A disturbing claim has emerged from the dark web, with the notorious Everest ransomware group allegedly announcing a significant cyberattack on McDonald’s India. This [...]
Supreme Court Document Leak: Hacker Pleads Guilty to Federal Charges The integrity of government digital infrastructure is under constant assault, a reality starkly highlighted [...]
Unmasking the WhisperPair Flaw: Introducing WPair, the Essential Scanner Tool In an increasingly interconnected world, the convenience of seamless device pairing often comes with [...]
New Spear Phishing Attack Leveraging Argentine Federal Court Rulings to Covert RAT for Remote Access
A disturbing new spear-phishing campaign has cast a harsh light on the persistent threat of sophisticated social engineering, particularly when targeting high-value sectors. This [...]
A disturbing new development has sent ripples through the cybersecurity community: advanced language models, particularly versions built on GPT-5.2, can now reliably develop functional [...]
The digital landscape is a constant battleground, and a recent, urgent alert sent shivers through the UK’s cybersecurity community. On January 19, 2026, the National [...]
Gootloader’s Stealthy Resurgence: A Low Detection Threat Bypassing Security Tools The cybersecurity landscape is a constant arms race, and recent intelligence indicates a concerning re-emergence. [...]
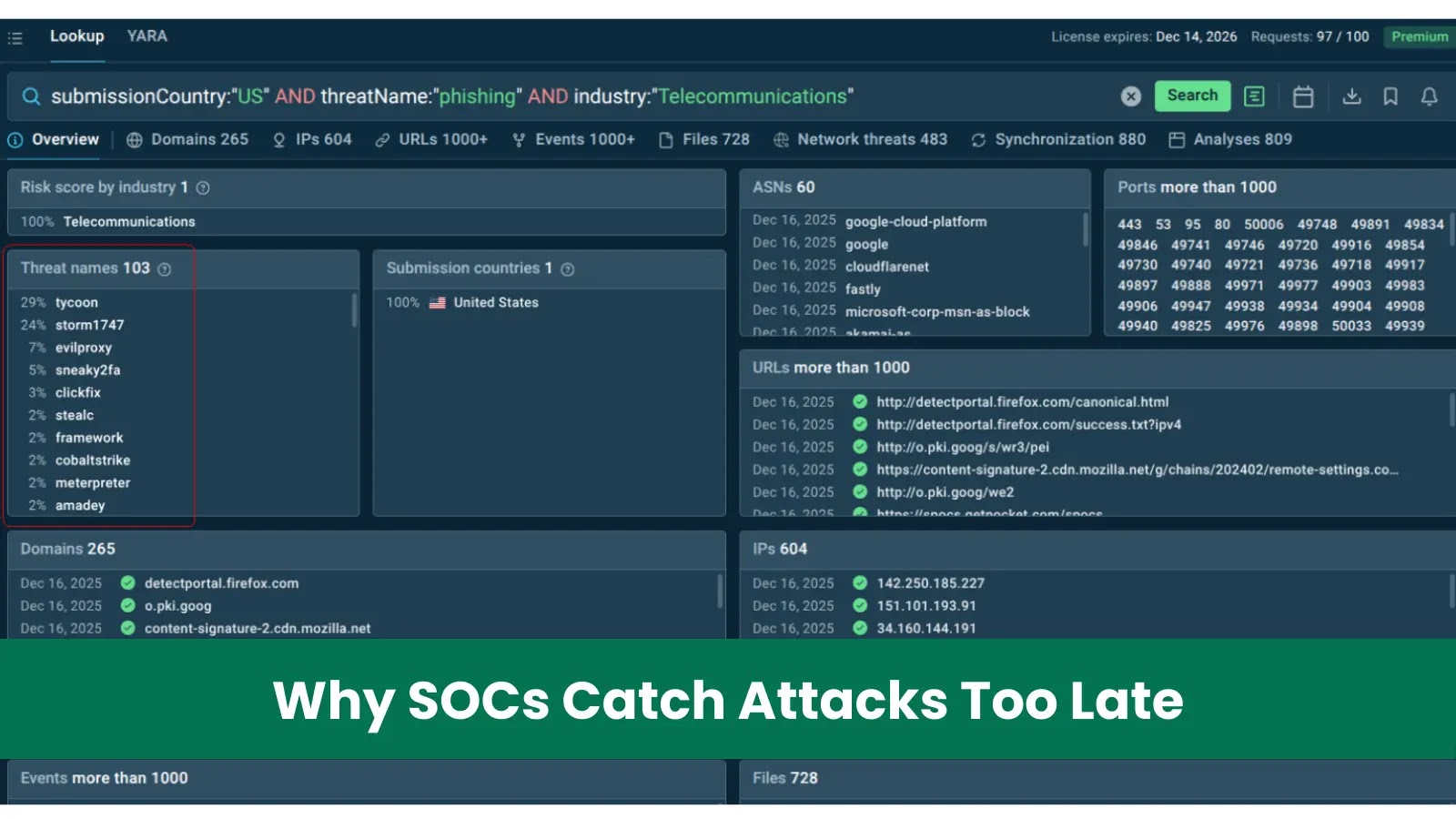
The Costly Reality: Why Delayed Attack Detection Plagues Most SOCs The stark truth for many Security Operations Centers (SOCs) is that they’re consistently a [...]
Critical WordPress Plugin Flaw: Over 100,000 Sites at Risk of Full Takeover A severe vulnerability has surfaced in the widely used Advanced Custom Fields: Extended [...]
Unmasking the Threat: Apache Airflow Vulnerabilities Expose Sensitive Data Data orchestration platforms like Apache Airflow are the backbone of modern data pipelines, managing complex workflows [...]