In the dynamic landscape of workflow automation, n8n has emerged as a powerful open-source platform, empowering users to connect applications and automate intricate processes. [...]
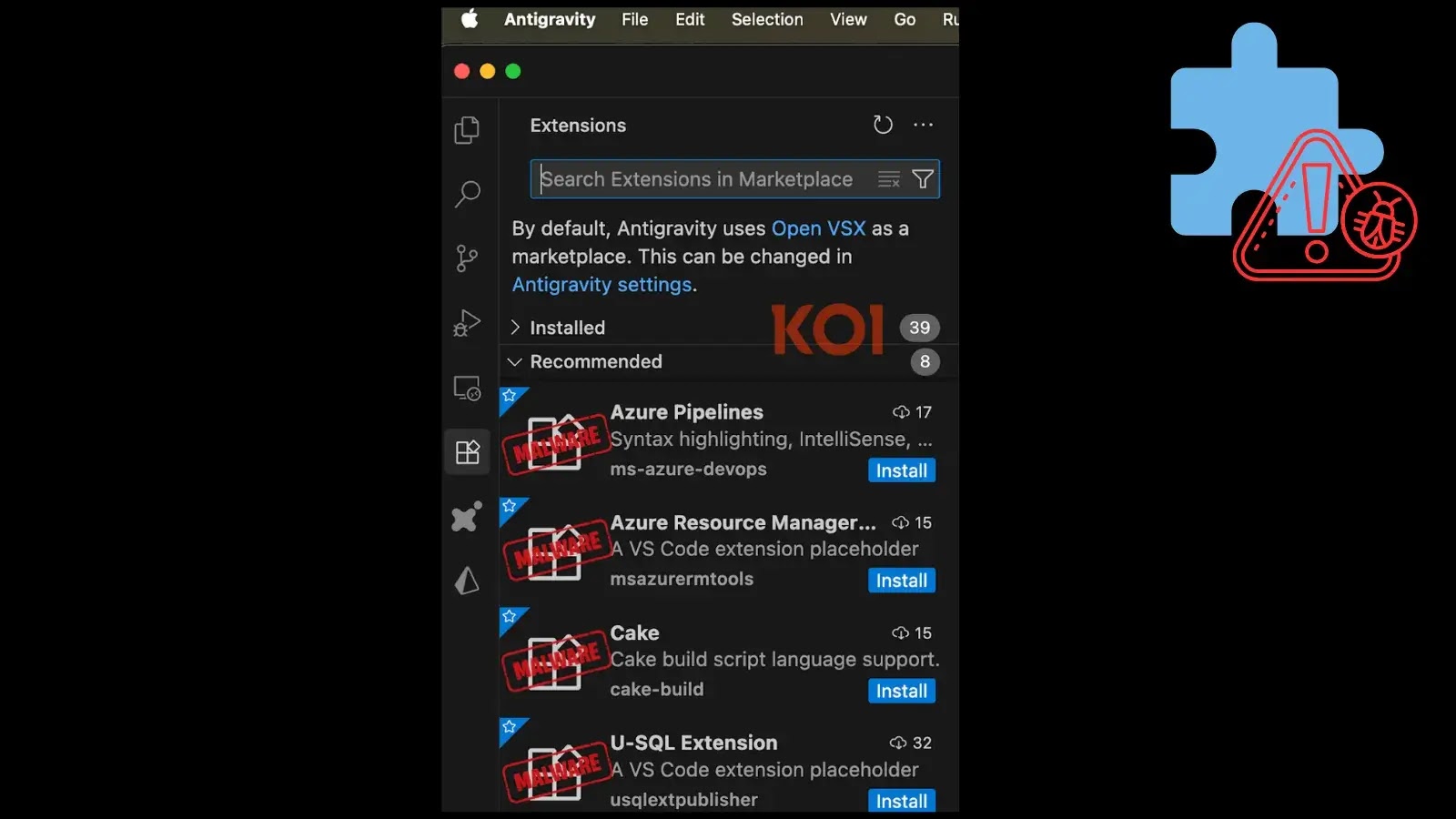
Navigating the AI-Powered IDE Minefield: Malicious Extension Recommendations Threaten Developer Security The landscape of software development is undergoing a rapid transformation, driven by innovative [...]
CISA’s KEV Catalog Explosive Growth: A 2025 Retrospective on Surging Exploitation The cybersecurity landscape has undergone a dramatic shift, and the United States Cybersecurity [...]
The digital battlefield continues to evolve, and with it, the sophistication of tools wielded by malicious actors. A recent disturbing development on the dark web [...]
The Criticality of Endpoint Management in 2026 The modern IT landscape is a tapestry woven with hybrid work models, remote teams, and a sprawling array [...]
Organizations worldwide face a new, highly sophisticated phishing campaign. Threat actors are masquerading as Google Support, leveraging a multi-pronged social engineering attack to pilfer user [...]
The digital landscape is a constant battleground, where cyber attackers relentlessly innovate to circumvent defenses. A new and particularly insidious campaign, dubbed “ClickFix,” has emerged, [...]
The Silent Compromise: How Stolen Cloud Credentials Are Fueling Global Breaches The digital landscape is fraught with sophisticated threats, yet sometimes the most devastating [...]
Stealthy Tuoni C2 Malware Infiltrates U.S. Real Estate: A New Era of Evasion The landscape of cyber threats is shifting. Gone are the days [...]
The cybersecurity landscape just got a significant jolt. Following a period of disconcerting silence, the notorious threat group known as the Scattered Lapsus$ Hunters [...]