Facebook remains a primary target for threat actors due to its vast user base and the wealth of personal data it contains. A new and [...]
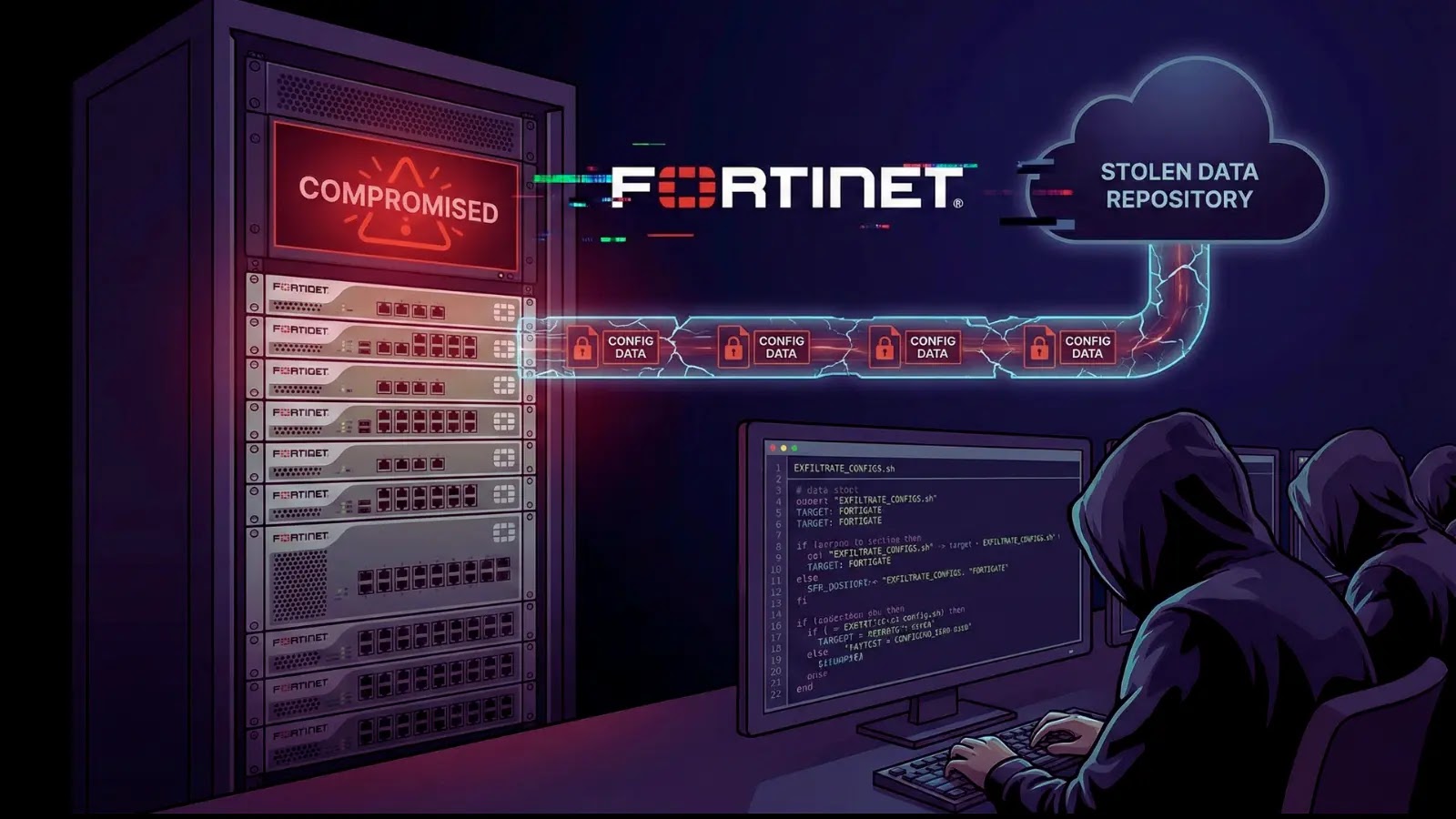
FortiGate Firewalls Under Attack: Automated Campaign Exploits Devices to Steal Configuration Data Recent intelligence points to a renewed and concerning surge in automated malicious activity [...]
Critical Vivotek Vulnerability Opens Door to Remote Code Execution for Legacy Devices In an alarming development for organizations relying on older surveillance infrastructure, a critical [...]
A disturbing trend is emerging from the complex landscape of web applications: a significant number of third-party tools are accessing sensitive user data without proper [...]
The digital landscape is a constant battleground, and even the most robust systems can harbor hidden vulnerabilities. In a recent and critical development, the U.S. [...]
The Python Package Index (PyPI) serves as a critical repository for open-source software, fueling countless development projects. However, its open nature also makes it a [...]
Unveiling Critical Chainlit AI Vulnerabilities: A Gateway to Cloud Environment Takeovers The rapid adoption of AI frameworks has revolutionized software development, but with innovation [...]
Unmasking the Multi-Stage Threat: When Malware Silences Defender The digital landscape is a constant battlefield, and a concerning new multi-stage malware campaign is demonstrating [...]
A silent threat has been lurking within a widely used Node.js library, potentially exposing countless applications to severe compromise. We’re talking about a critical [...]
The internet relies on a complex web of systems working in harmony, and at the core of this infrastructure is the Domain Name System [...]