Rethinking AI Security: Critical Vulnerabilities in GitHub Copilot, Gemini CLI, and Claude The rapid integration of AI into software development has fundamentally reshaped how we [...]
Next.js Launches React2Shell Scanner: Immediate Defense Against Critical Vulnerability In the fast-paced world of web development, a critical vulnerability can emerge, threatening the security and [...]
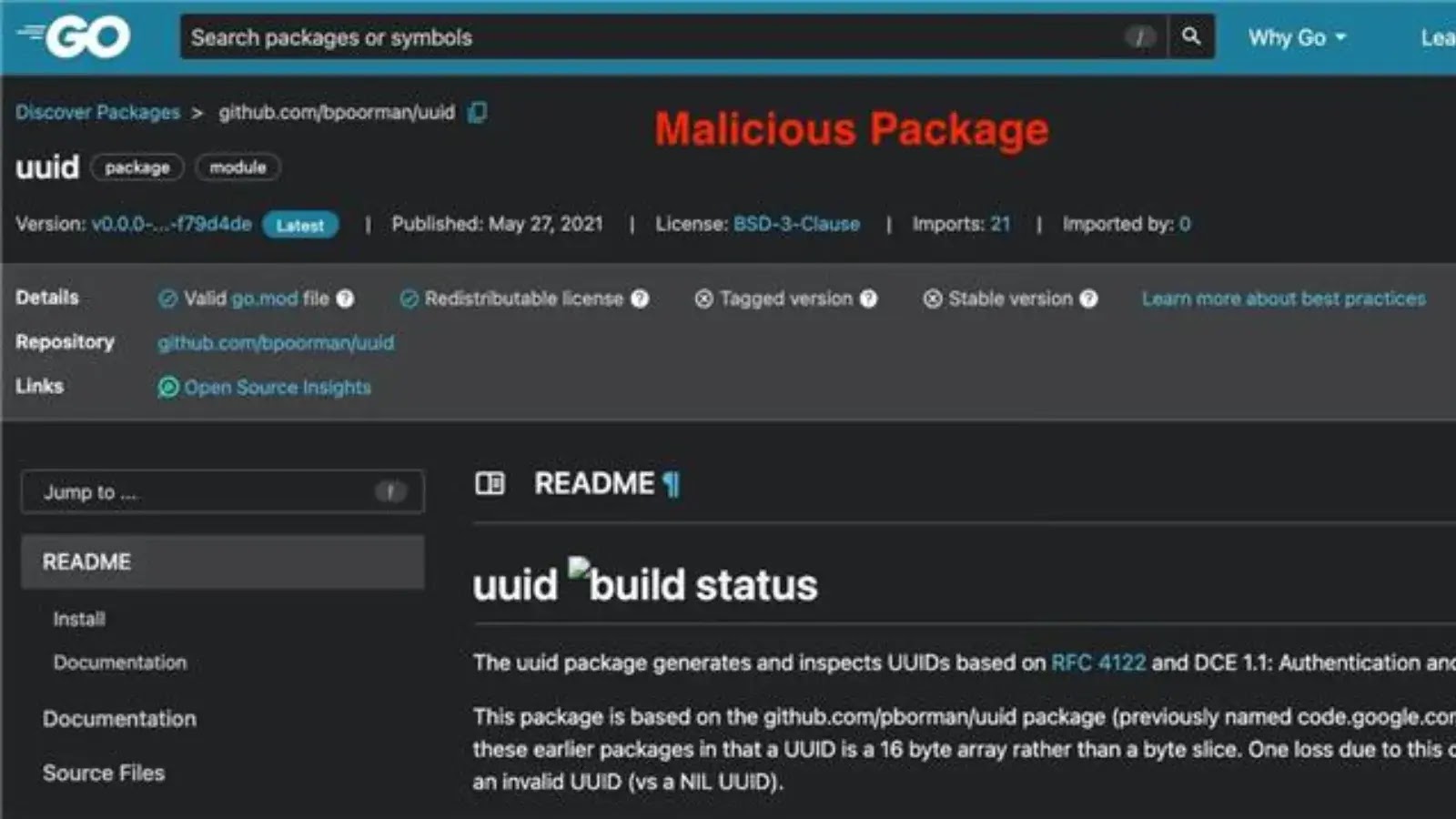
The Silent Threat: Malicious Go Packages Mimicking Google’s UUID Library In the vast landscape of software development, the efficiency and reusability offered by open-source libraries [...]
In the high-stakes world of cybersecurity, a disturbing trend has persisted despite international sanctions: commercial spyware companies relentlessly developing and deploying sophisticated tools to compromise [...]
The cybersecurity landscape has been rocked by recent developments concerning a critical remote code execution (RCE) vulnerability, now actively exploited in the wild. Tracked as [...]
Unmasking Calisto: Russian FSB’s Persistent Cyber Espionage Operations In the high-stakes world of international relations, cyber espionage remains a silent, yet potent, weapon. Recent [...]
In the high-stakes world of cybersecurity, understanding the tactics of nation-state threat actors is paramount. A disturbing trend has emerged, with Russian-linked advanced persistent [...]
Proactive Protection: NCSC’s New Notification Service Fortifies UK Cyber Defenses The landscape of cyber threats is relentless, with adversaries constantly seeking vulnerabilities to compromise [...]
A disturbing new threat has emerged for organizations relying on Apache Tika: a critical vulnerability that attackers can exploit simply by uploading a specially crafted [...]
The Deceptive Lure: How Threat Actors Weaponize Microsoft Teams Notifications for Callback Phishing The digital workplace, a hub of collaboration and efficiency, is increasingly [...]