IoT Security at the Edge Computing: Securing Industrial IoT Edge Devices In the rapidly evolving landscape of the Industrial Internet of Things (IIoT), securing IoT [...]
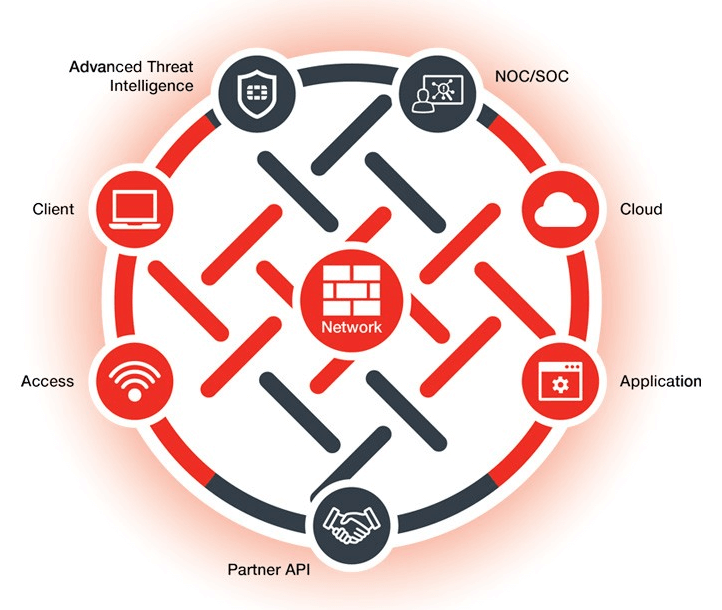
Fortinet FortiSIEM: Security Information and Event Management Peer Insights In the evolving landscape of cybersecurity, understanding the capabilities and benefits of robust solutions like Fortinet [...]
Cross-site scripting (XSS) vulnerability in Grafana Cross-site scripting (XSS) vulnerability in Grafana Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Grafana [...]
Identity and Access Management Trends Shaping 2025 The identity and access management landscape is experiencing unprecedented transformation in 2025, driven by sophisticated cyber threats, quantum [...]
Ivanti Releases Critical Security Update for EPMM After Limited Exploits Discovered Ivanti has issued an important security advisory addressing vulnerabilities in open-source libraries used in [...]
5 Must-Have Security Features for Native Apps Native apps are built compatible with a platform or operating system, such as iOS or Android. While unrestricted [...]
The Rise of Ransomware – Strategies to Protect Your Systems Ransomware has emerged as one of the digital age’s most pervasive and financially devastating cyber [...]
Cisco IOS XE Wireless Controllers Vulnerability Enables Full Device Control for Attackers Cisco has disclosed a critical security vulnerability in its IOS XE Wireless LAN [...]
Bridging the Gap – CISOs and CIOs Driving Tech-Driven Security In today’s hyper-connected business landscape, the convergence of technology and security has never been more [...]
VMware Aria Operations Vulnerability Exposes Systems to Privilege Escalation Attacks VMware has issued a critical security advisory (VMSA-2025-0006) addressing a high-severity local privilege escalation vulnerability [...]