—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Cross-Site Scripting Vulnerabilities in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: MEDIUM Systems Affected Cisco Packaged [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Remote Code Execution Vulnerability in CISCO Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Systems Affected Unified [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Denial of service Vulnerability in PAN-OS Firewall Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]
Navigating the Data Security Landscape in 2026: An Imperative for Businesses The year 2026 presents a cybersecurity panorama defined by escalating threats, stringent regulatory frameworks, [...]
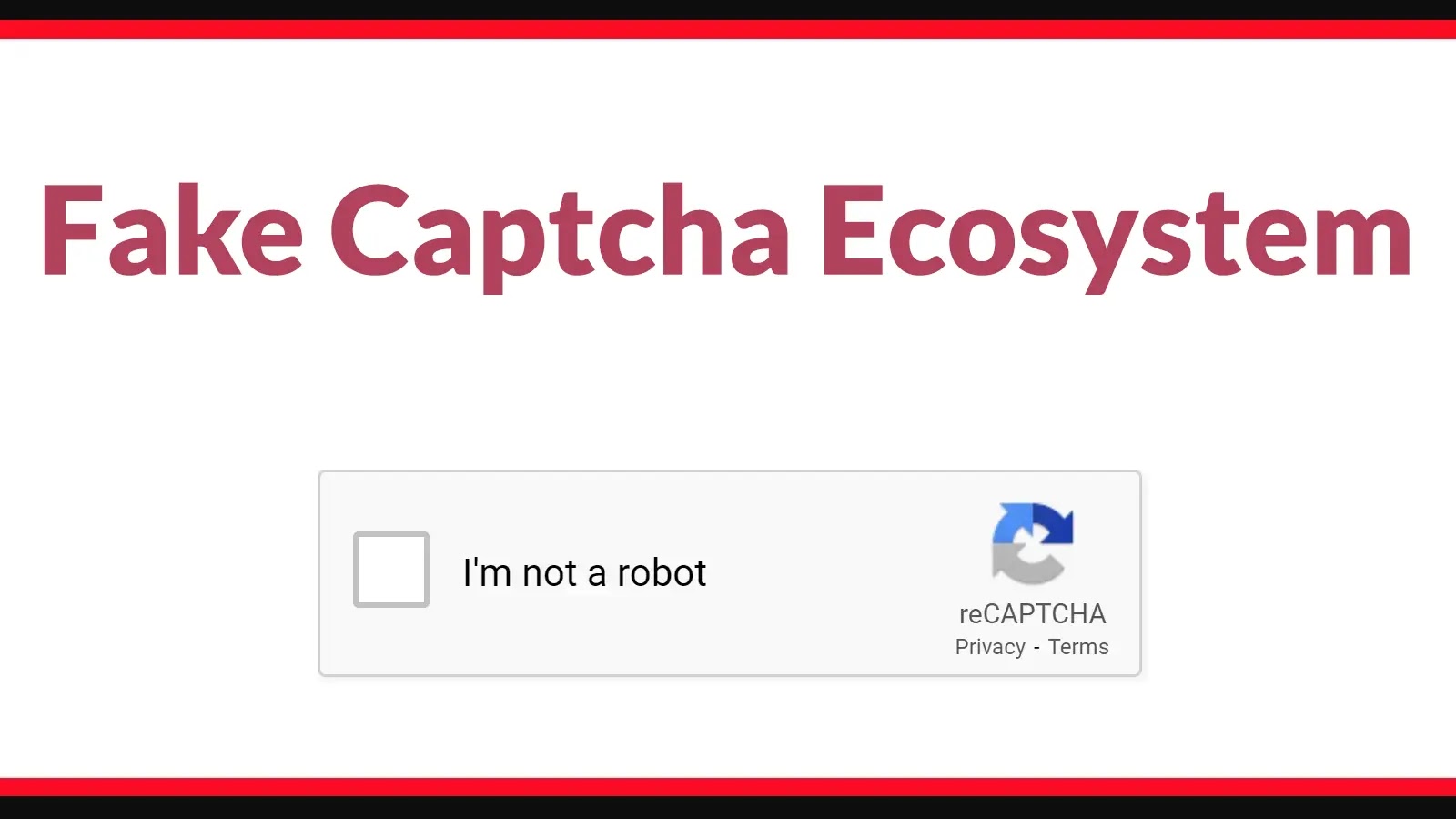
The digital threat landscape is in constant flux, but a new, particularly insidious danger has emerged: the weaponization of generative AI to transform benign web [...]
A new, dangerous macOS infostealer dubbed MacSync is actively targeting cryptocurrency users, employing a sophisticated social engineering tactic that bypasses traditional security measures. This affordable [...]
The web is a vast, interconnected space, and with its convenience comes the constant need for verification. We encounter CAPTCHAs and security checks daily, a [...]
A Critical Flaw: Backdoor Vulnerability Impacts 20,000 WordPress Sites The digital landscape is a relentless battlefield, and even the most popular platforms are not immune [...]
LNK File Weaponization: North Korean Threat Actors Deploy MoonPeak Malware on Windows Systems In a pressing development for cybersecurity, threat actors, reportedly linked to North [...]
The lines between privacy and national security are constantly redrawn, especially when cutting-edge technology intersects with legal investigations. A recent development stemming from a massive [...]