The silent threat of information-stealing malware constantly evolves, and a recent discovery highlights this persistence: SolyxImmortal. This Python-based implant is not about loud, destructive [...]
A disturbing trend in cybercrime has emerged, leveraging one of the internet’s most trusted advertising platforms: Google Ads. Recent reports, particularly identifying activity in September [...]
A critical security flaw has been identified in Livewire Filemanager, a widely adopted component for file management within Laravel web applications. This vulnerability, tracked as [...]
The Silent Saboteurs: Malicious Chrome Extensions Targeting Enterprise HR & ERP Platforms Enterprise security has recently faced a formidable and coordinated threat: a cluster [...]
The digital landscape consistently reminds us of the persistent and evolving threats organizations face. A recent and significant incident highlights this reality: the Investment [...]
The digital battlefield continues to evolve, and recent developments highlight the relentless efforts of cybercriminals to exploit vulnerabilities for financial gain. In a significant [...]
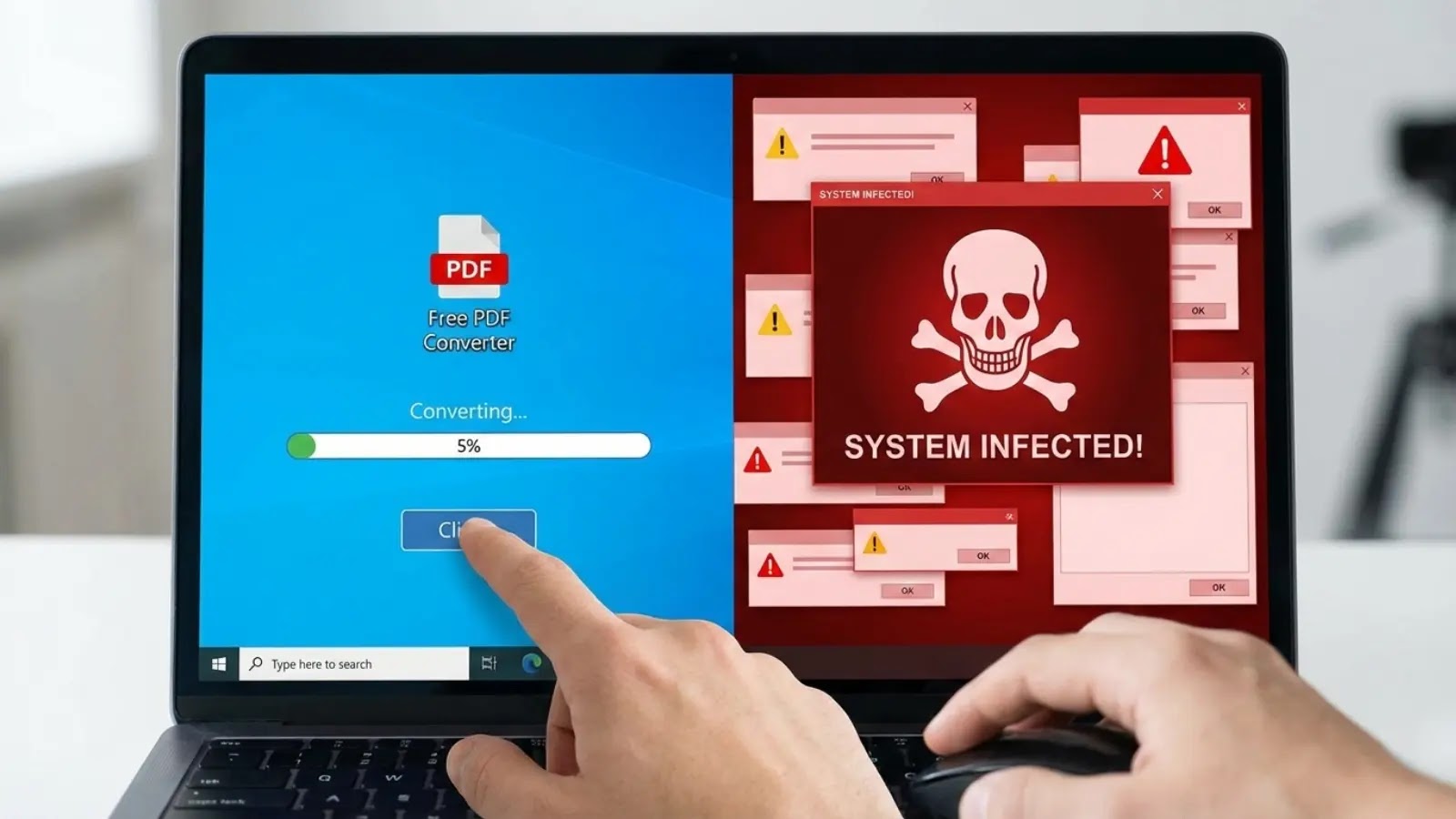
The Hidden Threat: How Free Converter Apps Turn Your Clean System into an Infected Minefield The promise of free utility applications often masks a [...]
A sophisticated new spear-phishing campaign, dubbed Operation Poseidon, has emerged, leveraging an insidious tactic: the abuse of Google Ads infrastructure to distribute the potent [...]
A disturbing revelation from the cybersecurity community has sent ripples through organizations relying on cloud security, specifically those leveraging Cloudflare’s robust Web Application Firewall (WAF). [...]
The Silent Heist: When Paychecks Vanish Without a Data Breach Imagine your employees, diligent and trustworthy, logging into their bank accounts on payday only [...]