jsPDF Vulnerability Exposes Millions to Object Injection Attacks: A Deep Dive The digital landscape consistently presents new challenges for developers, and a recent discovery [...]
North Korean threat actors are escalating their sophisticated cyber espionage efforts, employing a new, more insidious tactic that blends social engineering with advanced malware [...]
The digital landscape relies heavily on robust authentication mechanisms. Multi-Factor Authentication (MFA) stands as a critical barrier against unauthorized access, safeguarding sensitive data and systems. [...]
Starkiller: The Phishing Framework That Proxies Real Login Pages to Bypass MFA The digital threat landscape constantly evolves, and with it, the sophistication of [...]
A new, highly sophisticated cyber campaign has surfaced, employing a deceptive technique dubbed “ClickFix” to propagate a custom remote access trojan (RAT) known as [...]
For organizations relying on WordPress, a new and insidious threat has emerged, silently compromising websites to PUSH malware onto unsuspecting users. A threat actor, [...]
A disturbing revelation has sent ripples through the cybersecurity landscape: Conduent Business Services, LLC, a prominent government technology contractor, has been entangled in a [...]
Anthropic Claude Under Large Scale Distillation Attacks By Chinese AI Labs with 13 Million Exchanges
The landscape of artificial intelligence is marked by rapid innovation, but also by increasingly sophisticated threats. A recent accusation by Anthropic, creators of the [...]
Google Chrome users, pay critical attention. A recent emergency security update, rolling out progressively to versions 114.0.5735.116/117 for Windows and macOS, and 114.0.5735.116 for [...]
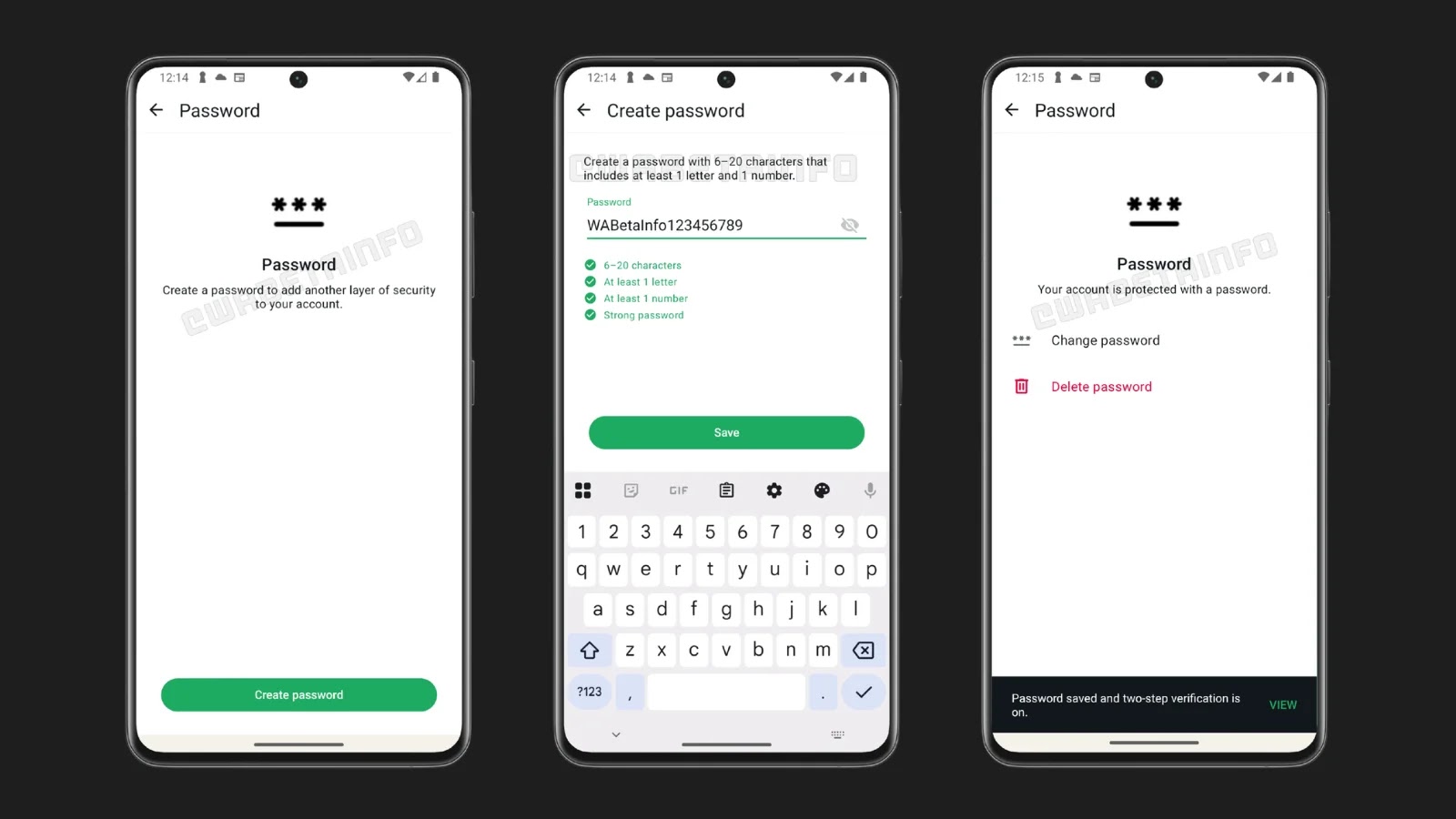
In an increasingly interconnected digital landscape, the security of our communication channels is paramount. WhatsApp, a platform relied upon by billions globally, is taking a [...]