CISA Sounds the Alarm: New BRICKSTORM Malware IOCs Demand Immediate Attention In the relentless landscape of cyber threats, staying ahead of sophisticated malware campaigns [...]
In the relentlessly evolving landscape of cyber threats, a new and particularly insidious campaign has emerged, directly targeting users of HubSpot, the widely adopted customer [...]
Microsoft Unveils Baseline Security Mode: A New Era for M365 Hardening In the expansive and increasingly complex landscape of cloud productivity, securing Microsoft 365 [...]
Unleashing AI Power: Claude Opus 4.5 Elevates GitHub Copilot Capabilities In the dynamic landscape of software development, artificial intelligence continues to reshape how we [...]
A recent critical alert has cybersecurity professionals on high alert: over 120 Cisco Secure Email Gateway and Cisco Secure Email and Web Manager devices [...]
Cybersecurity Weaknesses Exposed: PornHub Breach, Cisco 0-Day, and High-Stakes Geopolitical Espionage The digital landscape is a constant battlefield, and the past week offered a [...]
In the intricate world of cyber warfare, threat actors consistently adapt their methods, often leveraging legitimate tools to masquerade their malicious activities. A concerning trend [...]
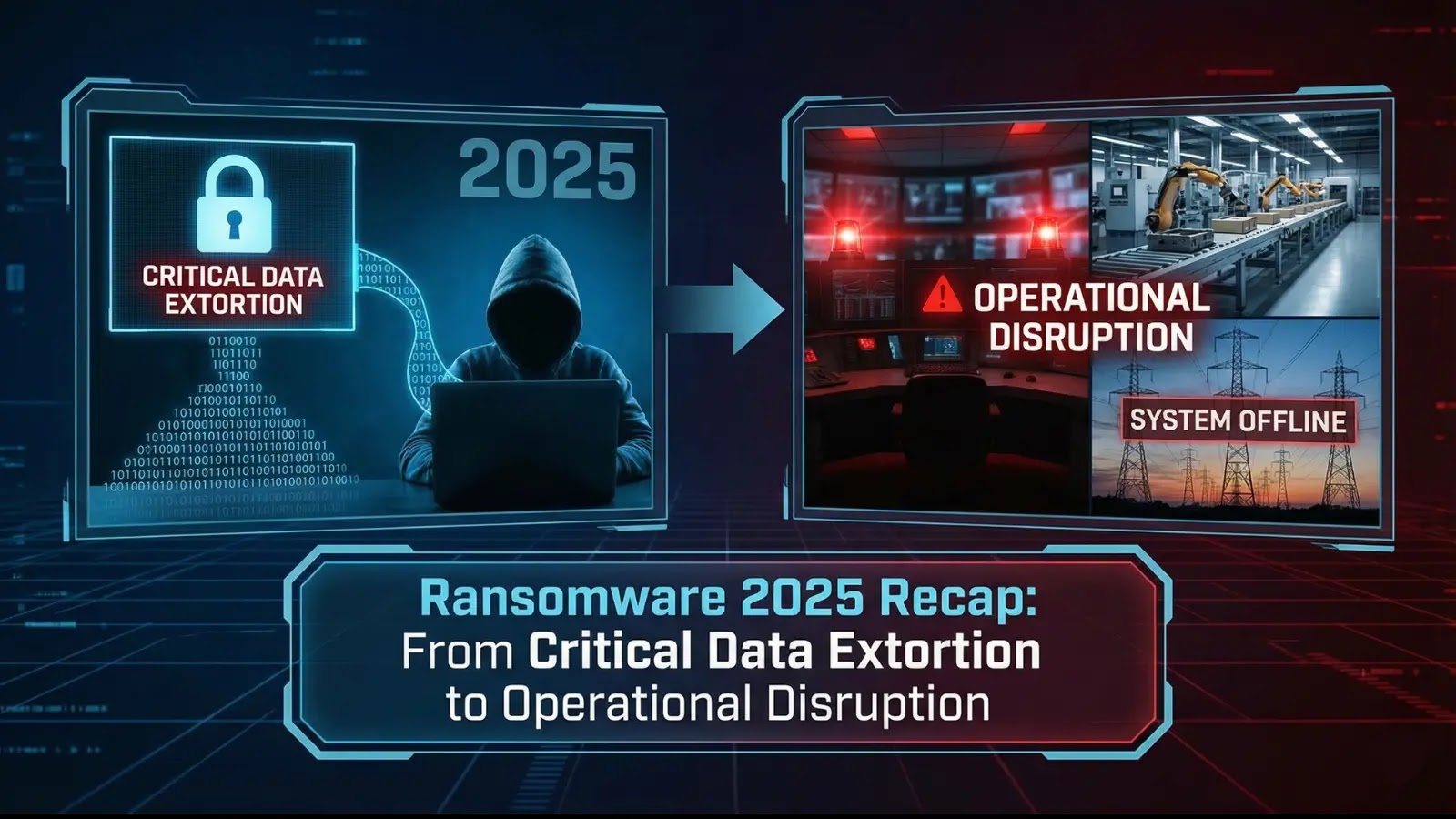
The digital battlefield of 2025 painted a stark picture of escalating cyber threats, particularly in the realm of ransomware attacks. What was once predominantly a [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 WhatsApp Account takeover campaign (GhostPairing) Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: High Description It has been [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Local Privilege Escalation Vulnerability in SonicWall SMA1000 Appliance Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Software [...]