OceanLotus Shifts Focus: Targeting China’s Xinchuang IT Ecosystem in Supply Chain Attacks The digital battleground continues to evolve, and with it, the sophistication of state-sponsored [...]
Unmasking a Digital Shadow: Indonesia’s Gambling Ecosystem Under Scrutiny For over a decade, a sophisticated cybercrime infrastructure has silently thrived, deeply embedded within Indonesia’s illegal [...]
The cybercriminal landscape is undergoing a significant shift, with sophisticated tools increasingly paving the way for destructive ransomware attacks. A newly identified threat, dubbed “Shanya,” [...]
Hundreds of Porsches Rendered Undrivable: A Satellite Security System Malfunction immobilizes Luxury Vehicles Imagine stepping out to your high-performance luxury vehicle, only to find it [...]
The pharmaceutical industry, a bastion of innovation and critical research, finds itself increasingly targeted by sophisticated cyber threats. The recent disclosure by Inotiv, a prominent [...]
Rethinking AI Security: Critical Vulnerabilities in GitHub Copilot, Gemini CLI, and Claude The rapid integration of AI into software development has fundamentally reshaped how we [...]
Next.js Launches React2Shell Scanner: Immediate Defense Against Critical Vulnerability In the fast-paced world of web development, a critical vulnerability can emerge, threatening the security and [...]
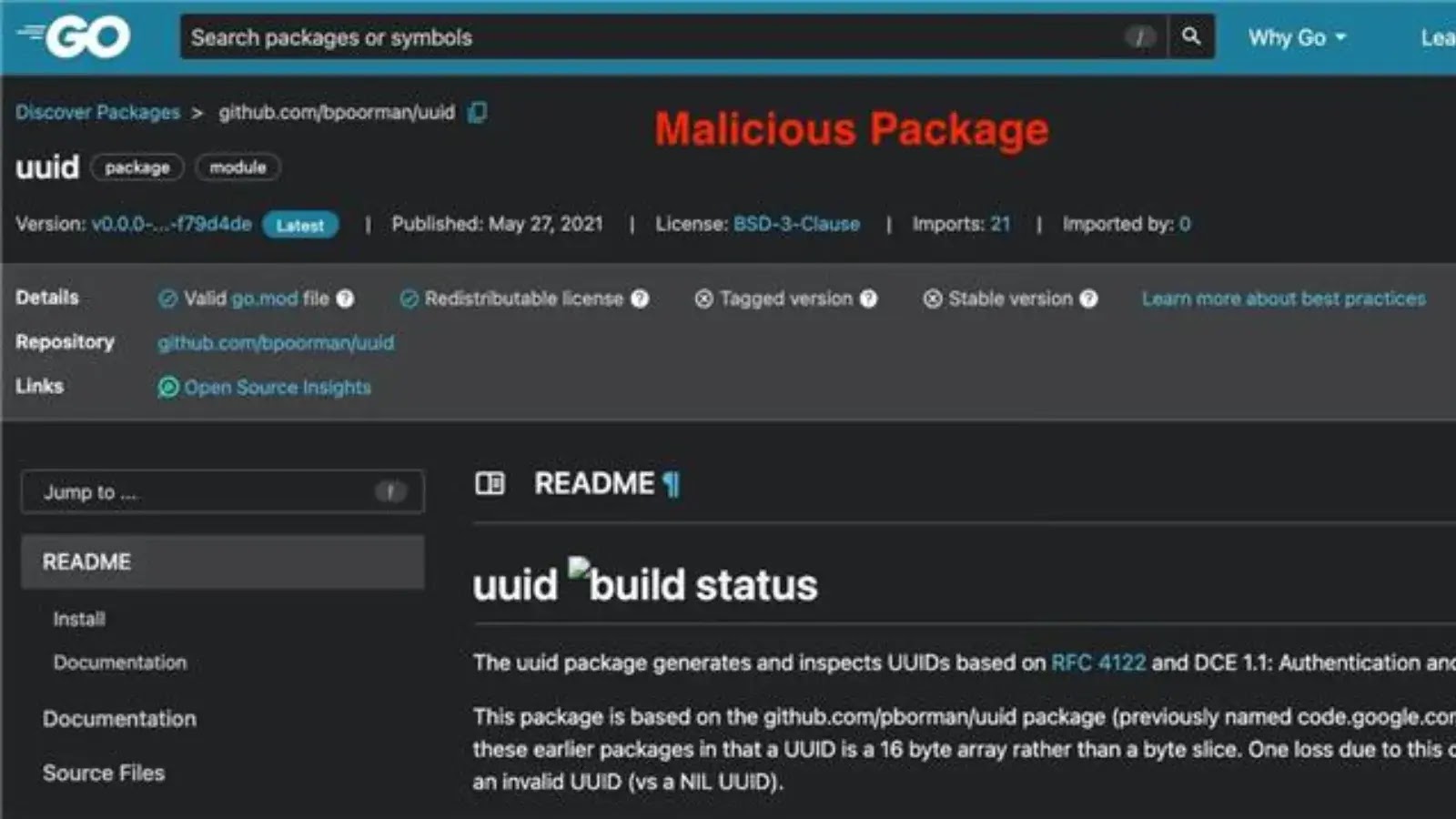
The Silent Threat: Malicious Go Packages Mimicking Google’s UUID Library In the vast landscape of software development, the efficiency and reusability offered by open-source libraries [...]
In the high-stakes world of cybersecurity, a disturbing trend has persisted despite international sanctions: commercial spyware companies relentlessly developing and deploying sophisticated tools to compromise [...]
The cybersecurity landscape has been rocked by recent developments concerning a critical remote code execution (RCE) vulnerability, now actively exploited in the wild. Tracked as [...]