A recent incident involving a stolen Gemini API key serves as a stark reminder of the devastating financial consequences that can arise from inadequate [...]
When Trusted Tools Turn Treacherous: AzCopy Exploited for Data Exfiltration The cybersecurity landscape has always been a game of cat and mouse, but the [...]
The landscape of cyber threats is perpetually reshaped by evolving attack methodologies. For years, cybercriminals largely adapted Windows-centric malware for Linux environments. However, a significant [...]
The digital battlefield continues to evolve, and recent events underscore the sophisticated threats targeting critical infrastructure and government entities. In a stark reminder of [...]
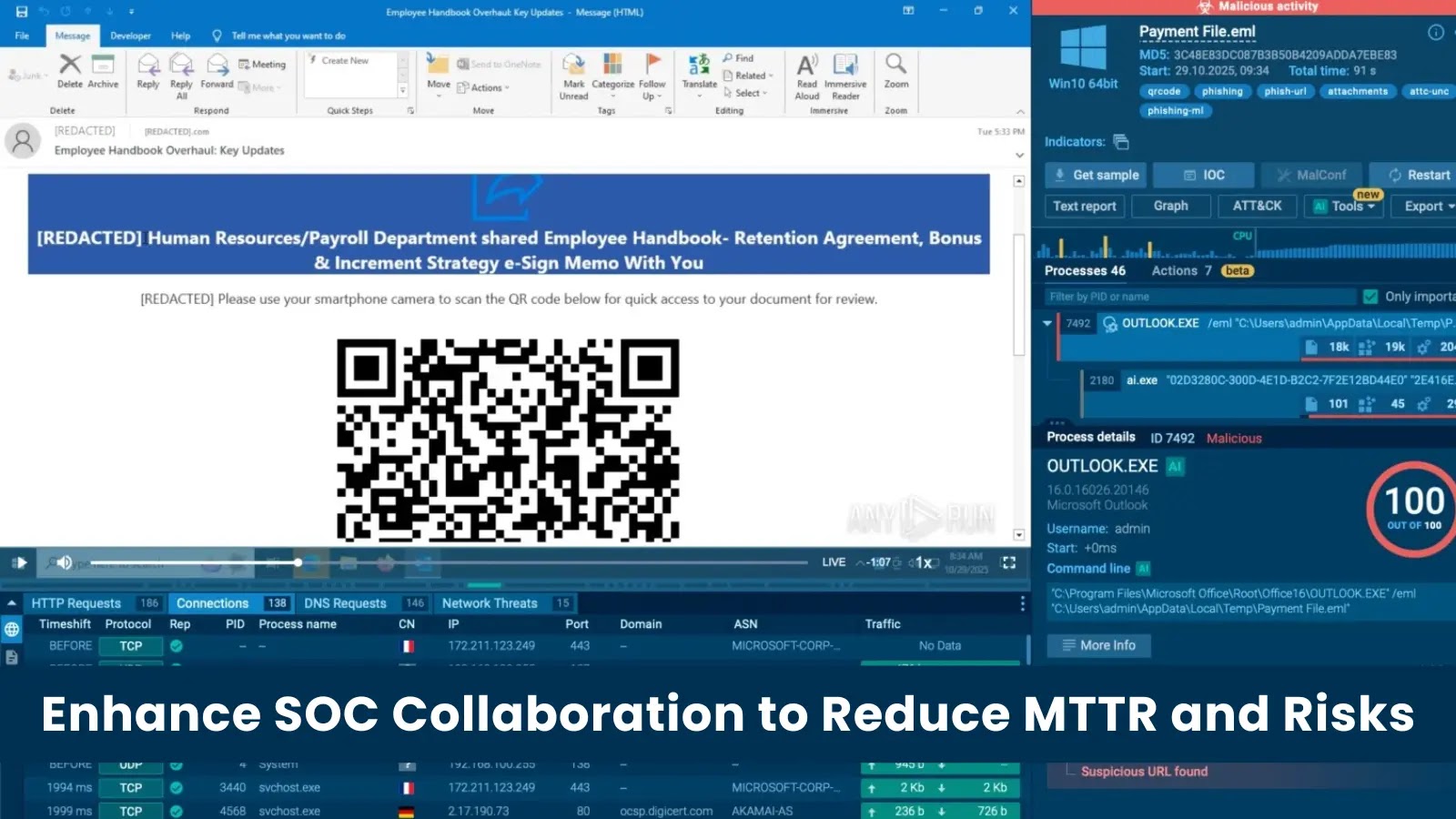
The Critical Link: How Better SOC Collaboration Slashes MTTR and Business Risk In the high-stakes environment of a modern Security Operations Center (SOC), two [...]
The pace of cyber threats is accelerating, and the lines between human-orchestrated attacks and machine-driven intrusions are blurring at an alarming rate. Organizations that [...]
Operation Leak: The Takedown of LeakBase Cybercriminal Forum In a significant victory against organized cybercrime, an international law enforcement coalition, led by the FBI, [...]
When Recovery Fails: Understanding the Windows 10 KB5068164 WinRE Boot Failure Imagine a scenario where your crucial Windows 10 system encounters a critical error. [...]
The digital battleground is constantly shifting, with threat actors continuously innovating their tactics. For cybersecurity professionals, staying ahead of these malicious advancements is paramount. [...]
A disturbing discovery has emerged for macOS users relying on IPVanish VPN. A critical privilege escalation vulnerability has been identified within the IPVanish VPN application [...]