A few hours of downtime can feel like an eternity in our hyper-connected world. When a major internet infrastructure provider experiences an outage, the ripple [...]
Unmasking Remcos RAT: Decoding Its Command-and-Control Communications In the evolving threat landscape, understanding the intricate mechanisms of malware is paramount for effective defense. Today, we’re [...]
In a significant win against cybercrime, law enforcement agencies in the Netherlands have successfully dismantled a substantial infrastructure used by a rogue hosting provider to [...]
Lazarus Group Unleashes ScoringMathTea RAT: A New Threat to Global Security The landscape of cyber warfare is perpetually shifting, with state-sponsored advanced persistent threat (APT) [...]
A critical vulnerability within the Imunify AI-Bolit component recently sent shivers down the spines of server administrators worldwide. This wasn’t merely a minor flaw; it [...]
A chilling discovery has sent ripples through the WordPress community. A critical command injection vulnerability, tracked as CVE-2025-9501, has been identified in W3 Total Cache, [...]
In a stark reminder of the persistent threats businesses face, the notorious Everest ransomware group has allegedly claimed a significant cyber victory against Under Armour, [...]
The global aerospace and defense sectors are under siege from a highly sophisticated, Iranian-backed threat group known as UNC1549. Since mid-2024, this advanced persistent threat [...]
The digital landscape is under constant siege, and a pervasive, insidious threat has escalated its tactics: Lynx ransomware. Recent intelligence reveals a sinister evolution where [...]
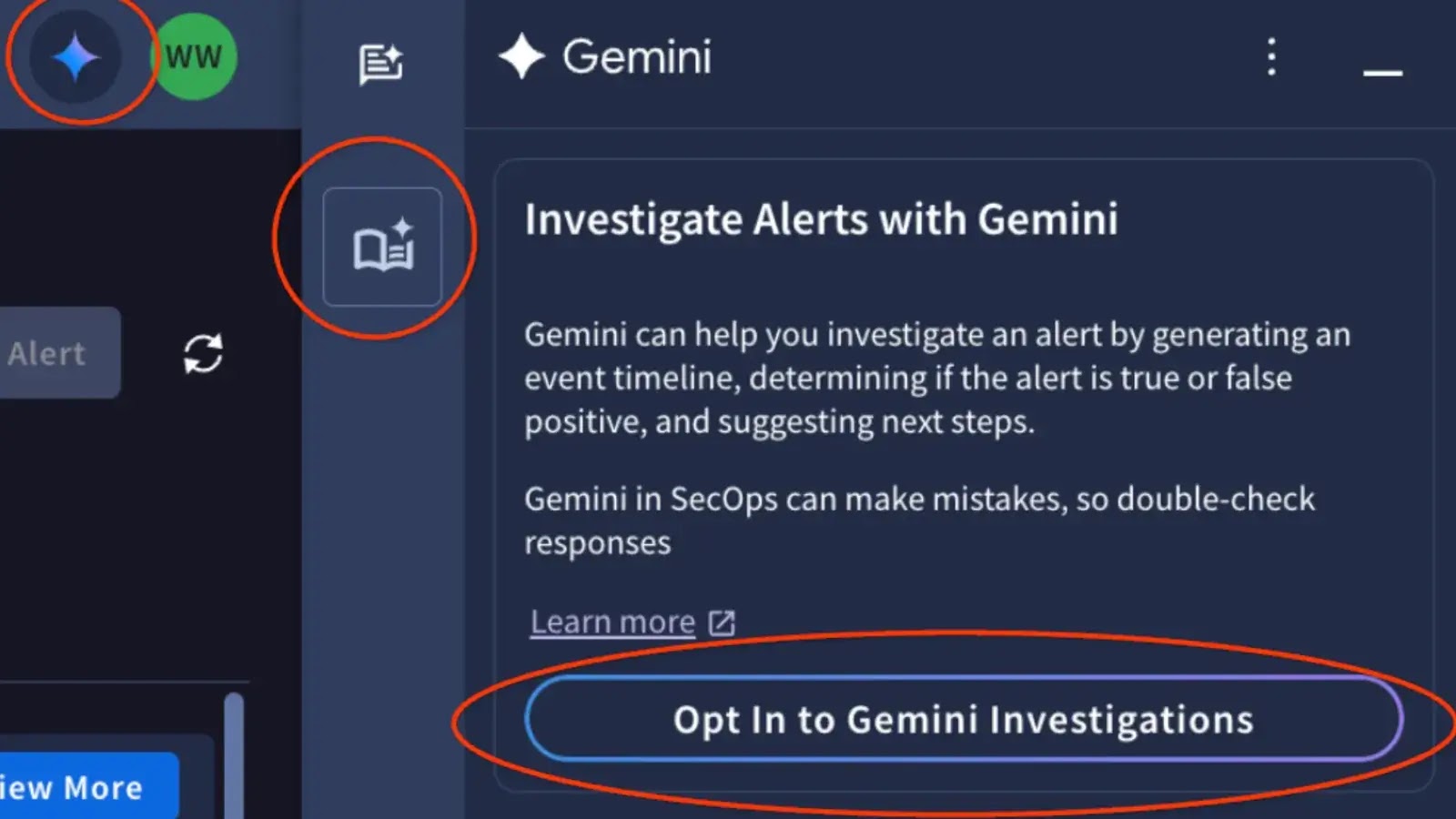
In the relentless battle against cyber threats, security operations centers (SOCs) face an ever-increasing deluge of alerts. Differentiating critical incidents from benign noise demands [...]