IT infrastructure is the backbone of modern business, and when critical services falter, the impact can be severe. Recently, Microsoft confirmed a significant issue affecting [...]
A significant security flaw has recently surfaced, casting a shadow over the integrity of Windows operating systems. Microsoft has officially confirmed an out-of-bounds vulnerability [...]
The Connected Car: A New Battleground for Cybersecurity Modern vehicles are more than just modes of transport; they are sophisticated, interconnected devices that increasingly [...]
Every minute a Security Operations Center (SOC) analyst spends deliberating during incident triage is a minute the organization remains vulnerable. When the true nature [...]
A disturbing new development has emerged from the shadowy world of advanced persistent threats. Operation ForumTrol, a group known for its sophisticated cyber operations, has [...]
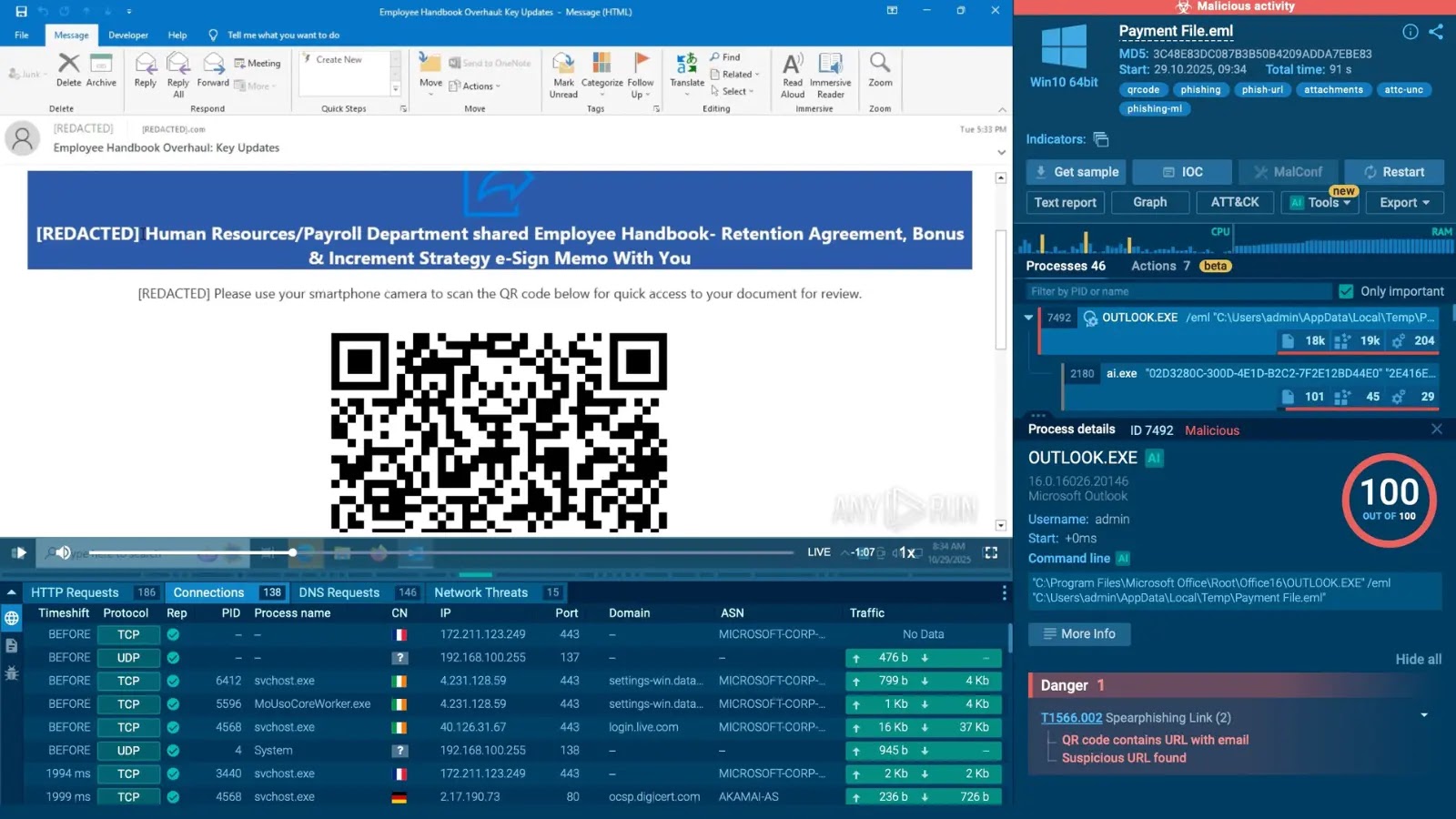
Kimsuky’s Evolving Threat: Weaponized QR Codes Deliver Mobile Malware The digital landscape continually presents evolving cyber threats, and one prominent actor in this space [...]
A recent critical routing issue within Microsoft’s infrastructure caused widespread access and sign-in disruptions for thousands of Microsoft 365 users in Japan and China. [...]
The digital landscape continues its rapid evolution, introducing both unprecedented opportunities and intensified threats. For organizations relying on virtual environments, the integrity and availability of [...]
Cisco AsyncOS 0-Day: Critical Exploitation in the Wild & What You Need to Know In the high-stakes world of cybersecurity, a zero-day vulnerability represents one [...]
In the relentless landscape of enterprise cybersecurity, a recent surge in brute-force attacks targeting widely used VPN gateways from Cisco and Palo Alto Networks has [...]