The global cybersecurity landscape is a constant battlefield, with state-sponsored threat actors employing advanced tactics to achieve their objectives. Recently, a joint investigation by [...]
Microsoft Acknowledges Critical RemoteApp Connection Breakage in Latest Windows Updates Enterprise environments utilizing Azure Virtual Desktop (AVD) and RemoteApp connections are currently facing a [...]
Organizations worldwide face an escalating threat landscape, with ransomware remaining a top concern. Among the most insidious evolutions in this space is the rise of [...]
The modern contact center is the nerve center of customer interaction, making its underlying infrastructure a prime target for malicious actors. Recent disclosures highlight critical [...]
A critical new threat has emerged for organizations and individuals relying on ASUS devices. The Cybersecurity and Infrastructure Security Agency (CISA) has officially added an [...]
A severe security flaw lurking within HPE OneView Software has sent a clear warning signal across the cybersecurity landscape. This critical vulnerability, capable of allowing [...]
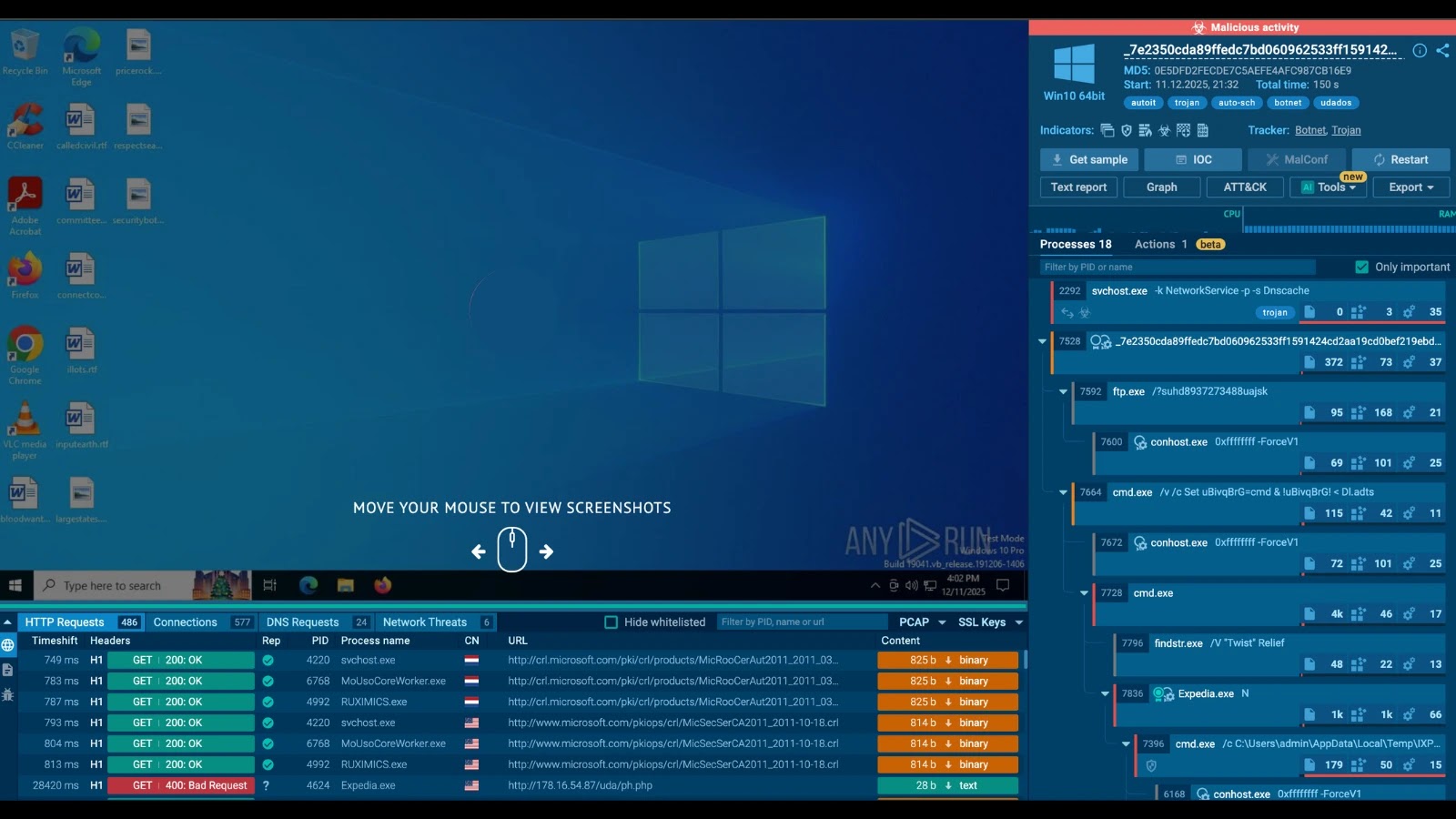
Unmasking Udados: A New Botnet’s Assault on the Tech Sector The digital landscape just got a new, formidable adversary. A newly identified botnet malware [...]
OpenAI GPT-5.2-Codex: Revolutionizing Agentic Coding and Vulnerability Detection The pace of software development and the escalating complexity of cybersecurity threats demand increasingly sophisticated tools. In [...]
The React2Shell Threat: Unpacking CVE-2025-55182 and Escalating Attacks A new and aggressive threat, dubbed React2Shell (officially CVE-2025-55182), has emerged, targeting widely deployed React Server Components [...]
The digital landscape is a constant battleground, and even the most seasoned users can fall victim to sophisticated attacks. A new and concerning threat, Phantom [...]