urgent Warning: Critical RCE Flaw in SmarterMail Demands Immediate Action A severe security vulnerability has been identified in SmarterMail, posing an existential threat to [...]
The digital battlefield is constantly evolving, with cyber adversaries employing increasingly sophisticated tactics to achieve their objectives. A recent and concerning development involves a Chinese-linked [...]