In a stark reminder that even the oldest digital skeletons can rattle the foundations of modern security, a newly confirmed vulnerability in the Telnet daemon [...]
Unmasking Decade-Long Espionage: Google Dismantles Chinese Hacking Infrastructure The digital shadows have once again been illuminated, revealing a highly sophisticated and disturbingly pervasive cyber [...]
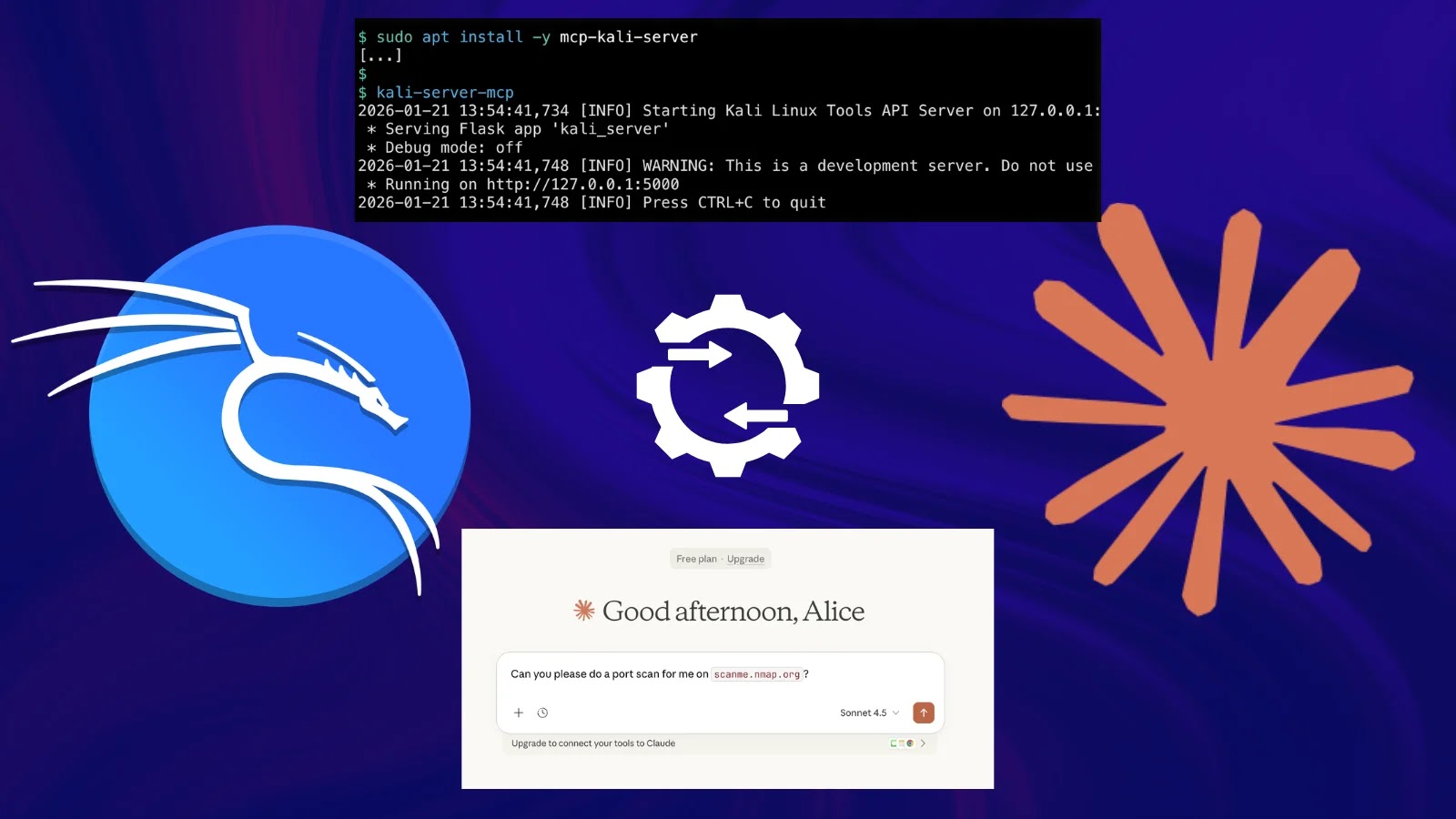
Unveiling the Future of Penetration Testing: Kali Linux Integrates Claude AI The landscape of cybersecurity is constantly reshaped by innovation. For penetration testers, the [...]
Unmasking SURXRAT: A New Android Threat Landscape The mobile threat landscape is undergoing a significant transformation. We’re observing a clear shift towards highly professionalized [...]
The digital landscape is a constant battleground, where cybercriminals relentlessly evolve their tactics to exploit the trust users place in legitimate brands. A particularly sophisticated [...]
The landscape of cybersecurity is a perpetual cat-and-mouse game, and a recent disclosure has unveiled a concerning new tactic that threat actors could exploit. Researchers [...]
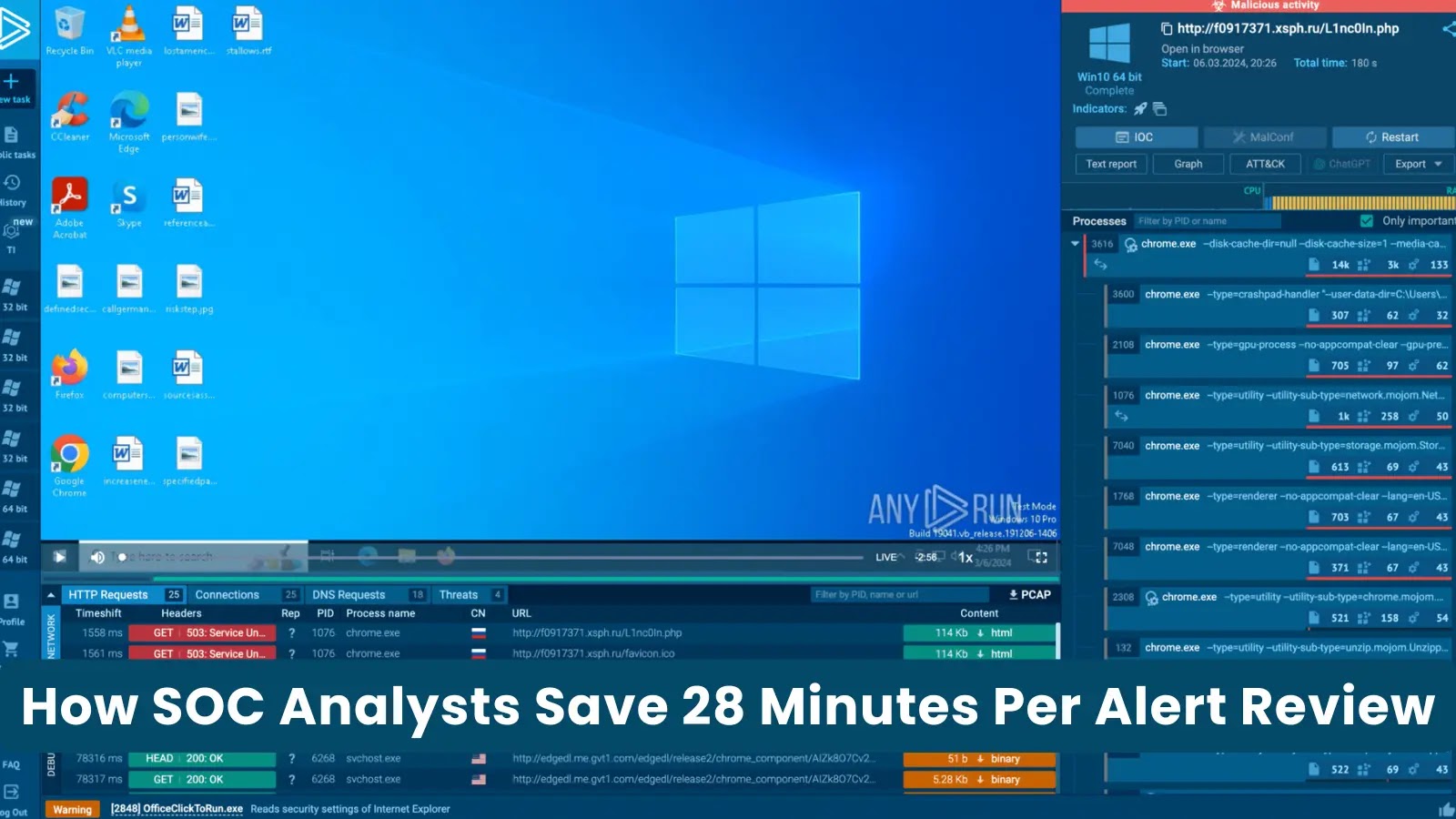
In the high-stakes world of cybersecurity, time is a critical differentiator between proactive defense and reactive damage control. For Security Operations Center (SOC) analysts, the [...]
Hacker Jailbreaks Claude AI: Unprecedented AI Exploitation for Government Data Theft The landscape of cyber warfare just shifted dramatically. A recent report has unveiled [...]
Navigating the Evolving Threat Landscape: OAuth Attacks and Entra ID Compromises In the complex ecosystem of cloud security, threat actors consistently adapt their techniques to [...]
Urgent Alert: Cisco SD-WAN 0-Day Vulnerability Actively Exploited Since 2023 for Root Access A critical zero-day vulnerability in Cisco Catalyst SD-WAN products has been [...]