converge your vision and values
Accelerate innovation. Drive efficiency. Stay competitive.
🔹 Key Areas & Partners
☁️ Cloud Enablement
Vendors: AWS | Azure | Google Cloud | Oracle Cloud
🤖 Automation & AI
Vendors: UiPath | Automation Anywhere | IBM Watson | Power BI
📊 Data & Analytics
Vendors: Tableau | Google AI | Microsoft BI | Snowflake
🔐 Cybersecurity
Vendors: Palo Alto | Fortinet | Cisco | Check Point
🏢 Enterprise Apps (ERP/CRM)
Vendors: SAP | Oracle | Salesforce | Zoho
💬 Customer Experience
Vendors: Adobe | HubSpot | Freshworks
Expertise and Experience:
Highly Skilled Team: Our team consists of certified professionals with extensive experience in various IT domains.
Comprehensive Solutions:
End-to-End Services: We offer a wide range of services, including network management, cybersecurity, cloud solutions, and IT consulting.
why choose us

Our Cyber Security & Secure networking Services
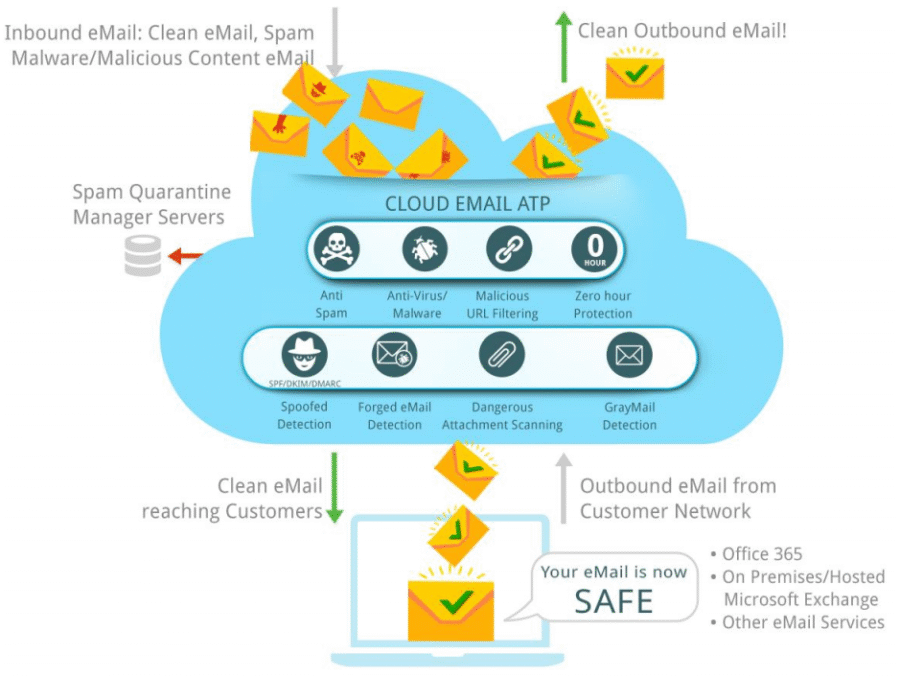
🛡️ Email Security Solutions | Advanced Protection from Phishing, Spam & Malware – Teamwin Global 📌 Overview Secure your organization’s most common attack vector — [...]
Structured Cabling & Managed IT Services by TeamWin TeamWin delivers trusted structured cabling services and networking solutions tailored for businesses of all sizes. Our expert [...]
🔒 Security Operations Center (SOC) Ensure your digital assets are protected with our proactive SOC services: 🛡️ Real-Time Threat Monitoring – Detect and respond to [...]
Articles from the latest news
Latest Tech Articles news
Layer 2 Switching in Network Virtualized Environments In today’s complex network environments, understanding layer 2 switching is crucial, especially within network virtualization. This guide aims [...]
Unmasking Hackerbot-Claw: How CI/CD Misconfigurations Became a Cyber Battlefield for Microsoft and DataDog The landscape of software development and deployment has been dramatically reshaped [...]
In the rapidly evolving landscape of artificial intelligence, the ability to seamlessly transfer contextual information between platforms has remained a significant hurdle. Users investing time [...]