A new security update for Google Chrome addresses a critical vulnerability within the browser’s Background Fetch API. Users are strongly advised to update their [...]
Urgent Alert: Fortinet FortiCloud SSO Vulnerability (CVE-2026-24858) Under Active Exploitation The cybersecurity landscape has been rocked by news of a critical authentication bypass vulnerability [...]
In the high-stakes world of enterprise cybersecurity, even the most established brands are not immune to the relentless threat of data breaches. Sportswear giant [...]
WhatsApp Confirms Message Privacy Amidst Lawsuit Claims: What You Need to Know In an era where digital privacy is paramount, a recent class-action lawsuit [...]
Chinese National Receives 46-Month Sentence for Multi-Million Dollar Crypto Laundering Scheme The digital frontier, while promising innovation and interconnectedness, also presents fertile ground for [...]
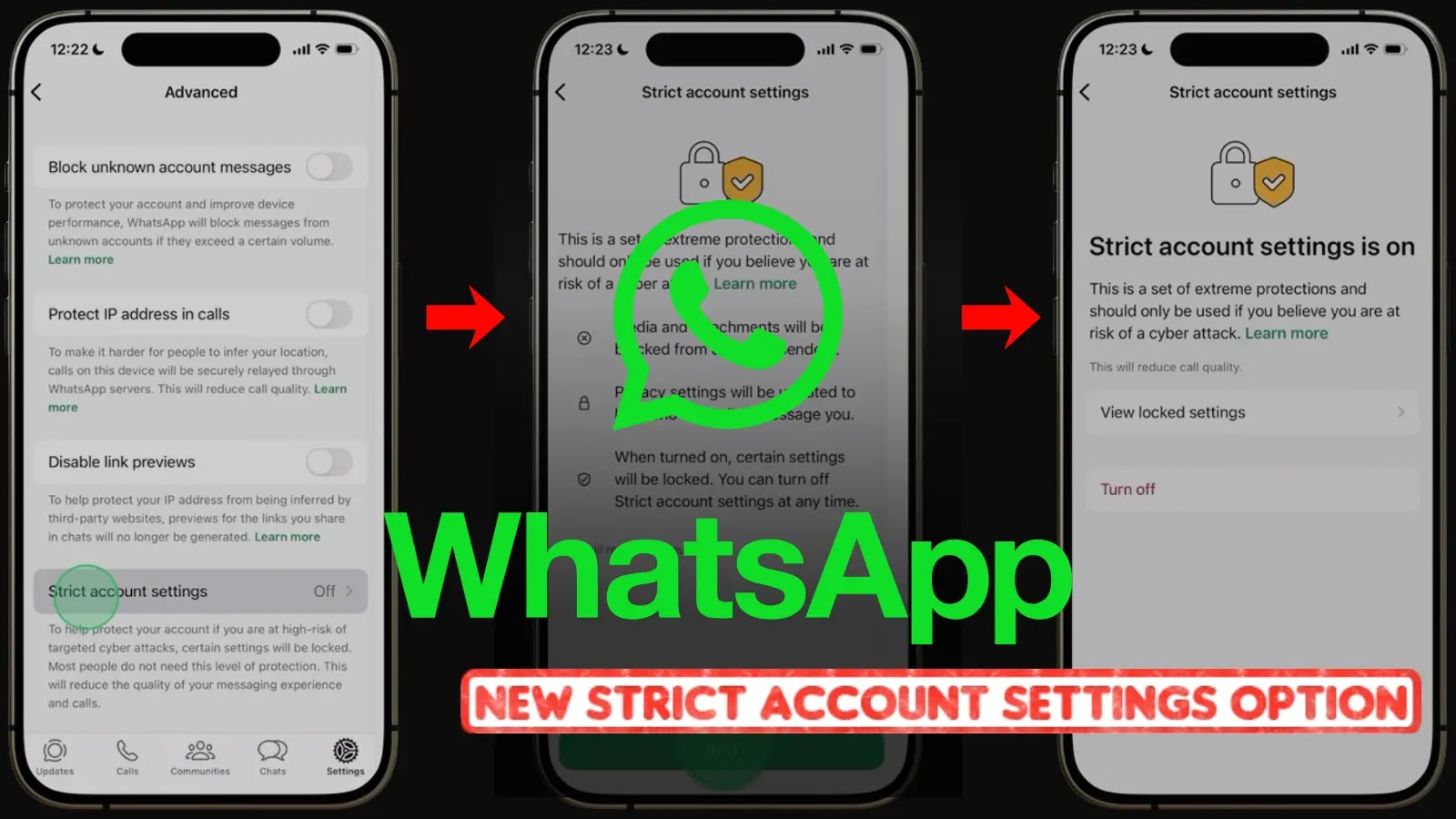
WhatsApp Bolsters Security: Introducing Strict Account Settings for Enhanced Protection In an era where digital communication is foundational, securing our messaging platforms is paramount. WhatsApp, [...]
HoneyMyte’s Evolving Threat: CoolClient Malware Now Targets Browser Login Data The digital battleground is continuously shifting, and advanced persistent threat (APT) groups are quick to [...]
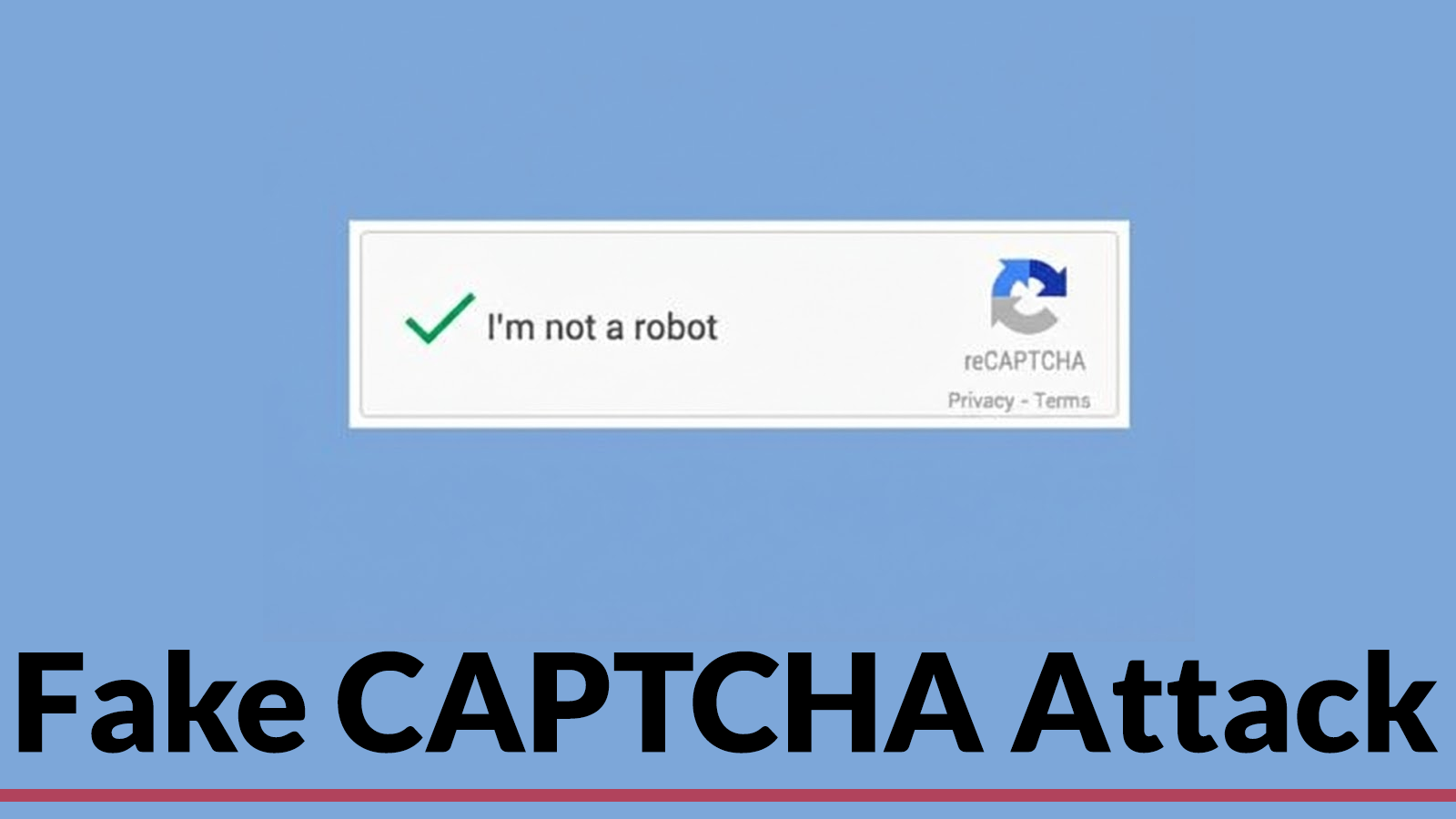
In the evolving landscape of cyber threats, attackers continually refine their methods, blending social engineering with legitimate system functionalities to bypass defenses. A recent campaign [...]
Unpacking OpenSSL Vulnerabilities: A Remote Code Execution Nexus The digital arteries of countless applications and systems worldwide rely on OpenSSL for secure communication. When [...]
FortiCloud SSO Disabled: Urgent Response to Zero-Day Exploitation The digital landscape demands constant vigilance. Evidence of this imperative recently emerged when Fortinet, a titan [...]