“Zero trust” security is a cybersecurity approach that challenges the traditional notion of “trust but verify.” In a zero trust model, organizations operate under the [...]
How can PAM/PAS solutions integrate with cloud environments and hybrid infrastructures? In today’s fast-paced and interconnected world, businesses are increasingly adopting cloud environments and hybrid [...]
Creating an Efficient and Agile Remote Workforce with VPNs. Creating an efficient and agile remote workforce with VPNs (Virtual Private Networks) can significantly enhance productivity, [...]
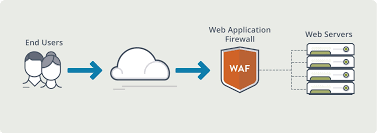
1. What is meany by WAF? A firewall that monitors, filters, and stops HTTP traffic going to and from a website or web application is [...]
What is VPN? VPN stands for Virtual Private Network. It is a technology that allows users to create a secure and encrypted connection over a [...]
What is a Proxy Server and how do they protect the computer network? A Proxy Server is an intermediary server that acts as a gateway [...]
How can you secure a Wi-Fi network using encryption and authentication methods? Securing a Wi-Fi network is crucial to prevent unauthorized access and protect sensitive [...]
What is meant by PAS? (Privileged Access Security) Privileged Access Security (PAS) refers to the set of technologies, practices, and policies designed to protect and [...]
What is CASB? The role of CASBs in SASE dominated future. A cloud access security broker (CASB) is an on-premises or cloud-based security policy enforcement point [...]
Description about Sophos Firewalls and What are the features in it? What is Sophos Firewall? Sophos is a well-known cybersecurity company that offers a range [...]