Cisco ASA & FTD VPNs Vulnerability Actively Exploited in Attacks Cisco has disclosed a critical vulnerability in its Adaptive Security Appliance (ASA) and Firepower Threat [...]
Cisco ATA 190 Telephone Adapter Flaw Exposes Devices To Remote Takeover Cisco has issued a critical security advisory concerning multiple vulnerabilities in its ATA 190 [...]
What is Banner Grabbing? Types, Features & How it Works! Both hackers and security professionals employ various techniques to gather information about computer systems and [...]
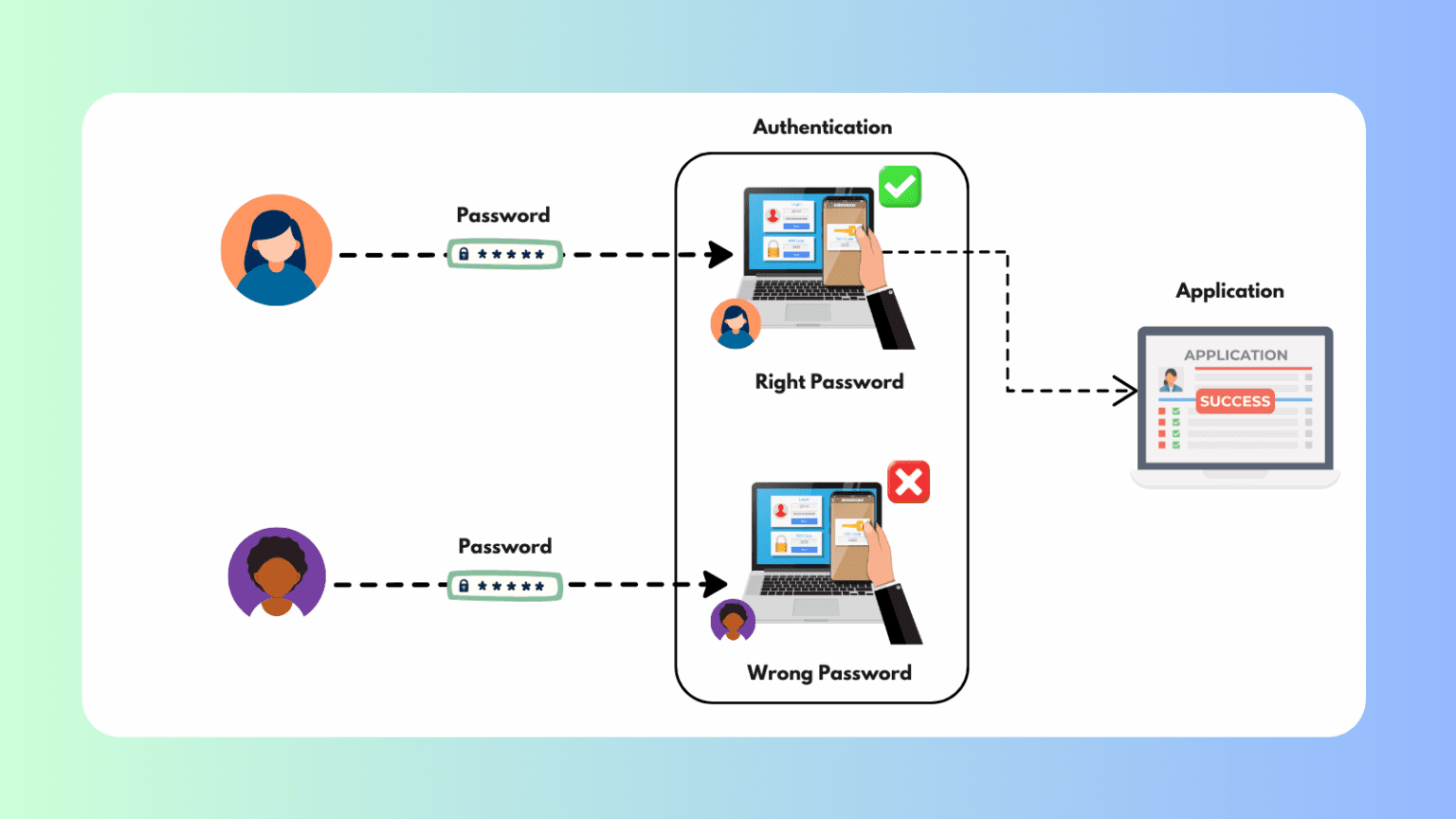
What is Authentication? – Types, Role & How it Works! Authentication is a cornerstone of digital security, serving as the first defense against unauthorized access [...]
Critical Vulnerabilities Impact Millions Of D-Link Routers: Patch Now! In a significant security alert, millions of D-Link routers are at risk due to critical vulnerabilities [...]
CISA Warns of Three Vulnerabilities That Are Actively Exploited in the Wild The Cybersecurity and Infrastructure Security Agency (CISA) has added three new vulnerabilities to [...]
What is Account Harvesting? In today’s digital world, online security is a primary concern for individuals and businesses. One of the most significant threats is [...]
What is an Access Matrix? Access control is fundamental to operating system (OS) security. It ensures that only authorized processes can perform specific actions on [...]
What is Access Management? Access management is an essential aspect of an organization’s security infrastructure, designed to protect and manage access to information and resources. [...]
FireTail Unveils Free Access for All to Cutting-Edge API Security Platform FireTail announces a free version of its enterprise-level API security tools, making them accessible [...]