Imagine your critical network monitoring system, designed to provide visibility and control, suddenly becoming an open door for attackers. This isn’t a hypothetical fear for [...]
The cybersecurity landscape just got a lot more complex for anyone managing Linux servers or IoT devices. Security researchers have uncovered a new, highly sophisticated [...]
The Rise of Evilginx: Bypassing MFA with Advanced Phishing Multi-factor authentication (MFA) has long been lauded as a critical defense against unauthorized access, adding [...]
Critical Zero-Day Flaws Expose PyTorch Models to Arbitrary Code Execution via PickleScan The landscape of artificial intelligence security has been shaken by the discovery [...]
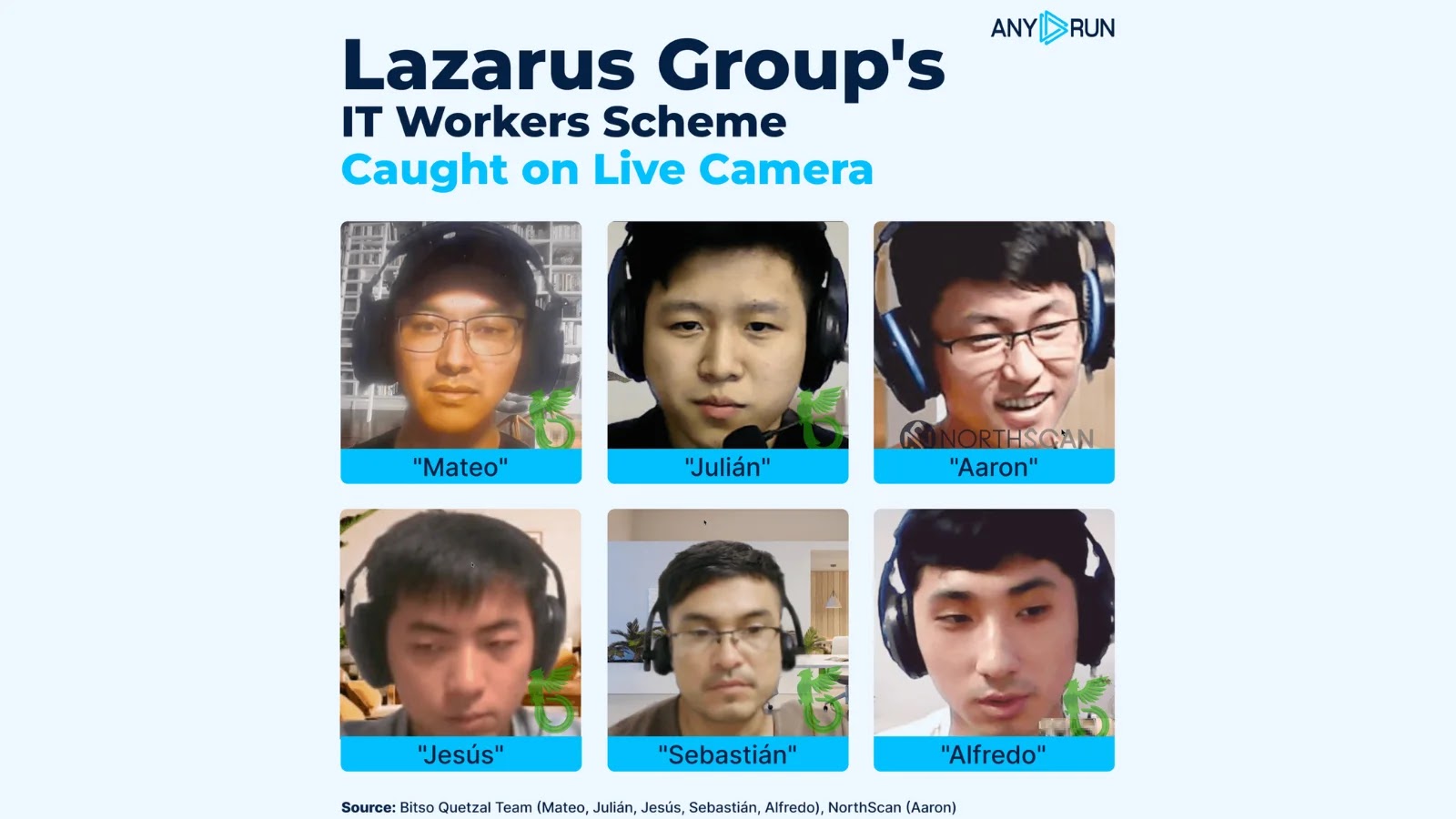
The digital battlefield continues to evolve, and with it, the sophistication of state-sponsored threat actors. One name consistently at the forefront of these discussions [...]
The Temu Tangle: Arizona Accuses E-commerce Giant of Data Theft In an era where personal data is often more valuable than currency, allegations of [...]
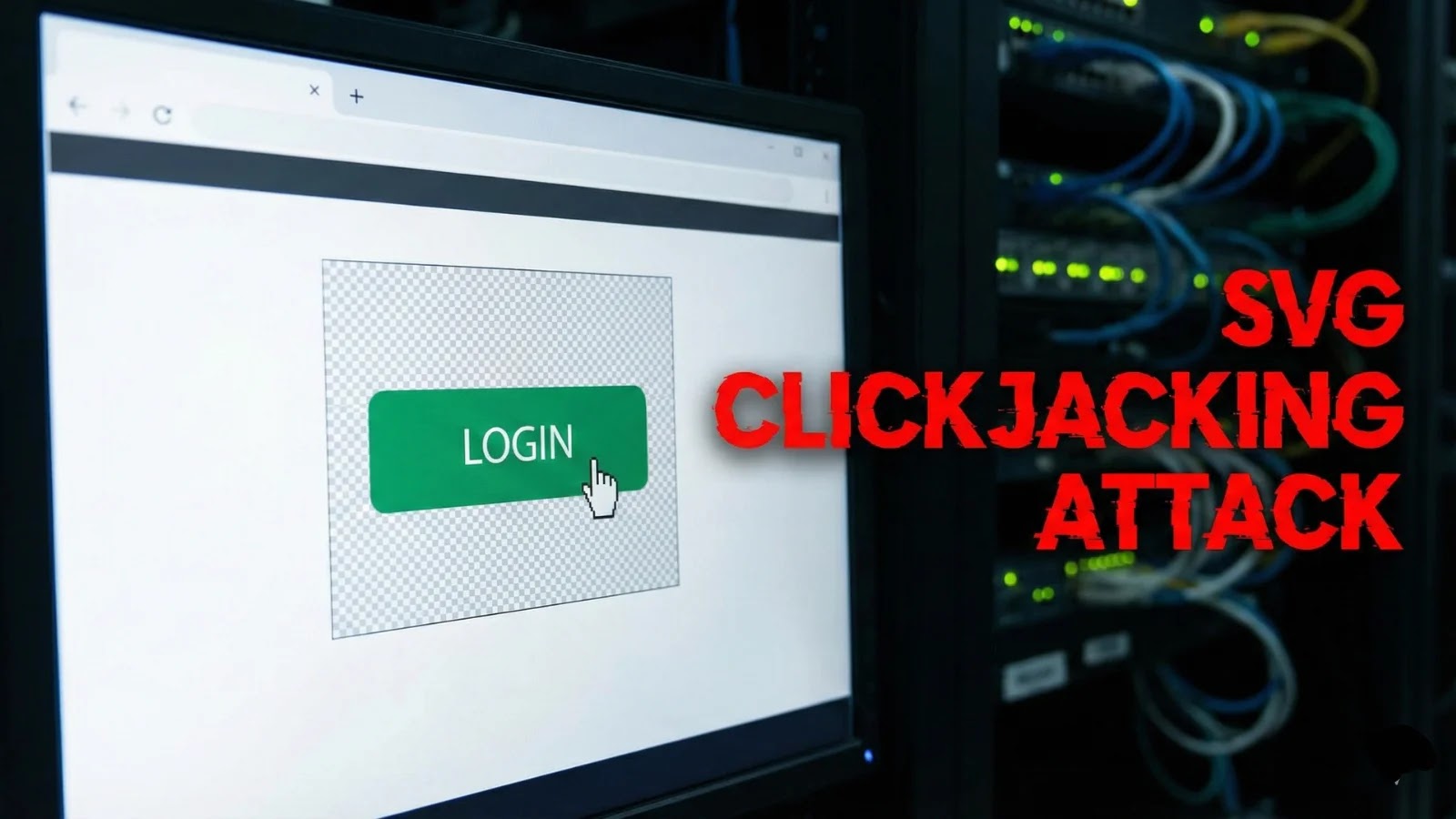
Remember clickjacking? That seemingly antiquated attack where a malicious actor overlays an invisible frame on a legitimate webpage, tricking users into unintended clicks? For years, [...]
The operational technology (OT) landscape faces a relentless barrage of threats, and when critical vulnerabilities in industrial control systems (ICS) are actively exploited, the urgency [...]
The digital corporate landscape, a vibrant hub of innovation and collaboration, is simultaneously a prime target for increasingly sophisticated cyber threats. While discussions often [...]
BRICKSTORM Alert: PRC-backed Malware Targets VMware ESXi and Windows Environments The cybersecurity landscape is under constant siege, and a recent joint advisory from the [...]