Unmasking the macOS Illusion: Critical ExifTool Flaw Puts Apple Systems at Risk For years, a prevailing sentiment among many users, and even some professionals, [...]
CISA Sounds the Alarm: macOS & iOS Vulnerabilities Under Active Attack The digital defenses of Apple users are under an immediate and significant threat. [...]
The Silent Threat: Fake AI Browser Extensions Compromise Enterprise Chat Histories The line between productivity and peril continues to blur in the enterprise landscape. A [...]
Urgent Security Alert: Hikvision Vulnerability CVE-2017-7921 Added to KEV Catalog Organizations worldwide face a critical cybersecurity challenge as a severe vulnerability impacting multiple Hikvision products [...]
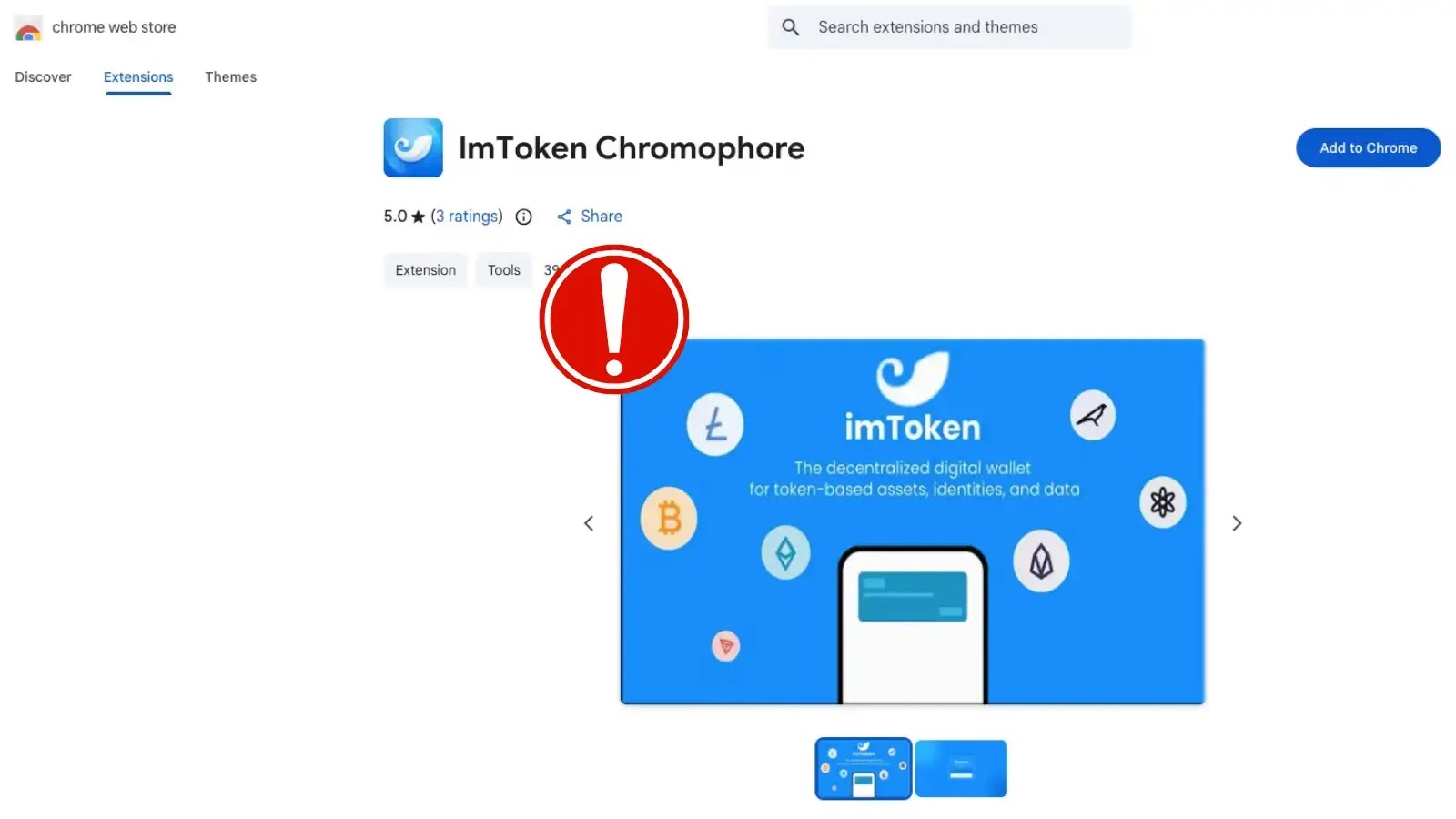
The Silent Threat: Malicious imToken Chrome Extension Steals Crypto Wallets In the decentralized world of cryptocurrency, the security of your digital assets hinges on [...]
The digital health landscape, while offering unparalleled convenience and efficiency, consistently presents a high-stakes target for malicious actors. A recent, sobering reminder of this vulnerability [...]
Unmasking the Critical AVideo Zero-Click Command Injection (CVE-2026-29058) The digital streaming landscape is an invaluable part of modern communication and entertainment, making the security [...]
A disturbing development in the cybersecurity underworld suggests a new, highly potent threat targeting Windows Remote Desktop Services (RDS). Reports indicate that a motivated threat [...]
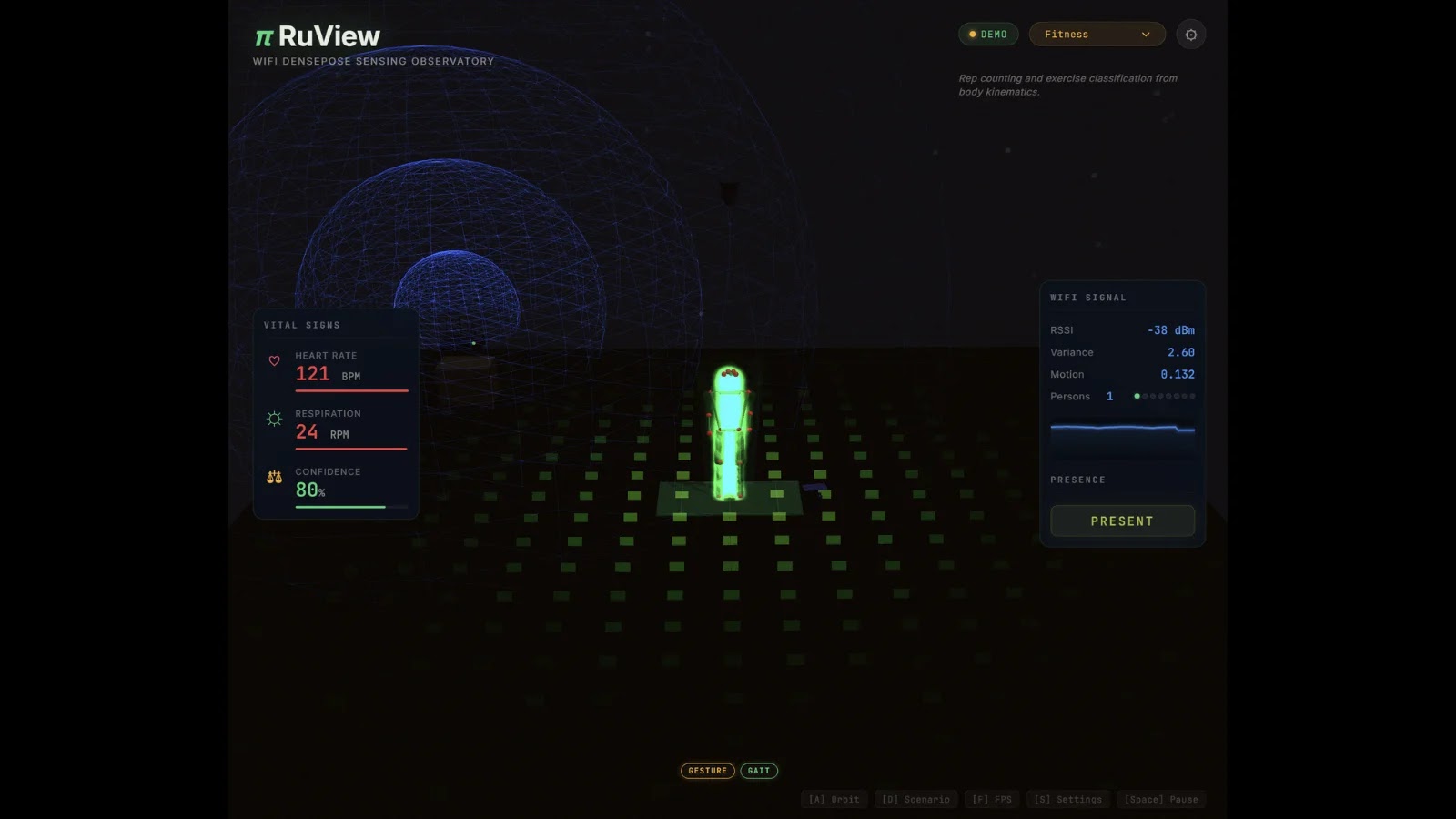
Unseen Eyes: WiFi Signals, Human Activities, and the π RuView Surveillance Threat The invisible waves that power our daily connectivity are now revealing our [...]
The Dawn of Autonomous Application Security: OpenAI’s Codex Security Unleashed In the relentless battle against software vulnerabilities, security teams often find themselves overwhelmed by a [...]