Cloud Security: Best Practices and Principles
Teamwin Global Technologica is dedicated to empowering its clients through a comprehensive suite of IT security solutions. We recognize the paramount importance of our customers’ businesses, and we are committed to providing unwavering support at all times. Safeguarding your enterprise and ensuring tomorrow’s success is our primary objective.
Understanding Cloud Security
What is Cloud Security?
Cloud security refers to a comprehensive set of policies, technologies, applications, and controls utilized to protect virtualized IP, data, applications, and the associated infrastructure of cloud computing. It encompasses the strategies and measures put in place to ensure a secure cloud environment for all cloud data and cloud resources. This includes everything from the physical infrastructure of the cloud provider to the applications and data residing within the cloud environment. Robust cloud security is paramount in today’s interconnected digital landscape.
Importance of Cloud Security in Modern Computing
The proliferation of cloud computing, encompassing public cloud, private cloud, and hybrid cloud models, has made cloud security an indispensable component of modern IT strategy. As organizations increasingly migrate critical applications and sensitive data to the cloud, the importance of maintaining a strong security posture cannot be overstated. Effective cloud security solutions and security measures are essential to protect against a myriad of security risks and ensure the confidentiality, integrity, and availability of cloud data.
Common Security Risks in Cloud Environments
Despite the inherent benefits of cloud environments, they are not immune to security risks. Common threats include data breaches, misconfigurations, insecure APIs, identity and access management vulnerabilities, and insider threats. Without comprehensive security controls and cloud security strategies, organizations face significant exposure. Adopting security best practices, implementing robust security policies, and leveraging advanced security tools are critical to mitigating these risks and establishing a secure cloud infrastructure.
Security Best Practices for Cloud Computing
Implementing Strong Security Policies
Implementing robust security policies is a cornerstone of maintaining a secure cloud environment. These policies should encompass comprehensive guidelines for data security, access management, incident response, and compliance. Organizations must establish clear directives for all cloud resources, whether residing in a public cloud, private cloud, or hybrid cloud setup. Teamwin Global Technologica emphasizes the development of tailored security policies that align with an organization’s unique operational needs and regulatory requirements, ensuring that every aspect of cloud computing is governed by stringent security measures designed to mitigate potential security risks and enhance the overall cloud security posture. This proactive approach builds trust and safeguards valuable cloud data.
Using Cloud Security Tools Effectively
Leveraging cloud security tools effectively is paramount for a strong security posture in the dynamic cloud computing landscape. This involves deploying a comprehensive suite of cloud security solutions such as Cloud Security Posture Management (CSPM) tools to continuously monitor configurations, Cloud Workload Protection Platforms (CWPP) to secure applications and workloads, and Security Information and Event Management (SIEM) systems for real-time threat detection. Products from vendors like Palo Alto Networks, Fortinet, Trend Micro, and Wiz, among others, offer advanced capabilities for securing various cloud environments including AWS, Google Cloud, and Microsoft Azure. Teamwin Global Technologica assists clients in selecting, integrating, and optimizing these security tools to achieve a robust cloud security posture, ensuring continuous protection against evolving threats and maximizing the value of their cloud infrastructure investments.
Regularly Checking Security Posture
Regularly checking and enhancing the cloud security posture is a critical ongoing process that requires continuous vigilance. This involves routine security audits, penetration testing, and vulnerability assessments across all cloud resources to identify and remediate potential security risks before they can be exploited. Tools like Qualys, Rapid7, and Tenable provide comprehensive vulnerability management, while services from Arctic Wolf or CrowdStrike can offer continuous monitoring and threat detection. Teamwin Global Technologica’s expertise in cloud security posture management ensures that organizations consistently evaluate their security controls, adapt to new threats, and maintain compliance with industry standards. This proactive approach to security checks not only improves overall data security but also reinforces the secure cloud environment, building greater trust in the organization’s cloud computing capabilities.
Types of Cloud Security Solutions
Public, Private, and Hybrid Cloud Security
Cloud security solutions are specifically tailored to address the distinct needs of various cloud deployment models: public cloud, private cloud, and hybrid cloud. In the public cloud, security measures often involve shared responsibility, where the cloud provider secures the underlying infrastructure, and the customer is responsible for security within their applications and data. Private cloud environments, on the other hand, offer organizations greater control over their entire cloud infrastructure, necessitating robust cloud security policies and security controls directly managed by the enterprise. Hybrid cloud models combine elements of both, requiring comprehensive security strategies that seamlessly extend security posture across diverse cloud environments, ensuring consistent data security and mitigating potential security risks for all cloud resources.
Role of Cloud Service Providers in Security
Cloud service providers (CSPs) like AWS, Google Cloud, and Microsoft Azure play a pivotal role in cloud security. They are primarily responsible for the security “of” the cloud, encompassing the physical infrastructure, network, and foundational services. This includes ensuring the secure cloud environment through stringent security measures, maintaining compliance certifications, and offering a suite of security tools to their customers. While CSPs provide robust cloud security at the infrastructure level, organizations retain responsibility for security “in” the cloud, meaning the protection of their applications, data, and configurations. Teamwin Global Technologica works closely with clients to navigate this shared responsibility model, implementing security best practices and leveraging CSP-specific security controls to enhance the overall cloud security posture.
Zero Trust Security Model in Cloud
The Zero Trust security model is increasingly critical in cloud computing, shifting from perimeter-based security to a “never trust, always verify” approach. In the cloud environment, where traditional network boundaries are dissolving, Zero Trust mandates strict identity verification for every user and device attempting to access cloud resources, regardless of their location. This model emphasizes micro-segmentation, least privilege access, and continuous monitoring of all network traffic and cloud data. Adopting Zero Trust principles significantly enhances the security posture by minimizing the attack surface and containing potential breaches within the cloud infrastructure. Teamwin Global Technologica helps organizations implement Zero Trust strategies, integrating solutions from vendors like Zscaler, Palo Alto Networks, and Okta to build a truly secure cloud environment.
Enhancing Security Posture with Micro-Segmentation
What is Micro-Segmentation?
Micro-segmentation is a robust cloud security solution that divides data centers and cloud environments into distinct, isolated security segments down to the individual workload level. This advanced network security technique creates granular security zones, allowing organizations to define and enforce highly specific security policies for each application, service, or virtual machine. Unlike traditional network segmentation, which typically operates at a broader network level, micro-segmentation enables precise control over traffic flows, preventing unauthorized lateral movement within the cloud infrastructure. By isolating critical cloud resources and sensitive data, micro-segmentation significantly reduces the attack surface and contains security risks, fortifying the overall cloud security posture. This strategy is foundational for a secure cloud environment.
Benefits of Micro-Segmentation in Cloud Security
The benefits of micro-segmentation in cloud security are profound, directly enhancing the security posture and resilience against cyber threats. Firstly, it drastically limits lateral movement of attackers within the cloud environment, preventing a breach in one segment from compromising the entire cloud infrastructure. Secondly, it provides granular visibility and control over network traffic, enabling organizations to enforce least privilege access and detect anomalies more effectively. Thirdly, micro-segmentation simplifies compliance by allowing specific security policies to be applied to regulated data and applications. Furthermore, it improves incident response by containing breaches to smaller segments, thereby minimizing business disruption and data loss. Vendors like Illumio and VMware offer leading micro-segmentation solutions.
How Teamwin Global Adds Value through Micro-Segmentation
Teamwin Global Technologica adds significant value to our clients’ cloud security posture through the strategic implementation of micro-segmentation. We leverage our expertise to design and deploy bespoke micro-segmentation strategies tailored to each organization’s unique cloud environment, whether it’s public cloud, private cloud, or hybrid cloud. Our approach ensures that every cloud resource and piece of cloud data is protected by precise security controls, significantly reducing potential security risks. By integrating advanced security tools and security measures, we empower clients to achieve granular network visibility and enforce strict security policies, bolstering their secure cloud environment. Teamwin Global is committed to enhancing your robust cloud security, treating each customer as if they are the only one, and ensuring tomorrow’s success.
Addressing Cloud Security Challenges
Identifying Common Security Issues
Identifying common security issues within the intricate cloud environment is a critical step towards maintaining a robust cloud security posture. Organizations frequently grapple with challenges such as misconfigurations of cloud resources, leading to unintentional exposure of sensitive cloud data. Inadequate identity and access management (IAM) practices can create vulnerabilities, while shadow IT—unauthorized cloud service usage—often bypasses established security controls. Furthermore, sophisticated cyber threats, including ransomware and advanced persistent threats (APTs), continuously target the cloud infrastructure, necessitating proactive threat management and continuous vigilance. Teamwin Global Technologica aids clients in pinpointing these security risks and developing tailored cloud security strategies to mitigate them effectively, ensuring a secure cloud environment.
Best Practices to Mitigate Security Threats
Implementing best practices is essential to mitigate the myriad of security threats in the dynamic cloud computing landscape. This involves adopting a Zero Trust security model, ensuring every access request to cloud data and cloud resources is rigorously verified. Regular security audits, penetration testing, and vulnerability assessments using security tools from vendors like Qualys or Rapid7 are crucial for identifying and remediating weaknesses. Furthermore, emphasizing threat preparedness and proactive threat management, as offered by Teamwin Global’s cybersecurity features, allows organizations to anticipate and respond to emerging security risks efficiently. Educating employees on security best practices, such as strong password hygiene and phishing awareness, also significantly strengthens the overall cloud security posture, creating a more secure cloud environment.
Collaborating with Cloud Providers for Enhanced Security
Collaborating closely with cloud service providers (CSPs) like AWS, Google Cloud, and Microsoft Azure is fundamental for achieving enhanced cloud security. While CSPs are responsible for the security “of” the cloud, ensuring the robustness of their underlying cloud infrastructure, organizations must uphold their responsibility for security “in” the cloud. This partnership entails understanding the shared responsibility model, leveraging the native security tools and services offered by the cloud provider, and configuring them according to best practices. Teamwin Global Technologica facilitates this collaboration, guiding clients in optimizing CSP-specific security controls and integrating third-party cloud security solutions to create a seamless and secure cloud environment, thereby bolstering their overall cloud security posture against evolving security risks.
Some of the Comprehensive Cloud Security Providers
Here’s a categorized table of the listed cloud security vendors, grouped by their primary technologies:
| Technology Category | Vendors |
|---|---|
| Cloud Security Posture Management (CSPM) | Prisma Cloud (Palo Alto Networks), Wiz, Orca Security, Lacework, Microsoft Defender for Cloud, AWS Security, Google Cloud Security, IBM Security |
| Cloud Workload Protection Platforms (CWPP) | Trend Micro, SentinelOne, Palo Alto Networks, Sophos, CrowdStrike, Lacework, Wiz, Orca Security |
| Cloud Access Security Broker (CASB) | Netskope, McAfee (Trellix), Symantec (Broadcom), Bitglass (Forcepoint), Microsoft Defender for Cloud |
| Zero Trust & Identity Management | Okta, Cisco, Zscaler, Palo Alto Networks (Prisma Access), Fortinet, Illumio |
| Web & Application Security / WAF | Cloudflare, Barracuda Networks, Fortinet, AWS WAF, Akamai (not listed above but notable) |
| Email Security / DLP / Data Protection | Proofpoint, Symantec (Broadcom), Trend Micro, Forcepoint |
| SIEM / Threat Detection & Response | IBM Security, Rapid7, LogRhythm (not listed above), Arctic Wolf, Microsoft Sentinel |
| Vulnerability Management | Qualys, Tenable, Rapid7 |
| Endpoint Detection & Response (EDR) | CrowdStrike, SentinelOne, Sophos, Trellix |
| DevSecOps / Cloud-native App Security | Snyk, Wiz, Orca Security, Lacework |
⚠️ Some vendors appear in multiple categories due to their broad solutions across cloud security.
Let me know if you’d like this in a downloadable format like Excel or CSV.
The Future of Cloud Security
Emerging Trends in Cloud Security
The future of cloud security is shaped by several emerging trends that promise to further enhance the robust cloud security posture. The increased adoption of AI and machine learning for predictive threat detection and automated incident response is becoming paramount, enabling organizations to proactively identify and neutralize security risks before they escalate. Serverless computing and containerization are driving new security paradigms, emphasizing the need for specialized cloud security solutions like those offered by Snyk or Lacework for securing code and workloads at scale. Furthermore, the expansion of the attack surface due to the proliferation of IoT devices and edge computing necessitates comprehensive security measures that extend beyond the traditional cloud environment, demanding more sophisticated cloud security strategies.
Preparing for Evolving Security Threats
Preparing for evolving security threats in the cloud environment demands a forward-thinking and adaptive approach to cloud security. This involves continuous investment in threat intelligence and advanced security tools to stay ahead of sophisticated cyber adversaries. Organizations must prioritize robust cloud security posture management (CSPM) to ensure continuous compliance and identify misconfigurations across all cloud resources. Embracing a culture of threat preparedness and proactive threat management, core components of Teamwin Global’s cybersecurity offerings, is crucial for building resilience. Regularly updating incident response plans, conducting tabletop exercises, and fostering a security-aware workforce are also vital steps in fortifying the cloud infrastructure against the ever-changing landscape of security risks.
Investing in Robust Cloud Security Solutions
Investing in robust cloud security solutions is a strategic imperative for any organization committed to safeguarding its cloud data and cloud infrastructure. This encompasses a comprehensive suite of cloud security solutions, including advanced threat detection platforms, data encryption tools, and identity and access management systems. Solutions from industry leaders like Palo Alto Networks, Fortinet, and CrowdStrike offer cutting-edge capabilities for defending against complex security risks across public cloud, private cloud, and hybrid cloud environments. Teamwin Global Technologica is dedicated to empowering clients by providing expert guidance on selecting and implementing these security controls, ensuring that every customer achieves a superior cloud security posture. Our commitment is to provide unwavering support, ensuring tomorrow’s success in a secure cloud environment.
Our Cyber Security & Secure networking Services
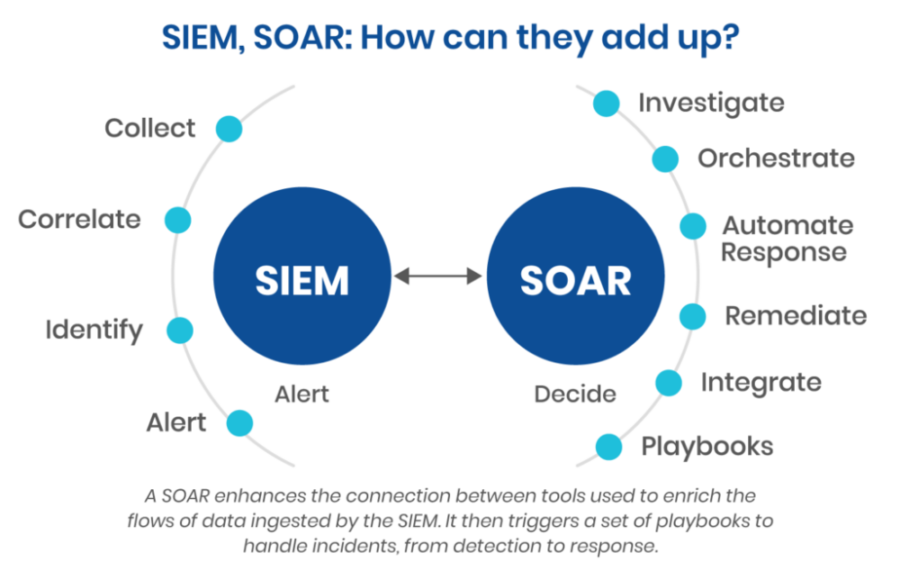
🧠 SIEM & SOAR Solutions | Real-Time Threat Detection & Automated Response – Teamwin Global 📌 Overview Centralize your security data and automate incident response [...]
Comprehensive Cybersecurity Solutions for Modern Businesses Protect your organization with end-to-end cybersecurity solutions from Teamwin Global. We defend your data, infrastructure, and people against today’s [...]
Why Choose TeamWin for Managed IT Services TeamWin offers reliable, scalable Managed IT Services designed for SMEs and small businesses. We provide proactive IT support [...]
Articles from the latest news
Latest Tech Articles news
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Zyxel Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Systems Affected Zyxel devices 4G/5G [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Trend Micro Apex One Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in VMware Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected VMware Aria [...]