Shipping documents, the mundane workhorses of global commerce, are now being weaponized in a highly effective and stealthy cyberattack campaign. Threat actors are exploiting [...]
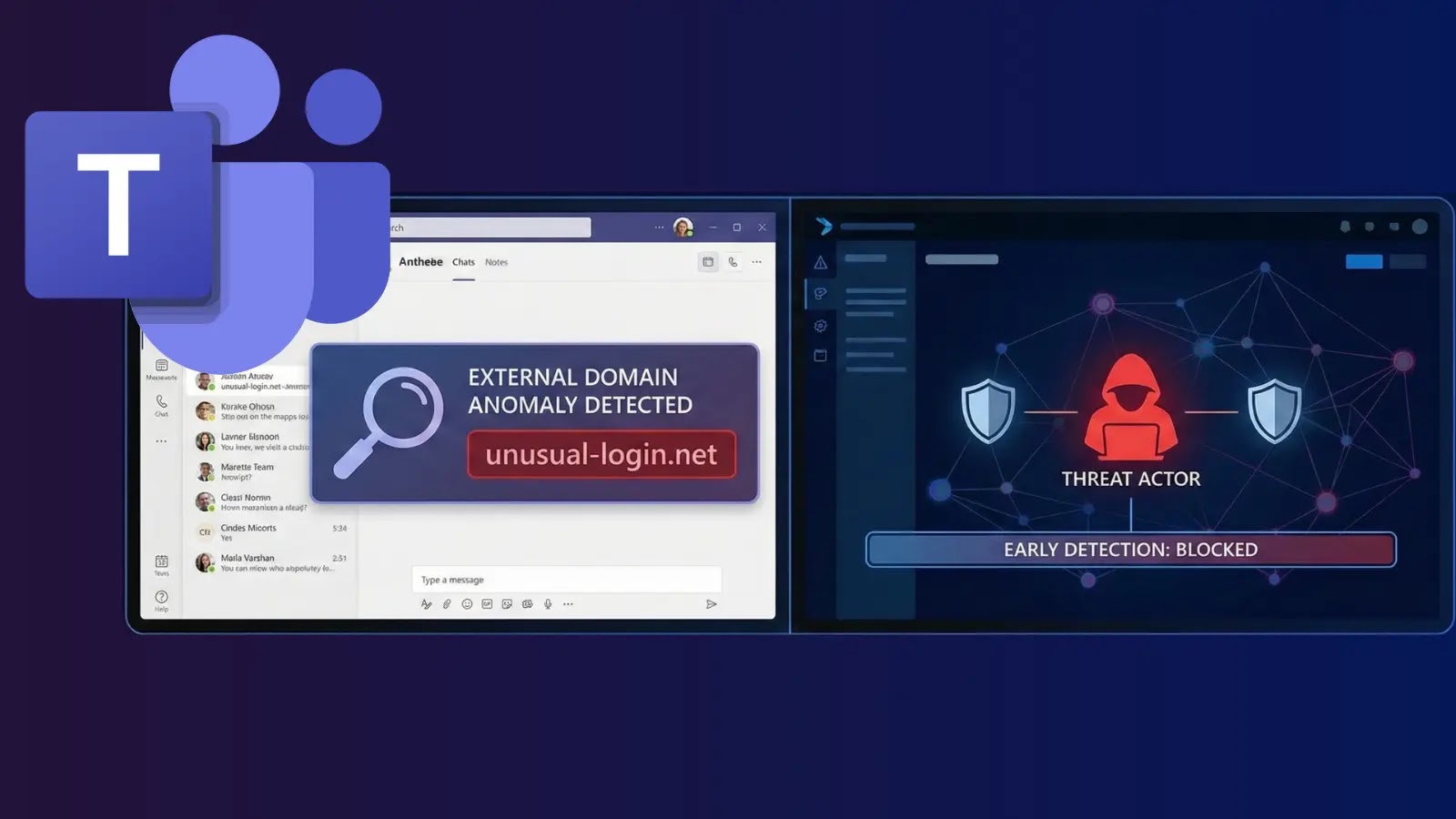
Unmasking Malicious Activity: How Microsoft Teams’ External Domain Anomalies Report Fortifies Your Defenses Modern enterprises rely heavily on collaborative platforms like Microsoft Teams, but [...]
The Trojan in the IDE: North Korean Hackers Weaponize Visual Studio Code The digital battleground continues to shift, and threat actors, particularly those sponsored by [...]
A disturbing trend has emerged in the cybersecurity landscape: attackers are increasingly leveraging the professional credibility of LinkedIn to infiltrate corporate environments. A sophisticated [...]
A critical vulnerability has emerged, striking at the heart of enterprise infrastructure relying on Oracle’s Fusion Middleware. Specifically targeting the Oracle HTTP Server and [...]
Imagine your critical Azure services – Key Vaults safeguarding secrets, CosmosDB powering your applications, or even your Azure OpenAI instances – suddenly becoming inaccessible. This [...]
Unauthenticated Root Access: Unpacking the Critical GNU InetUtils Vulnerability Imagine a scenario where a malicious actor can gain complete control over your critical systems [...]
Google Chrome 144: A Critical Security Update for V8 The digital landscape demands constant vigilance, especially when it comes to the tools we use [...]
The digital frontier is constantly under siege, and the latest alarm comes directly from the Cybersecurity and Infrastructure Security Agency (CISA). In a recent, critical [...]
A disturbing claim has emerged from the dark web, with the notorious Everest ransomware group allegedly announcing a significant cyberattack on McDonald’s India. This [...]