The Invisible Threat: How Indian Income Tax Scams Target Businesses The annual season for filing Income Tax Returns (ITR) in India brings with it a [...]
HardBit 4.0 Ransomware: A Deeper Dive into Open RDP and SMB Exploitation The landscape of cyber threats is perpetually shifting, and ransomware strains continue to [...]
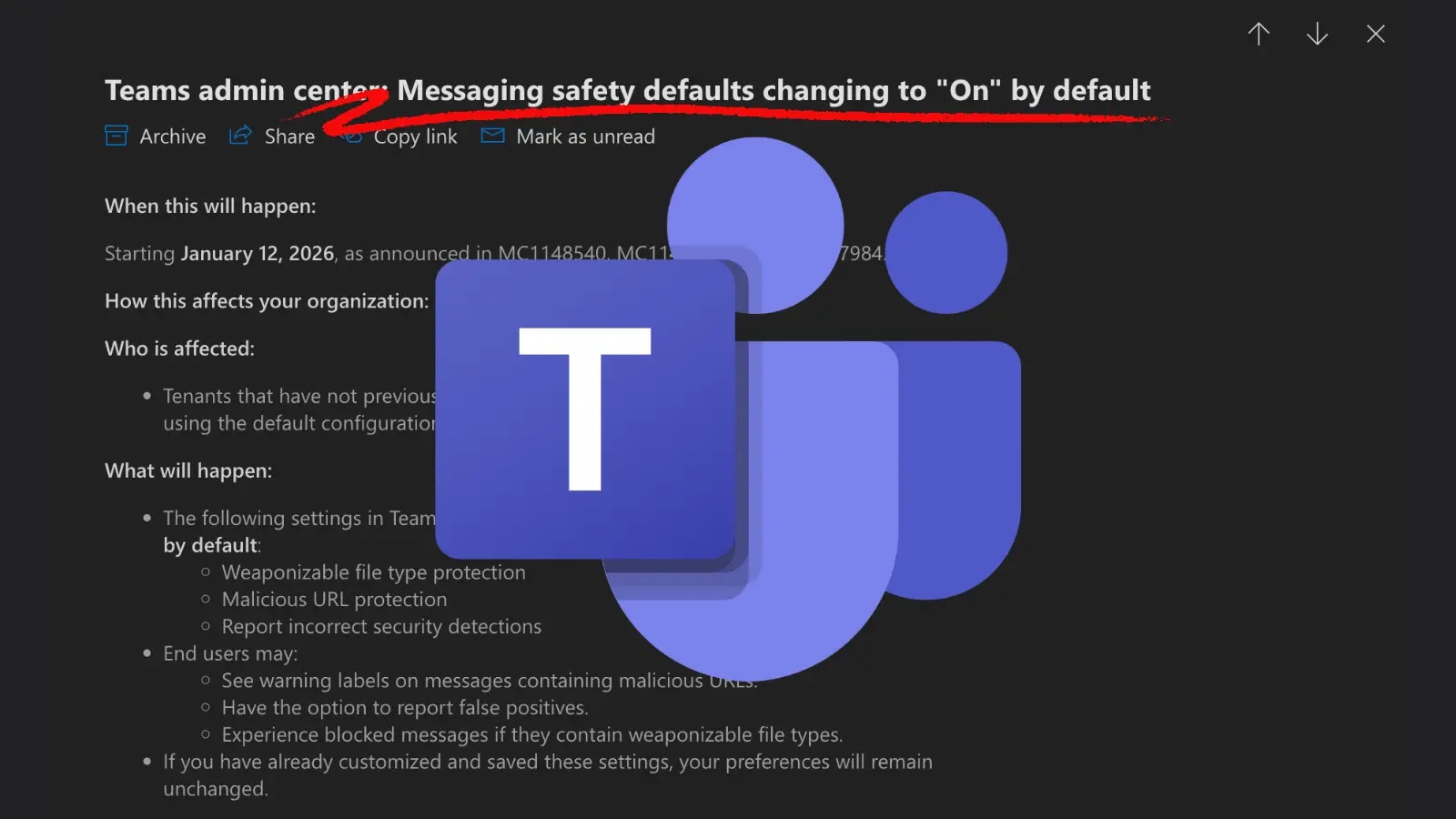
Microsoft Teams Fortifies Collaboration: What “Secure-by-Default” Means for You The digital workspace is constantly evolving, and with it, the threats that target our collaborative tools. [...]
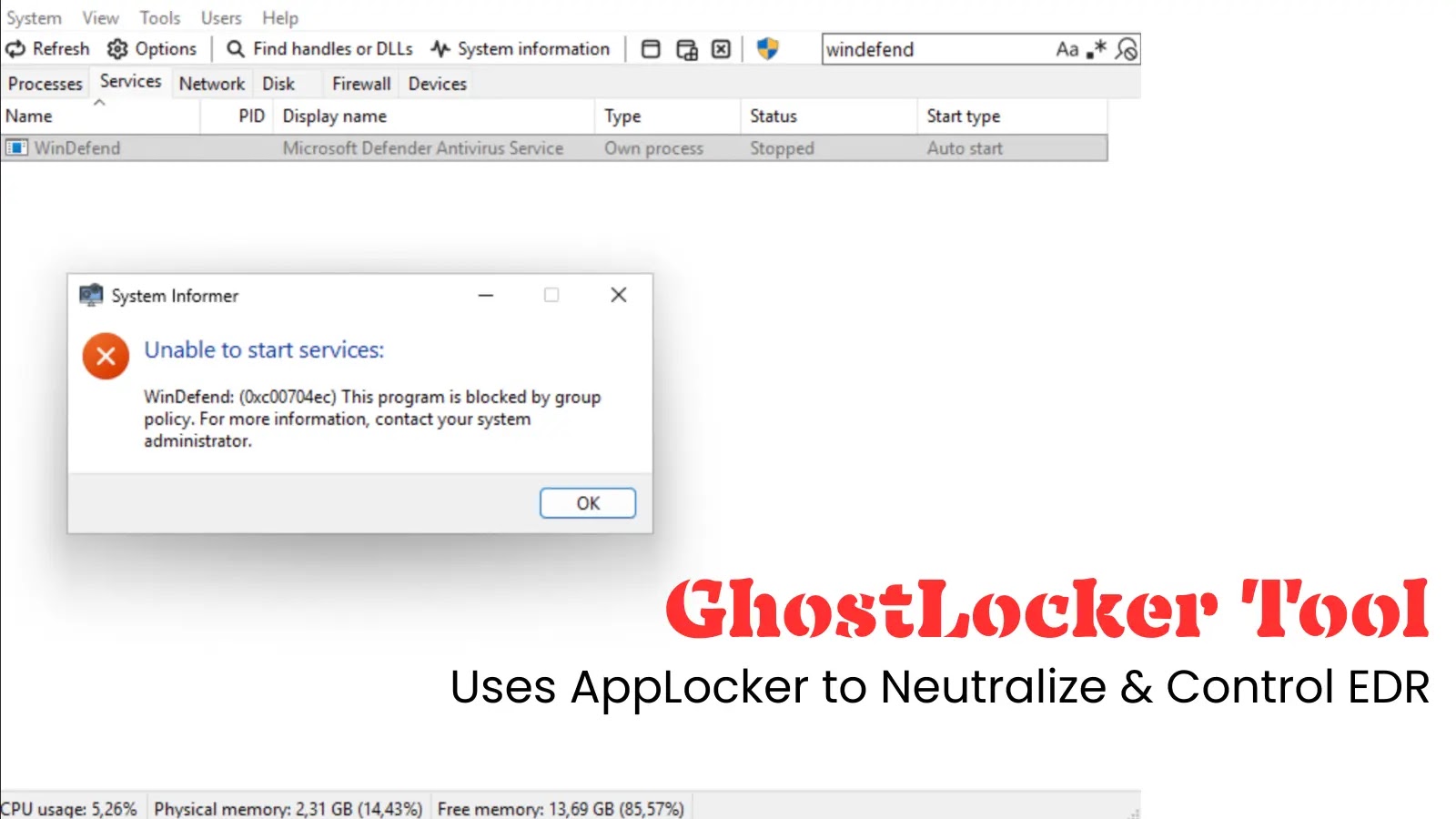
Endpoint Detection and Response (EDR) systems are the frontline guardians against sophisticated cyber threats. They promise to monitor, detect, and respond to malicious activities in [...]
The digital landscape consistently presents new challenges for cybersecurity professionals, and proactive defense is paramount. A recent development demanding immediate attention is the addition of [...]
Unmasking the Threat: Nezha Monitoring Tool Weaponized by Threat Actors The digital landscape is a constant battleground, and threat actors are perpetually refining their [...]
The digital landscape is a battleground, and threat actors constantly devise new ways to breach our defenses. A particularly insidious tactic has resurfaced: malicious Chrome [...]
Unmasking ClickFix: When Images Hide Information-Stealing Malware The digital threat landscape constantly shifts, with threat actors continuously refining their methods to bypass security measures and [...]
Spotify’s Music Library Scraped: An Unprecedented Challenge to Digital Archiving and Copyright The digital music landscape has been rattled by a recent, unprecedented event: [...]
The Silent Threat: Malicious NPM Package Steals WhatsApp Messages In a stark reminder of the persistent dangers lurking within open-source ecosystems, a highly deceptive [...]