A disturbing trend in software supply chain attacks has emerged, directly targeting users and their valuable cryptocurrency assets. The seemingly innocuous act of installing [...]
In the intricate landscape of enterprise cybersecurity, internal communications remain the lifeblood of organizations. Email, whether hosted on-premises via Microsoft Exchange or leveraging cloud [...]
Unmasking EtherHiding: A New Era of Web-Based Malware Delivery The digital threat landscape is in a constant state of flux, with malicious actors continuously [...]
Unpatched Tenda N300 Routers: A Root-Level Command Injection Catastrophe The security of our home networks often hinges on the devices that connect us to [...]
The veil has been lifted on one of the most prolific state-sponsored advanced persistent threat (APT) groups. In a groundbreaking revelation that sent ripples through [...]
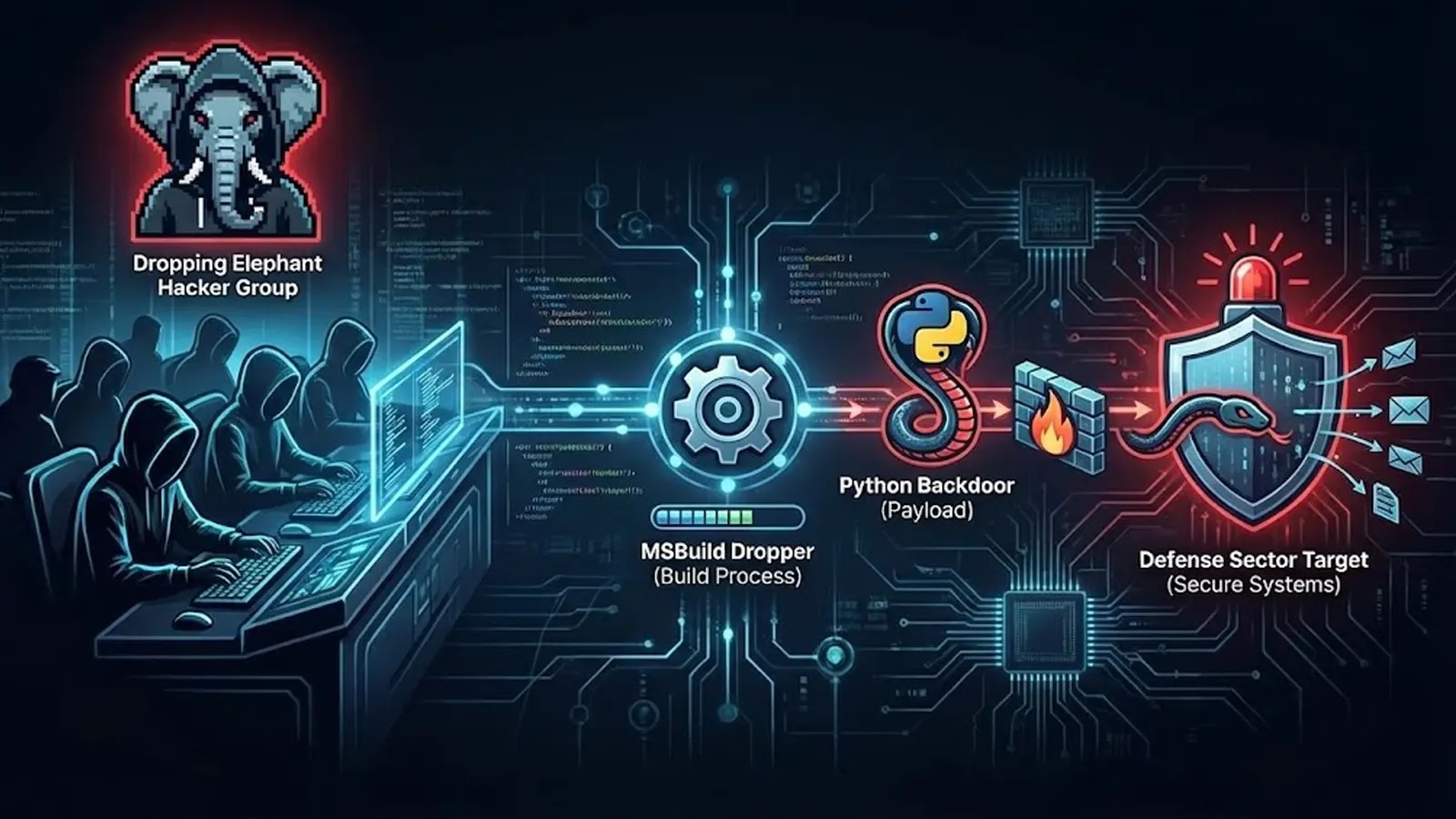
Cyber warfare is a relentless, shadow conflict, and the recent activities of the “Dropping Elephant” threat group underscore its escalating sophistication. This India-aligned adversary has [...]
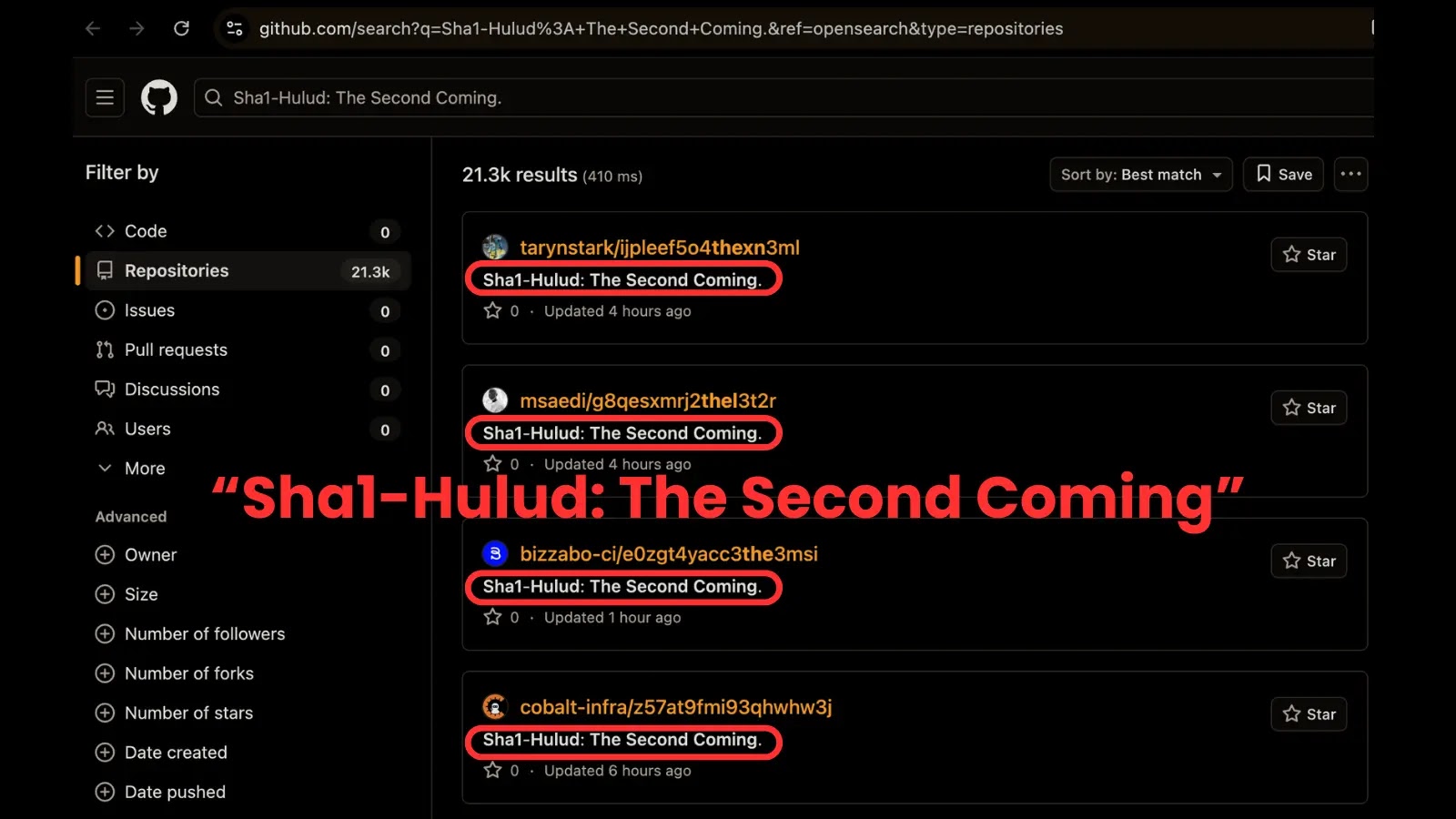
Sha1-Hulud Returns: Unpacking a Critical Supply Chain Attack on npm and GitHub The open-source ecosystem, a cornerstone of modern software development, is under renewed [...]
A disturbing new cyber campaign is exploiting the trust users place in their WhatsApp contacts, silently siphoning off sensitive data and financial information. This [...]
A troubling development has emerged for over a million WordPress websites: a public Proof-of-Concept (PoC) exploit has been released for a critical vulnerability in W3 [...]
The Shifting Sands of Cloud Security: From Reaction to Preemption In the relentlessly expanding cloud landscape, traditional security models often find themselves playing catch-up. [...]