PIM vs. PAM vs. IAM: Understanding Privileged Identity Management
In today’s intricate digital landscape, safeguarding an organization’s most critical assets from unauthorized access is a paramount concern for any robust security strategy. This article will thoroughly explore the distinctions and interconnections between Privileged Identity Management (PIM), Privileged Access Management (PAM), and Identity and Access Management (IAM), offering a comprehensive understanding of how these security measures collectively contribute to a formidable security posture. We will delve into their individual functionalities, highlighting how they converge to protect sensitive data and prevent potential security breaches.
Introduction to Privileged Identity Management
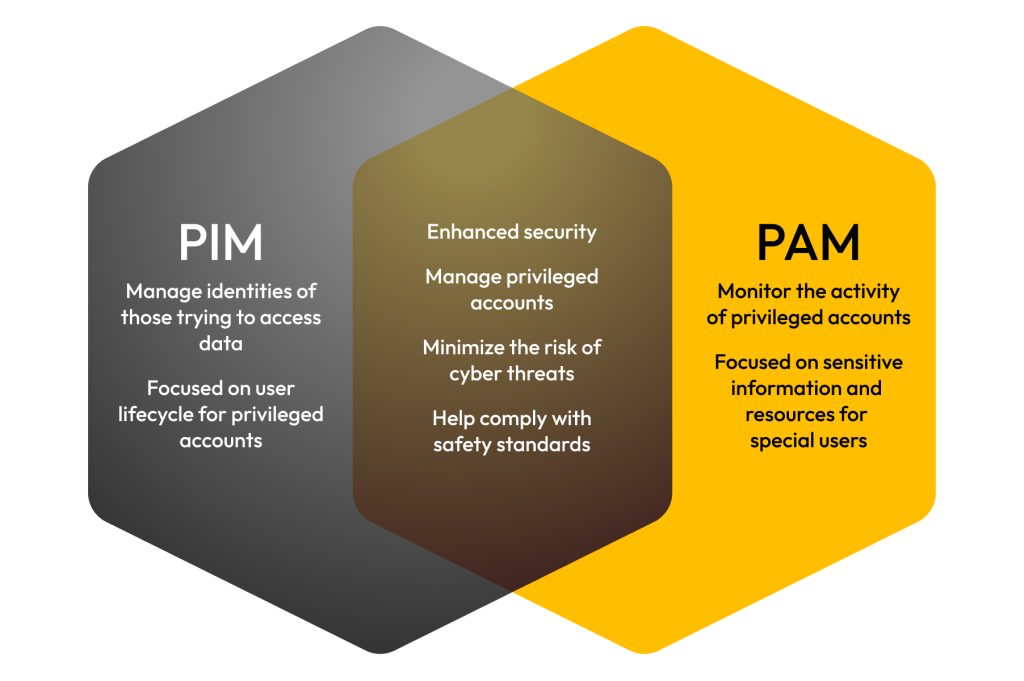
Privileged Identity Management, often abbreviated as PIM, is a crucial component of a comprehensive security strategy designed to secure privileged accounts and the associated sensitive data. It focuses on managing privileged identities within an organization, ensuring that privileged user access is meticulously controlled and monitored. A robust PIM solution is essential for mitigating risks associated with escalated privileges, which can be exploited in security breaches if not properly managed. It addresses the overarching challenge of controlling access to privileged credentials and maintaining the security of privileged sessions.
What is PIM?
PIM focuses on managing privileged identities, which are the non-human and human accounts that possess elevated permissions within an IT environment. This management solution involves the systematic control over the lifecycle of these privileged identities, from their creation to their eventual deprovisioning. A key aspect of a PIM strategy is to ensure that privileged access is only granted when absolutely necessary, adhering to the principle of least privilege. PIM involves comprehensive security measures such as role-based access control and the regular auditing of privileged account activities to prevent potential security breaches and enhance the overall security posture.
What is PAM?
Privileged Access Management, or PAM, is a specialized security discipline and a critical subset of a broader security strategy, directly addressing the secure management of privileged access. Teamwin Global Technologica provides comprehensive PAM solutions as part of a robust suite of IT security solutions, specifically designed to control access to privileged accounts. A PAM solution helps organizations secure privileged credentials and manage privileged sessions, ensuring that only authorized individuals or systems can gain access to privileged IT assets. This approach significantly reduces the risk of credential theft and unauthorized access to sensitive data, fortifying an organization’s security posture.
What is IAM?
Identity and Access Management, or IAM, represents the foundational framework for controlling user access to information and resources across an entire organization. Unlike PIM and PAM, which focus specifically on privileged access, an IAM solution provides a comprehensive security strategy for all user identities, both human and non-human. It encompasses a wide array of security measures, including user provisioning, authentication, authorization, and role-based access control, to ensure that only authenticated and authorized users can access specific resources. IAM serves as the overarching system that manages all identities and their associated access rights, establishing the fundamental security posture for an organization.
Key Differences Between PIM, PAM, and IAM
PIM vs PAM: Understanding the Nuances
While both PIM (Privileged Identity Management) and PAM (Privileged Access Management) are integral to securing sensitive data and privileged accounts, their nuances lie in their specific focus. The core difference between PIM and PAM is that PIM establishes who has the right to a privileged identity, while PAM dictates how and when that identity can exercise its privileged access, thereby enhancing the overall security posture and preventing potential security breaches.
| Acronym | Primary Focus |
|---|---|
| PIM (Privileged Identity Management) | Management of privileged identities themselves, ensuring the lifecycle of these accounts is rigorously controlled and adheres to the principle of least privilege. |
| PAM (Privileged Access Management) | Managing and securing the access to privileged accounts during active privileged sessions, encompassing robust security measures like session monitoring and password vaulting. |
PAM vs IAM: A Comparative Analysis
The distinction between PAM (Privileged Access Management) and IAM (Identity and Access Management) is crucial for a comprehensive security strategy. An IAM solution ensures that only authenticated and authorized users can access specific resources through mechanisms like role-based access control and multi-factor authentication. While IAM manages everyone’s access, PAM specifically secures the keys to the kingdom.
| System | Primary Focus |
| IAM (Identity and Access Management) | Provides the foundational framework for managing all user identities and their corresponding access rights across the entire organization, encompassing both regular and privileged users. |
| PAM (Privileged Access Management) | A specialized subset of IAM, exclusively focused on the highly sensitive area of privileged access. It provides an additional layer of security measures for privileged accounts, which pose the greatest risk if compromised, by managing privileged credentials and controlling access to privileged accounts with enhanced scrutiny. |
PIM vs IAM: Key Differences
The key differences between PIM (Privileged Identity Management) and IAM (Identity and Access Management) further clarify their respective roles within a robust security strategy.
| System | Primary Focus |
|---|---|
| IAM (Identity and Access Management) | Manages all digital identities and their access rights across an organization, from regular employees to applications, providing broad user access control and ensuring that general users can access necessary resources. Ensures comprehensive security for all identities. |
| PIM (Privileged Identity Management) | Narrows its focus specifically on managing privileged identities—those accounts with elevated permissions. Ensures these powerful identities are properly provisioned, deprovisioned, and their use is consistently audited. Concentrates on the most critical identities to enhance the security of privileged assets and sensitive data. |
Components of a Strong Identity and Access Management Solution
Understanding Privileged Accounts
Privileged accounts represent the backbone of an organization’s IT infrastructure, holding elevated permissions that grant extensive control over systems, applications, and sensitive data. These accounts, whether human or non-human, such as service accounts, administrative accounts, or emergency accounts, are prime targets for cyber attackers due to their potential to bypass standard security controls. Understanding the nature and scope of these privileged accounts is the first step in implementing a robust Identity and Access Management (IAM) solution. Effective management of privileged accounts is paramount for maintaining a strong security posture, as their compromise can lead to devastating security breaches and significant financial and reputational damage.
Role of Privileged Users in Security
Privileged users, whether individuals or automated processes, wield significant power within an organization’s IT environment. Their access to privileged accounts allows them to perform critical system configurations, access sensitive data, and manage vital network resources. Given the potential impact of their actions, the role of privileged users in an organization’s security strategy is paramount. A comprehensive PIM and PAM solution ensures that these users operate under strict access control mechanisms, adhering to the principle of least privilege and just-in-time access. Teamwin Global Technologica’s solutions help organizations manage privileged users effectively, preventing unauthorized access and mitigating the risks associated with compromised privileged credentials, thereby fortifying the overall security posture against potential security breaches.
Access Control Mechanisms
Robust access control mechanisms are the foundational pillars of any strong Identity and Access Management (IAM) solution, dictating who can access what resources under what conditions. These mechanisms are crucial for securing privileged accounts and sensitive data within an organization. For privileged user access, advanced access control involves implementing principles such as role-based access control (RBAC), attribute-based access control (ABAC), and least privilege, ensuring that users only have the necessary permissions for their tasks. Within a PIM and PAM framework, these mechanisms are further enhanced with capabilities like privileged session management, multi-factor authentication, and just-in-time access to control access to privileged accounts, thereby significantly strengthening the security posture and reducing the risk of unauthorized access and security breaches.
Implementing Effective PIM and PAM Strategies
Best Practices for Implementing PIM
Implementing a robust PIM (Privileged Identity Management) solution requires adherence to best practices to ensure the comprehensive security of privileged accounts and sensitive data. Organizations should prioritize the principle of least privilege, ensuring that privileged user access is granted only for the duration and scope necessary for a task. Regular audits of privileged identities and privileged sessions are essential to detect and remediate any unauthorized access or suspicious activities. Furthermore, integrating PIM with other security measures such as multi-factor authentication and role-based access control strengthens the overall security posture, mitigating the risk of security breaches and maintaining the integrity of an organization’s critical IT assets.
How PAM Works in Organizations
PAM (Privileged Access Management) operates by establishing a secure, centralized system for controlling and monitoring all privileged access within an organization’s IT environment. A PAM solution typically involves components such as a password vault for managing privileged credentials, session management tools for monitoring and recording privileged sessions, and just-in-time access provisioning. When a privileged user needs to access a critical system, the PAM solution intermediates this access, ensuring that it aligns with predefined security policies. This meticulous control helps organizations enforce the principle of least privilege, preventing unauthorized access to privileged accounts and sensitive data, thereby significantly enhancing the security posture and reducing the likelihood of security breaches.
Integrating IAM with PIM and PAM
The seamless integration of IAM (Identity and Access Management) with PIM (Privileged Identity Management) and PAM (Privileged Access Management) is paramount for a holistic and impenetrable security strategy. IAM serves as the overarching framework, managing all user identities and their baseline access rights, while PIM and PAM layer on specialized controls for highly sensitive privileged accounts. By integrating these systems, organizations can achieve a unified view of all access permissions, ensuring consistent policy enforcement across the entire IT landscape. This synergy allows for centralized management of privileged identities, streamlined access control, and enhanced monitoring of privileged sessions, leading to a significantly improved security posture and reduced exposure to security breaches.
Enhancing Security Posture with IAM, PIM, and PAM
Building an Overall Security Strategy
Building an overall security strategy that effectively leverages IAM, PIM, and PAM is fundamental for safeguarding enterprise data and intellectual property. Teamwin Global Technologica provides a comprehensive suite of IT security solutions designed precisely for this purpose. Their expertise in advanced cybersecurity, threat detection, and secure networking solutions allows for the creation of a robust security posture. By integrating enterprise AI-driven next-generation firewalls, real-time Dark Web monitoring, and managed security services, organizations can establish a proactive defense. This holistic approach ensures that all aspects of access security, from general user access to highly sensitive privileged accounts, are meticulously protected against potential security breaches, thereby enhancing the overall security of IT assets.
Importance of Managing Privileged Identities
The importance of meticulously managing privileged identities cannot be overstated in today’s threat landscape. Compromised privileged accounts are frequently the gateway for sophisticated cyber-attacks, allowing unauthorized access to sensitive data and critical systems. An effective PIM solution, such as the Endpoint Privilege Tool (AdminbyRequest) offered by Teamwin Global Technologica, is designed to regain control over user privileges and protect sensitive data from potential breaches. By safeguarding endpoints through stringent management of local admin privileges, organizations can significantly mitigate the risks associated with escalated permissions. This proactive approach ensures that only authorized privileged users can access vital IT assets, thereby fortifying the overall security posture against malicious actors and preventing devastating security breaches.
How Teamwin Global Can Help
Teamwin Global Technologica Pvt Ltd is an IT services company specializing in empowering its clients through a comprehensive suite of IT security solutions, particularly in the realm of IAM, PIM, and PAM. With highly trained and motivated teams updated on the latest technologies, Teamwin Global Technologica provides unwavering 24/7 support. They emphasize a custom-tailored approach, ensuring the best fit and value for money in securing privileged accounts and sensitive data. By offering reliable, efficient, and valuable solutions, including managed support services and responsive customer support, Teamwin Global assists organizations in building a robust security posture, preventing unauthorized access, and mitigating the risk of security breaches. Their commitment to educating clients ensures informed decisions for enhanced security.
Our Cyber Security & Secure networking Services
Biometric devices and management platforms are central to modern enterprise identity and access control. Together, they provide secure, efficient, and scalable solutions for employee authentication, [...]
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
🧠 SIEM & SOAR Solutions | Real-Time Threat Detection & Automated Response – Teamwin Global 📌 Overview Centralize your security data and automate incident response [...]
Articles from the latest news
Latest Tech Articles news
A recent data breach disclosure from PayPal has sent ripples through the cybersecurity community, highlighting a critical flaw in their PayPal Working Capital (PPWC) loan [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Jenkins Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected Jenkins weekly versions [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Google Chrome for Desktop Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected [...]