Another day, another grim reminder of the persistent threats lurking within our digital lives. Delta Dental of Virginia, a non-profit dental insurance provider, recently [...]
In the dynamic realm of cybersecurity, staying ahead of sophisticated threats requires continuous innovation in both defensive and offensive strategies. Penetration testers and red teams [...]
Identity and Access Management (IAM) systems are the linchpin of modern security, controlling who can access what resources within an organization. When vulnerabilities emerge [...]
The landscape of cyber threats has fundamentally shifted. Traditional defenses, reliant on signature-based detection and file-centric analysis, are increasingly outmatched by sophisticated adversaries employing fileless [...]
Canon Caught in Clop Ransomware Net via Oracle E-Business Suite 0-Day: A Deep Dive The digital threat landscape continues its relentless expansion, and the [...]
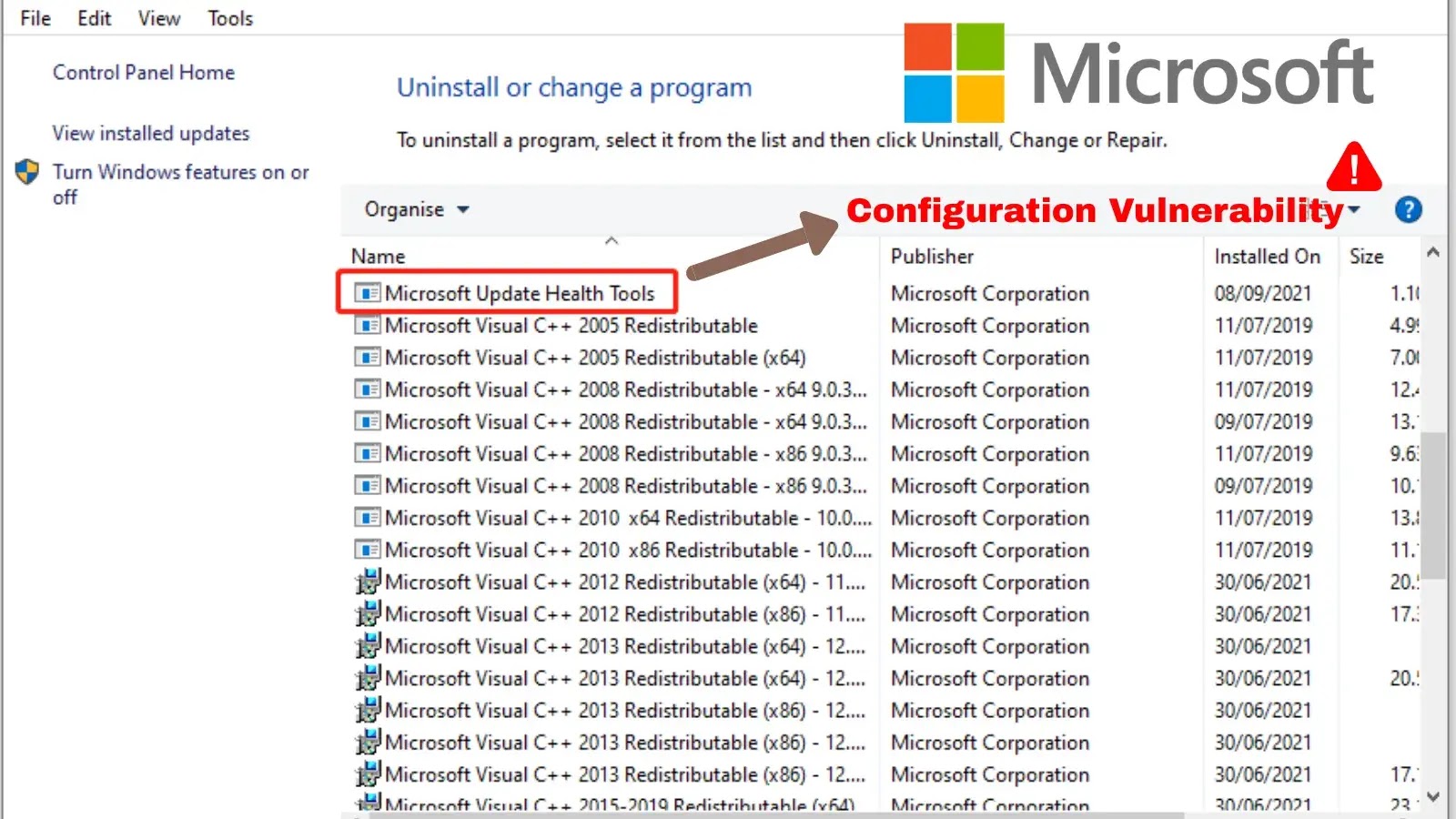
Unpacking a Critical Flaw: RCE in Microsoft’s Update Health Tools The intricate dance between maintaining a secure IT environment and ensuring operational efficiency often [...]
Critical HashiCorp Vault Vulnerability: Unauthenticated Access via Terraform Provider Flaw A severe security vulnerability has been identified within HashiCorp’s Vault Terraform Provider, posing a [...]
Navigating the Evolving Threat Landscape: The Imperative of Exposure Management The cybersecurity paradigm has shifted. Reactive defense, characterized by perimeter security and incident response, is [...]
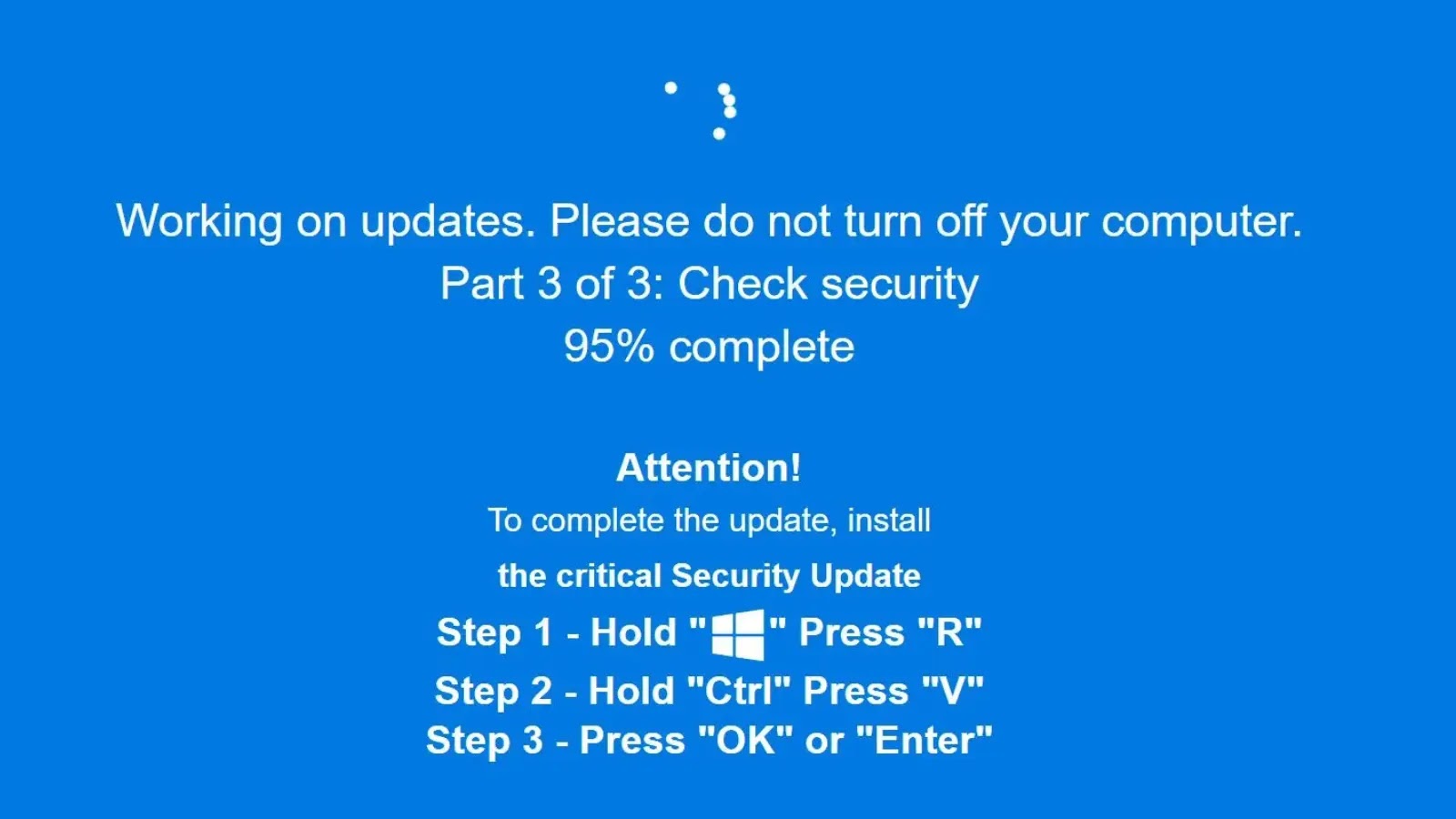
The Devious Disguise: ClickFix Attack Hides Malware in Fake Windows Updates via Steganography A new, highly concerning cyber threat has emerged, leveraging sophisticated social [...]
The AI Paradox: How GPT-3.5 and GPT-4 Are Fueling Autonomous Malware The landscape of cyber warfare is undergoing a seismic shift. Large Language Models [...]