The Unseen Guest: Pre-Installed Spyware on Samsung Galaxy Devices The trust users place in their smartphone manufacturers is fundamental. When a device, designed for communication [...]
The Deceptive Lure of Fake Invoices: XWorm’s Covert Credential Theft In the relentless landscape of cyber threats, attackers constantly refine their tactics. A particularly [...]
The AI-Powered Cyberattack Has Arrived: A New Era of Threat The cybersecurity landscape has undeniably shifted. For years, we’ve discussed the theoretical implications of [...]
Critical pgAdmin4 RCE Flaw: A Looming Threat to PostgreSQL Infrastructures The digital defense perimeter of PostgreSQL database environments just got a little thinner. A [...]
The digital defense landscape is under constant assault, and a new threat, RONINGLOADER, exemplifies the escalating sophistication of malware authors. Recently identified targeting Chinese users, [...]
A new threat looms for organizations relying on FortiWeb Web Application Firewalls (WAFs). A proof-of-concept (PoC) exploit tool for CVE-2025-64446 has been publicly released, [...]
Unpacking the Critical Cisco Catalyst Center Privilege Escalation Vulnerability A significant security concern has emerged for organizations leveraging Cisco Catalyst Center Virtual Appliances. A [...]
Unmasking DigitStealer: macOS Under Siege by a New Multi-Stage Threat The digital landscape for macOS users has just become significantly more perilous. A formidable new [...]
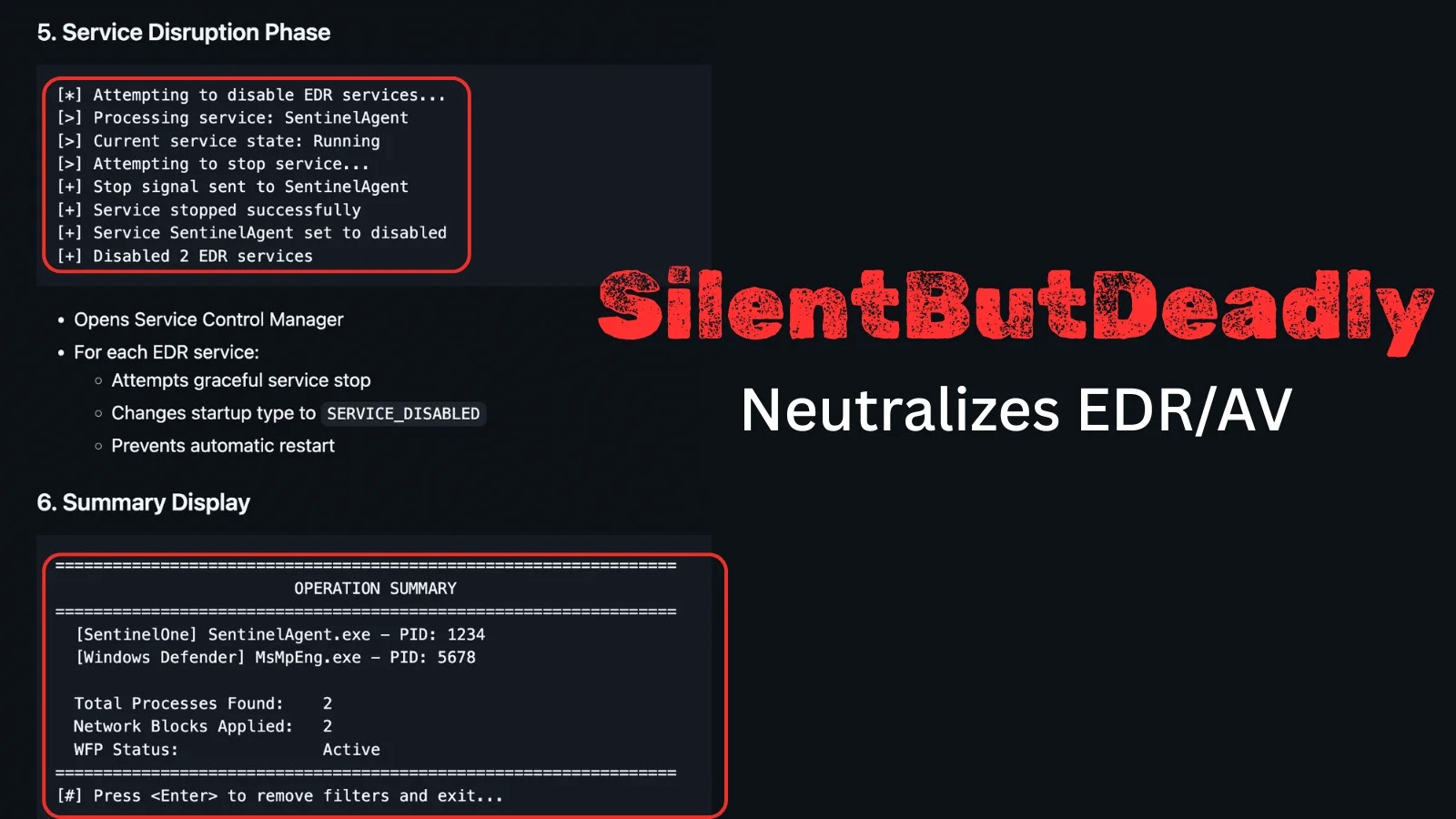
The ever-escalating arms race between cyber defenders and attackers recently saw a new development with the emergence of SilentButDeadly. This open-source tool introduces a [...]
The persistent threat landscape demands constant vigilance from cybersecurity professionals. A new wave of Formbook malware attacks highlights this critical need, demonstrating sophisticated tactics to [...]