A Critical Alert for Angular Developers: XSS Vulnerability in i18n Pipeline In the intricate landscape of modern web development, security often hinges on the [...]
The dawn of AI-driven autonomous systems promised unparalleled efficiency and innovation. Yet, a recent discovery casts a long shadow over this promise, revealing a critical [...]
HPE AutoPass Vulnerability: Remote Authentication Bypass Puts Licensing Servers at Risk A critical security alert has been issued concerning a significant flaw within the AutoPass [...]
The landscape of software development is constantly evolving, bringing with it both innovation and increased complexity. As organizations accelerate their digital transformation, the challenge of [...]
A severe security vulnerability has been identified within Langflow, a prominent AI application platform, allowing for perilous remote code execution (RCE) attacks. This critical [...]
A disturbing trend continues to challenge the integrity of software supply chains, and the latest incident directly impacts the vibrant PHP and Laravel developer [...]
Urgent Warning: VMware Aria Operations Vulnerability Actively Exploited In The Wild The cybersecurity landscape remains a relentless battleground, and a recent advisory from the [...]
Cyber Conflict Escalates: Epic Fury, Roaring Lion, and Iran’s Digital Retaliation The digital realm often mirrors geopolitical tensions, and recent events have starkly illustrated [...]
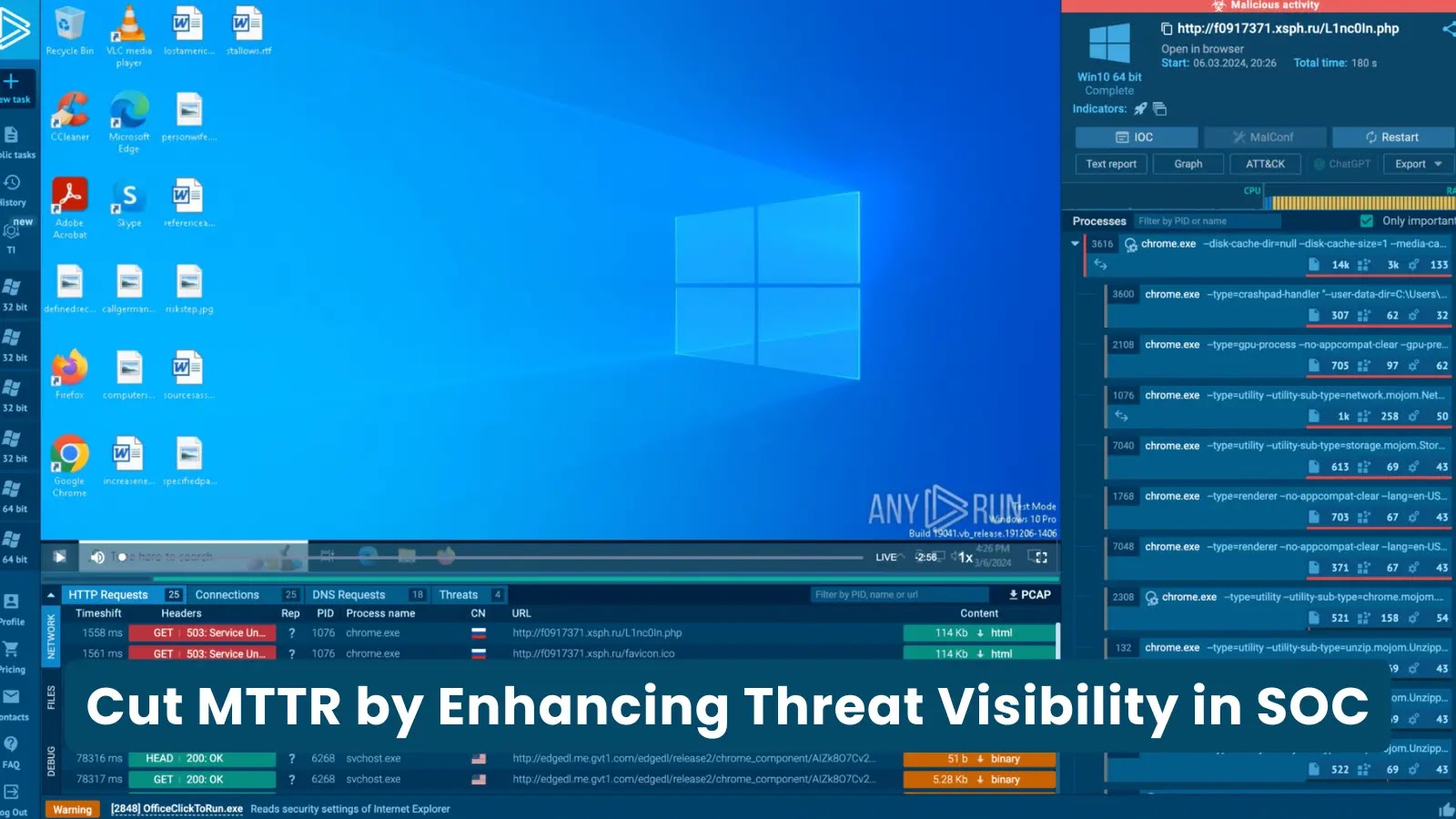
Elevating SOC Efficacy: Bolstering Threat Visibility to Reduce MTTR The security operations center (SOC) faces an unrelenting barrage of threats. Amidst this constant pressure, [...]
Once considered a haven for privacy-conscious individuals, Telegram has undergone a significant transformation. It’s no longer just a secure messaging app; it has evolved [...]