The Gentlemen: A New Ransomware Threat Leveraging Dual Extortion The cybersecurity landscape has been rocked by the emergence of a sophisticated new ransomware group, aptly [...]
Software updates are the cornerstone of a secure digital environment, patching vulnerabilities and enhancing system stability. But what happens when the very mechanism designed to [...]
A disturbing trend has emerged from the cybersecurity landscape: threat actors are actively exploiting a critical Remote Code Execution (RCE) vulnerability in 7-Zip, the widely-used [...]
Sysmon’s Native Integration: A Game Changer for Windows Security For years, System Monitor (Sysmon) has stood as an indispensable utility in the cybersecurity toolkit. Its [...]
The Unseen Threat: Securing Electron Applications with Seraphic’s Breakthrough In the evolving landscape of enterprise software, a critical blind spot often persists: the security [...]
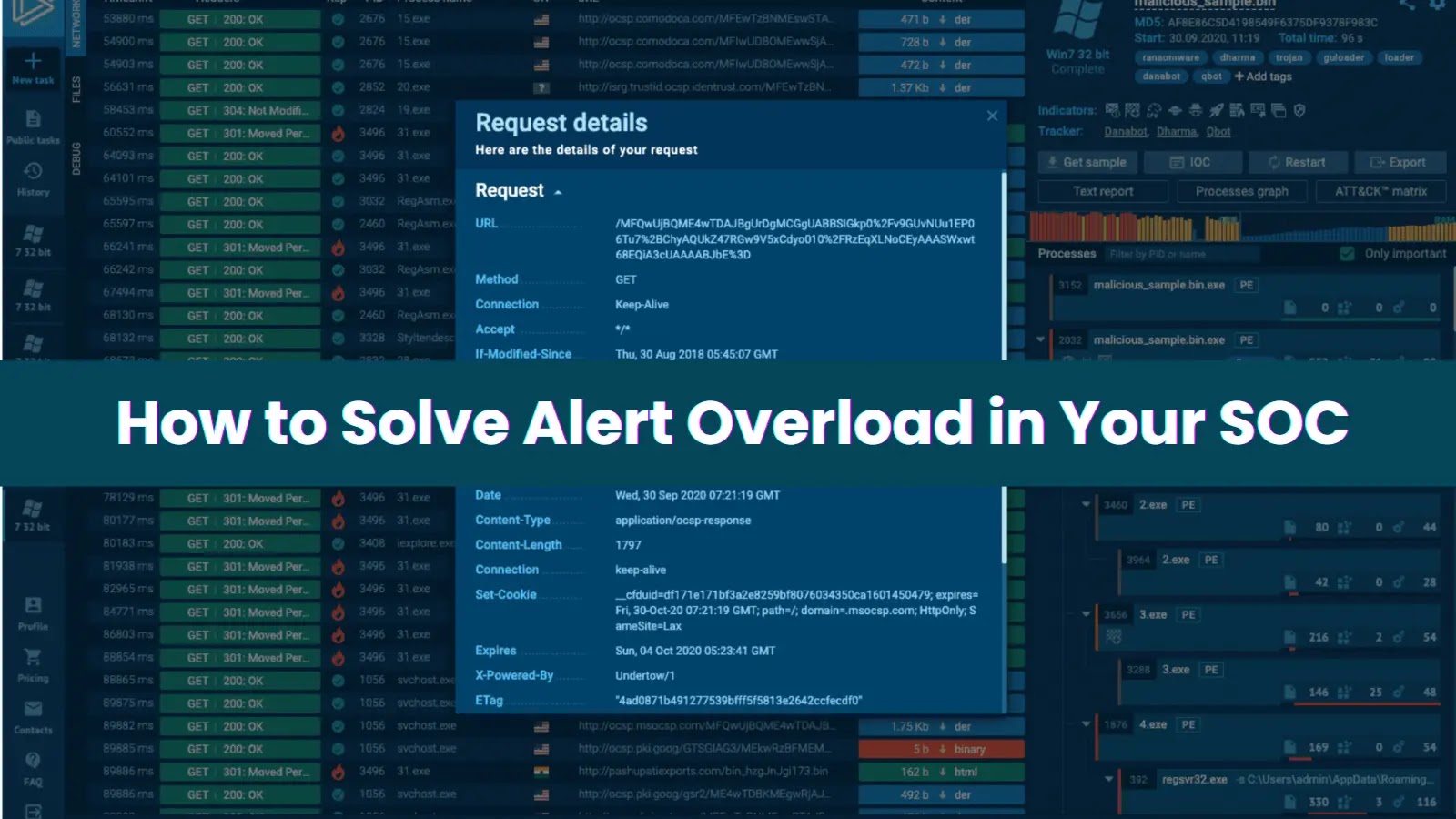
The Silent Killer: How Alert Overload Drains Your SOC Your Security Operations Center (SOC) is a critical line of defense, but what happens when [...]
Palo Alto Networks GlobalProtect VPNs Under Siege: A Deep Dive into 2.3 Million Attacks Remote access solutions are the backbone of modern enterprise connectivity, [...]
Malicious ‘Free’ VPN Extension with 9 Million Installs Hijacks User Traffic and Steals Browsing Data
The Silent Spy: Malicious ‘Free’ VPN Extensions and a 9 Million User Betrayal The promise of absolute digital freedom, often branded as a “free VPN,” [...]
Urgent Patch Alert: Critical SolarWinds Serv-U Vulnerabilities Expose Organizations to Remote Code Execution The digital landscape is a constant battleground, and for organizations relying on [...]
The pace of cyber threats continues to accelerate, demanding a more proactive and intelligent defense. Security teams are constantly challenged to move beyond reactive incident [...]