The digital espionage landscape is under constant siege, with sophisticated threat actors continually refining their tactics. A disturbing new development has emerged with the highly [...]
The Indispensable Role of Enterprise Remote Access Software in 2025 Modern business operations are irreversibly shaped by hybrid and remote work models. This fundamental shift [...]
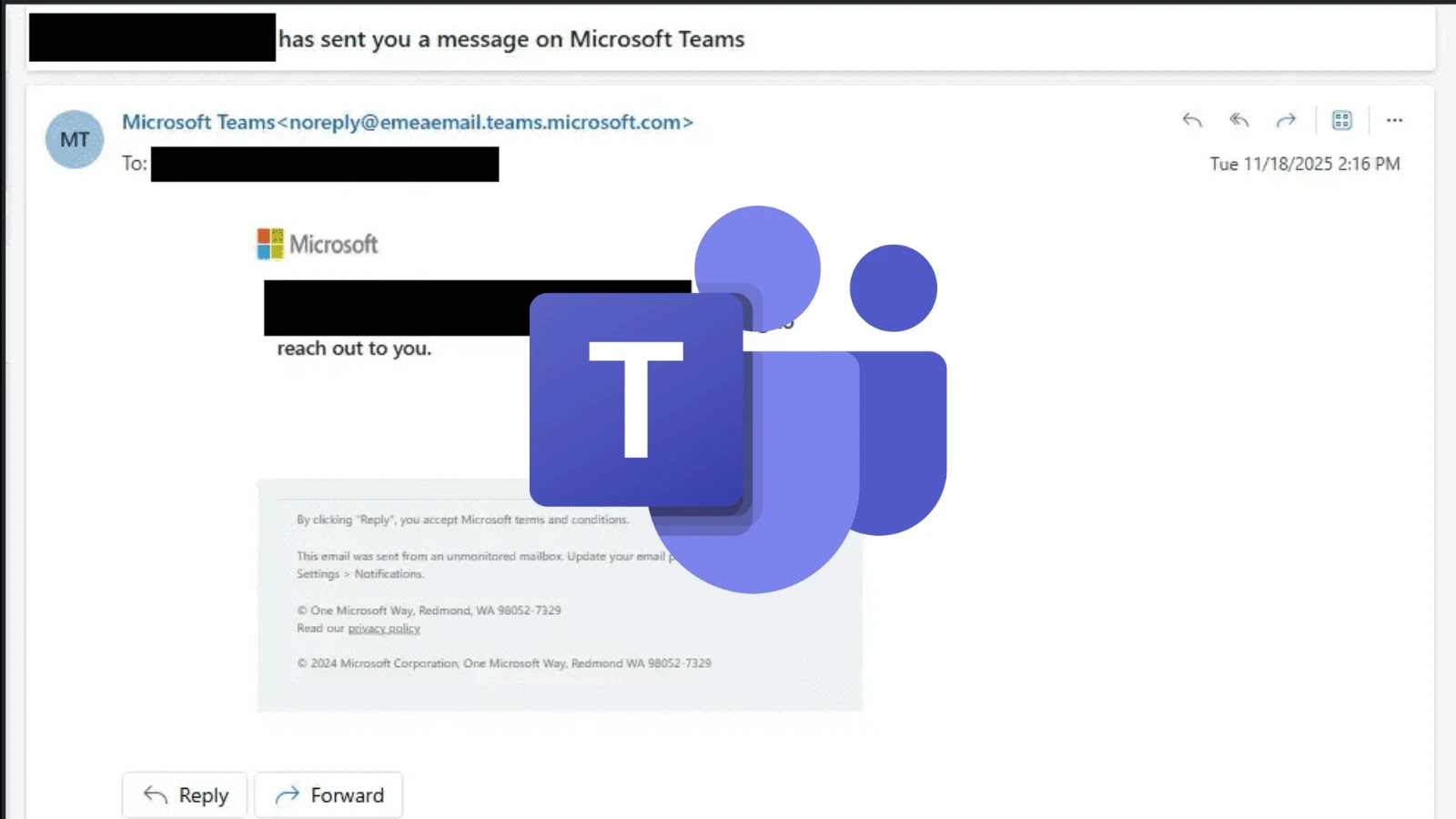
Unmasking the Microsoft Teams Guest Chat Vulnerability: A Gateway for Malware In the interconnected world of modern business, collaboration platforms like Microsoft Teams are [...]
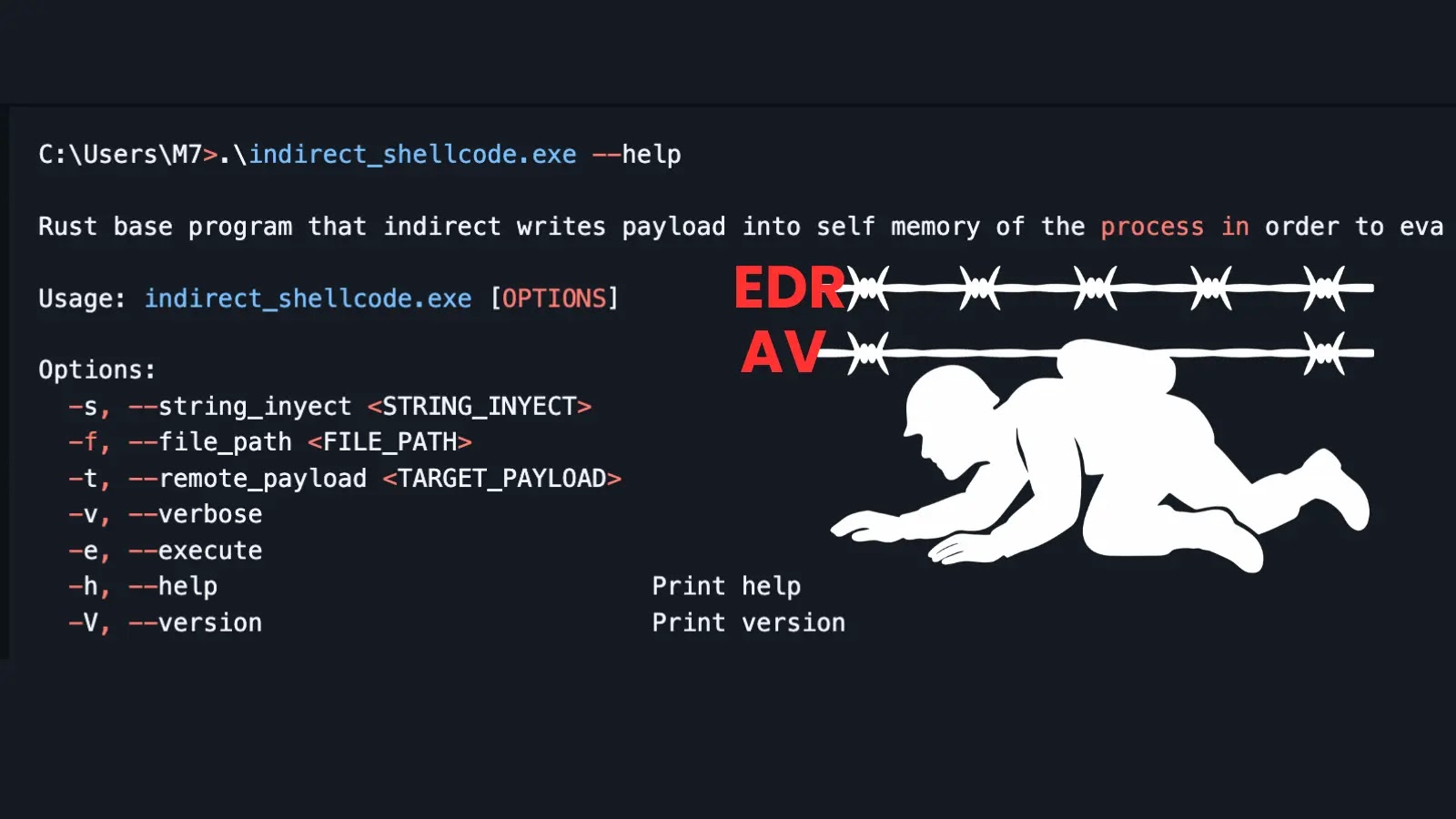
A disturbing new development in offensive security is challenging the effectiveness of modern Endpoint Detection and Response (EDR) and antivirus (AV) solutions. A novel tool, [...]
The dark corners of the internet are often where innovation takes its most sinister turn. We’ve witnessed the evolution of malware, phishing tactics, and ransomware, [...]
The digital landscape is a battleground, and threat actors are relentlessly seeking new vulnerabilities. A particularly insidious development has surfaced: the Akira ransomware group [...]
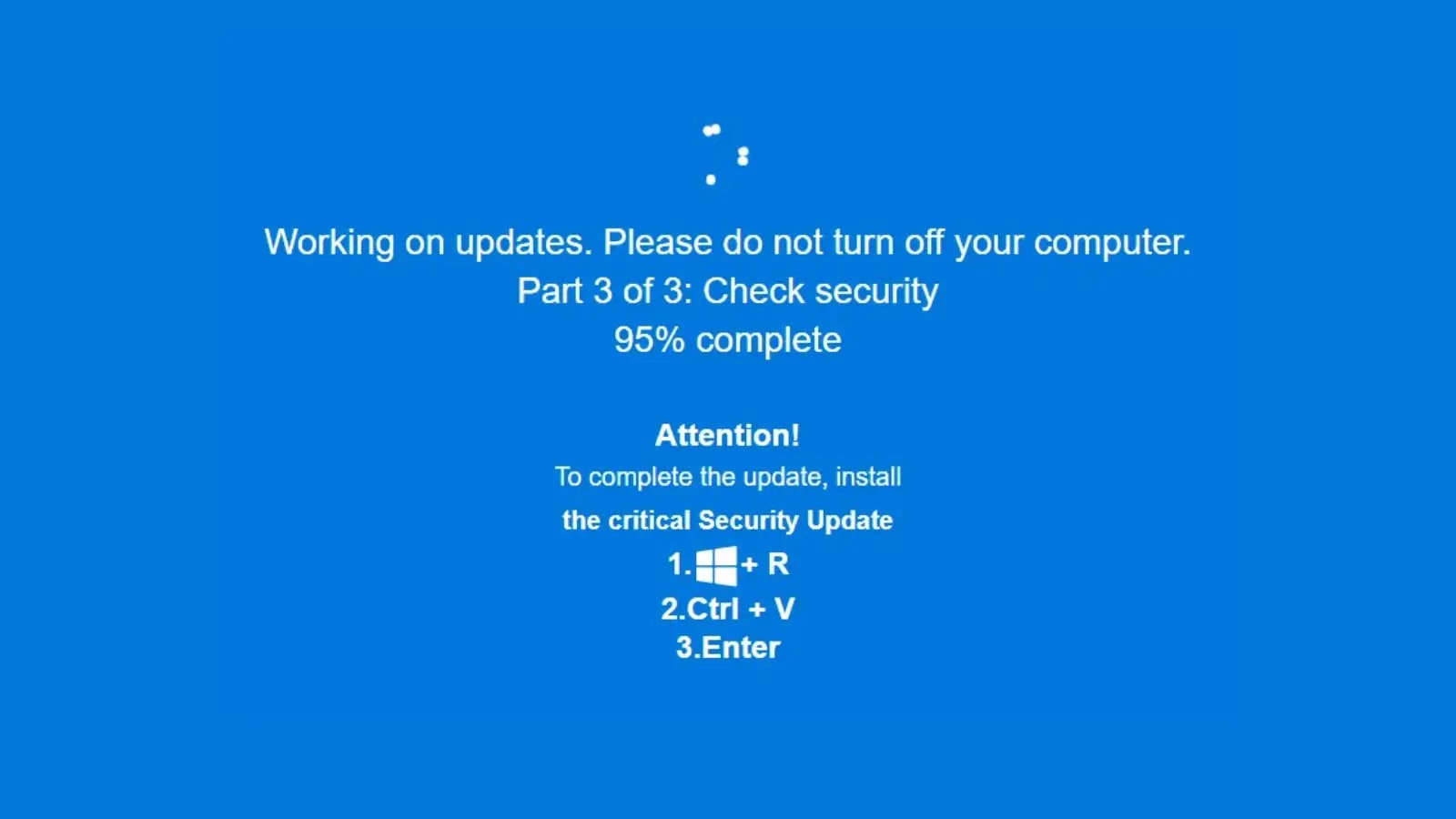
Unmasking JackFix: How Malicious Actors Weaponize Windows Updates The digital threat landscape is perpetually shifting, with adversaries continually innovating to breach defenses. A new, [...]
The Persistent Peril: NTLM Authentication Flaws and Ongoing Windows System Compromise The digital landscape is a battleground where old vulnerabilities often resurface with new [...]
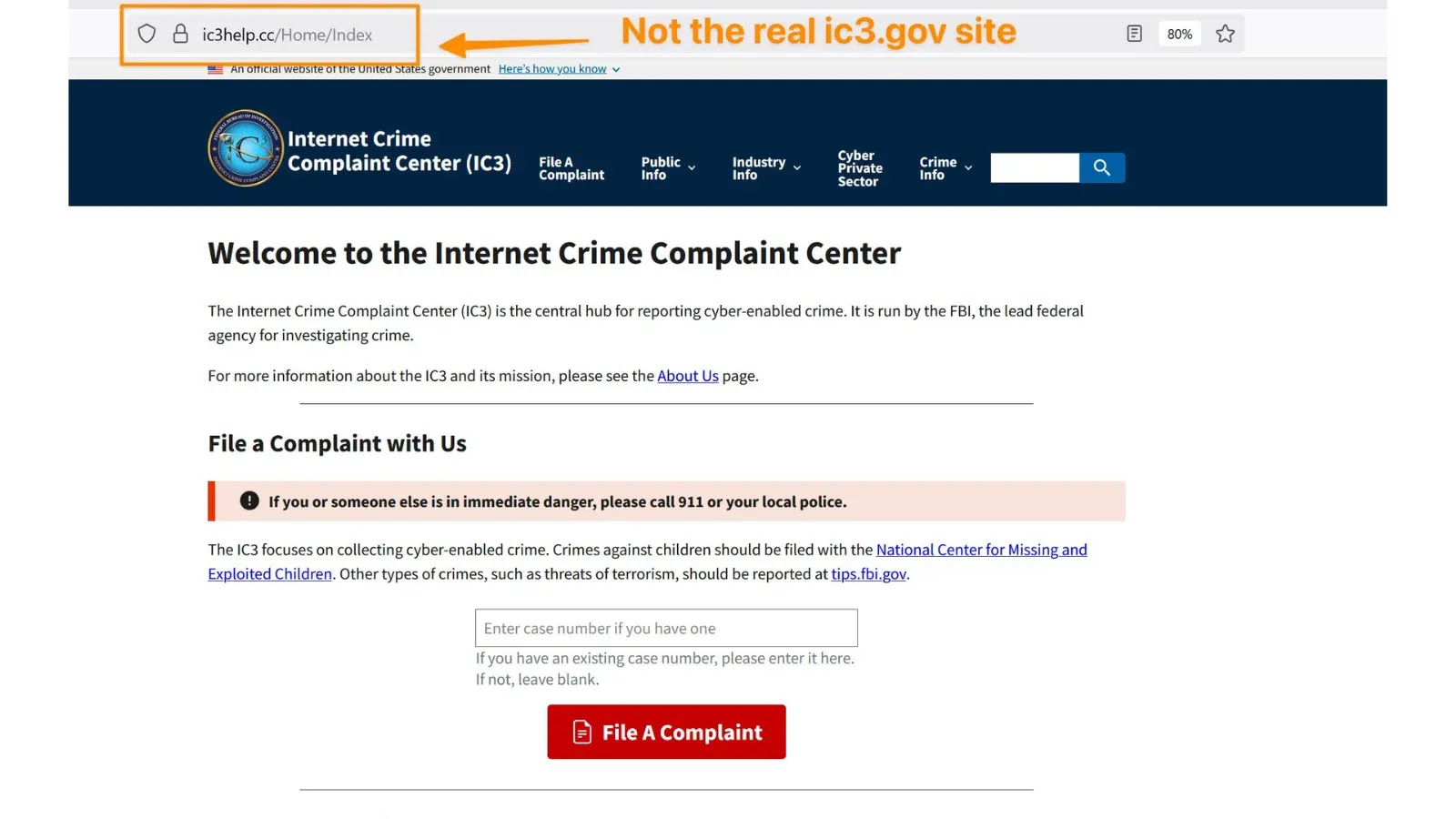
The digital landscape is a constant battleground, and even the most trusted entities can be weaponized by cybercriminals. The Federal Bureau of Investigation (FBI) [...]
The ubiquity of developer tools, especially sophisticated Integrated Development Environments (IDEs) like Visual Studio Code (VS Code), makes them prime targets for malicious actors. [...]