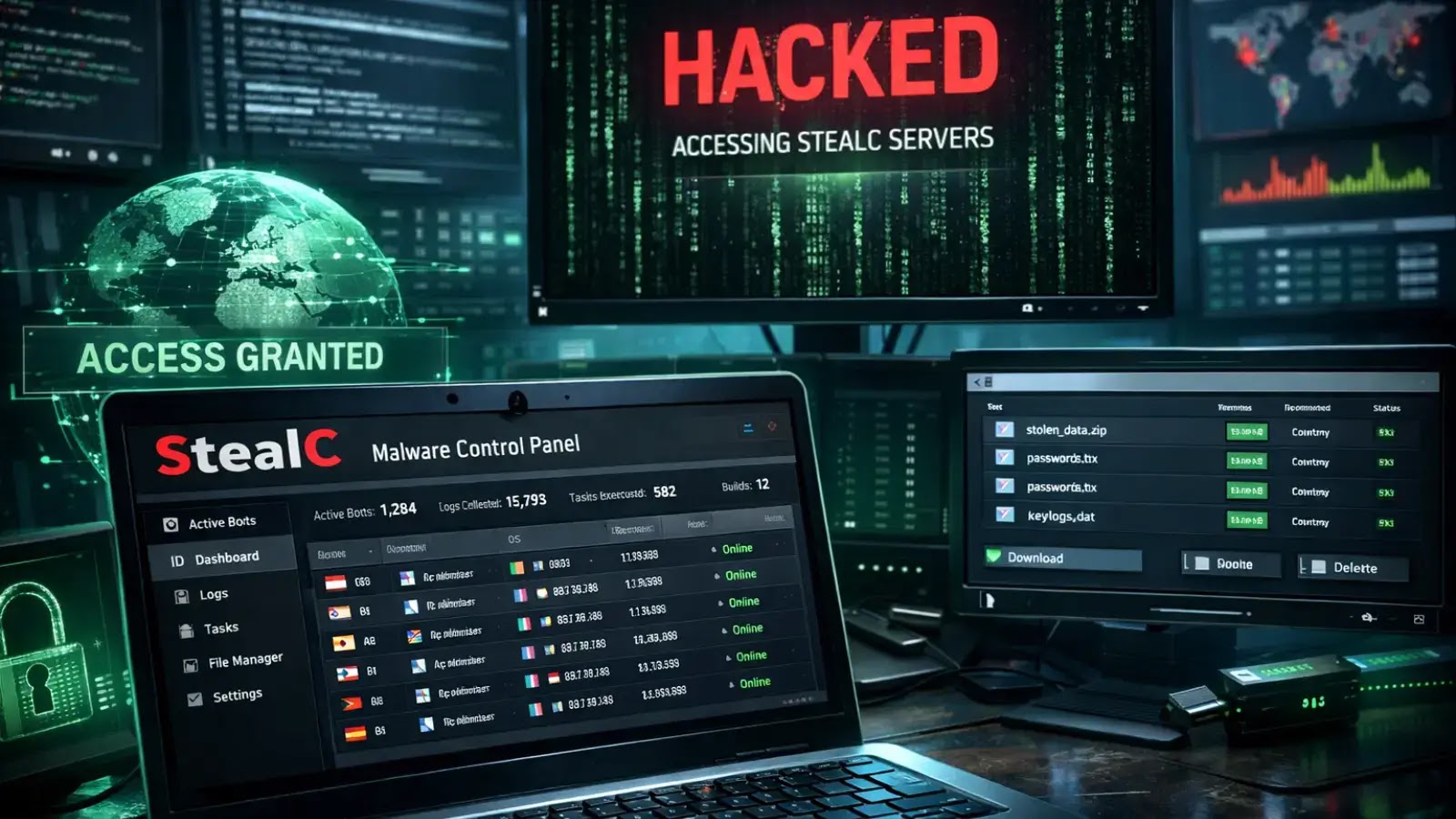
Unmasking the Threat: Researchers Infiltrate StealC Malware C2 Infrastructure In a significant win for cybersecurity, security researchers have successfully breached the command-and-control (C2) infrastructure [...]
The landscape of cloud security is constantly shifting, presenting new challenges even within highly sophisticated platforms. A recent disclosure by XM Cyber researchers has brought [...]
In the relentlessly evolving landscape of cybersecurity, the integrity and trustworthiness of digital communications hinge significantly on robust encryption. For years, the reliance on Transport [...]
Cloudflare Acquires Astro: A Boost for Open-Source Web Development The landscape of web development is constantly evolving, with speed, performance, and developer experience at the [...]
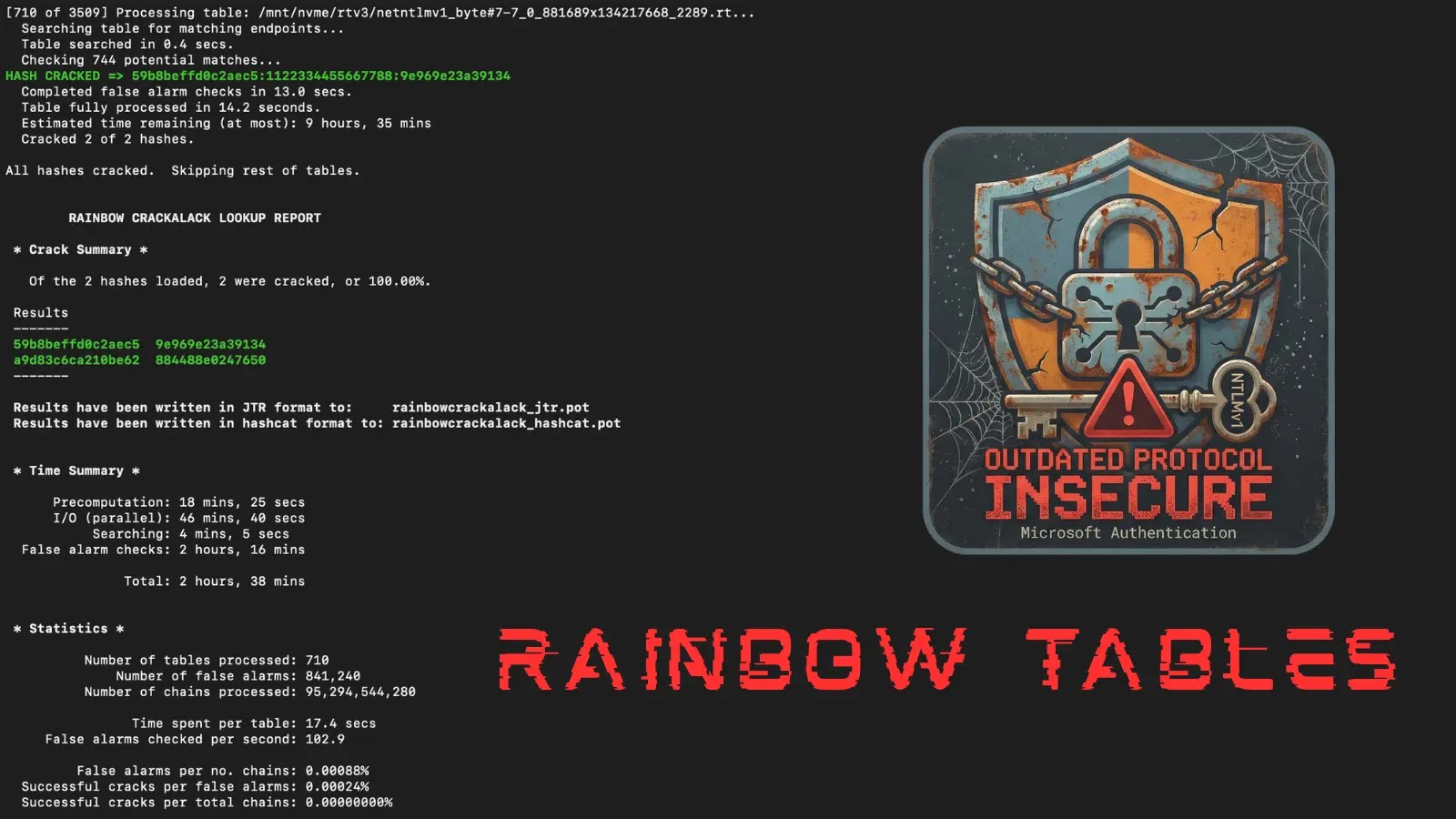
The cybersecurity landscape has just received a stark reminder of the persistent dangers posed by legacy protocols. Google-owned Mandiant, a titan in the threat [...]
Microsoft January 2026 Update Disrupts Remote Desktop Connections: An Emergency Fix Released The operational flow of countless organizations hinges on reliable remote access. When that [...]
For many years, the choice of a Google email address has felt like a permanent tattoo in the digital realm. An ill-considered username, perhaps chosen [...]
The digital perimeter of many organizations relies heavily on robust email security, making any compromise in this area a top-tier threat. Recently, Cisco, a titan [...]
GitGuardian Closes 2025 with Strong Enterprise Momentum, Protecting Millions of Developers Worldwide
The digital landscape is a battleground, and for organizations big and small, the integrity of their code and the security of their non-human identities are [...]
Web applications are the digital storefronts and operational backbones of modern organizations, making them prime targets for malicious actors. A single vulnerability in a web [...]