converge your vision and values
🧠 SIEM & SOAR Solutions | Real-Time Threat Detection & Automated Response – Teamwin Global
📌 Overview
Centralize your security data and automate incident response with next-gen SIEM and SOAR platforms. Teamwin Global delivers integrated security visibility, threat intelligence, and rapid mitigation through industry-leading solutions.
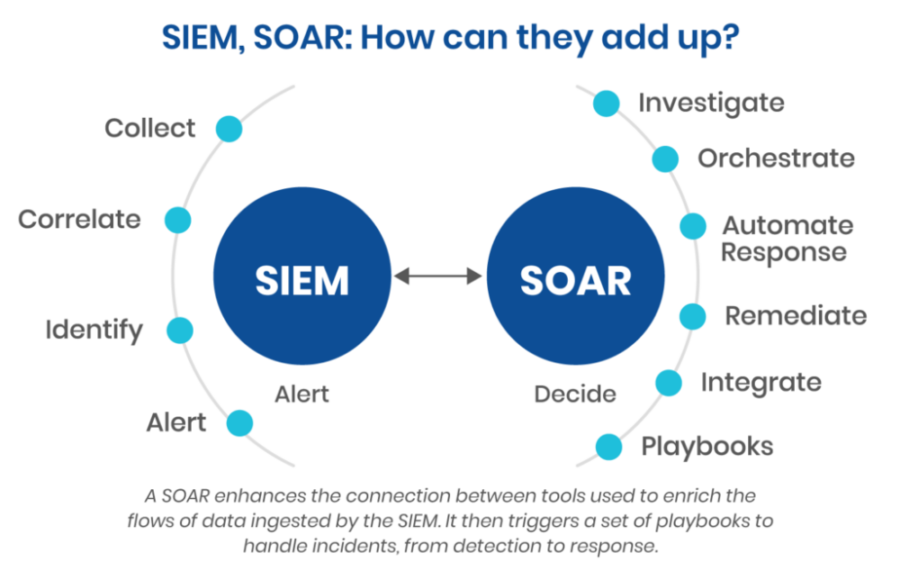
🚨 What Are SIEM & SOAR?
| 🛡️ Technology | 💡 Definition |
|---|---|
| SIEM (Security Information and Event Management) | Collects, normalizes, and analyzes logs across systems to detect threats in real time. |
| SOAR (Security Orchestration, Automation, and Response) | Automates security workflows, incident response, and integrates tools for faster actions. |
🔍 Key Capabilities
-
📊 Real-Time Log Monitoring & Correlation
-
🧠 Behavioral & UEBA Analytics
-
🧩 Integration with Firewalls, EDR, IAM, Cloud, etc.
-
🤖 Automated Playbooks & Response Actions
-
📁 Centralized Incident Management
-
📈 Compliance Reporting (PCI-DSS, ISO, HIPAA)
-
🌐 Threat Intelligence Feeds & IOC Matching
🤝 SIEM & SOAR Vendors
🌐 Global Industry Leaders
-
![🧠] Splunk Enterprise Security – Advanced analytics, machine learning
-
![🔎] IBM QRadar – Scalable enterprise-grade SIEM
-
![🚀] Microsoft Sentinel (Azure) – Cloud-native, AI-enhanced SIEM
-
![🔧] LogRhythm SIEM + SOAR – Integrated detection & response
-
![⚡] Exabeam – UEBA-driven SIEM with automation
-
![📡] Securonix Next-Gen SIEM – Big data and cloud-native
-
![🔐] Rapid7 InsightIDR – Lightweight SIEM with automation
-
![🧬] Elastic Security – SIEM on Elastic Stack
-
![🕵️♂️] Fortinet FortiSIEM – Unified NOC + SOC view
-
![📦] Palo Alto Cortex XSOAR – Powerful playbook-driven SOAR
🇮🇳 Trusted Indian Providers
-
![🛠️] Seqrite Hawk – SIEM built for Indian enterprises
-
![🧰] EventTracker (by Netsurion) – Managed SIEM/SOC platform
-
![🛡️] CyberSane SIEM – Indigenous security analytics
🔌 Integration Ready With
-
🔐 Firewalls & UTM
-
🖥️ Endpoint Detection & Response (EDR/XDR)
-
☁️ Cloud Platforms (AWS, Azure, GCP)
-
👥 Identity & Access Management
-
📬 Email Security & DLP
-
🌍 Threat Intelligence Platforms
🛠️ Services Offered by Teamwin Global
-
🔎 SIEM/SOAR Consulting & Architecture Design
-
🚀 Deployment & Integration Services
-
🤖 Custom Playbook Development
-
📞 24×7 Managed Detection and Response (MDR)
-
📚 Regulatory Compliance Reporting
-
🔁 Threat Hunting & SOC Modernization
🧭 Use Cases
-
🏦 Financial Sector: Detect fraud & insider threats
-
🏥 Healthcare: HIPAA-compliant threat monitoring
-
🏭 Manufacturing: OT/IT integration for anomaly detection
-
🏢 Enterprises: Unified SOC view for hybrid environments
🌟 Why Partner with Teamwin Global?
-
✔️ Certified SIEM & SOAR architects
-
✔️ Vendor-agnostic approach
-
✔️ Local + Global support teams
-
✔️ Flexible licensing & managed services
-
✔️ Tailored to SMBs, Enterprises, and Government
Expertise and Experience:
Highly Skilled Team: Our team consists of certified professionals with extensive experience in various IT domains.
Comprehensive Solutions:
End-to-End Services: We offer a wide range of services, including network management, cybersecurity, cloud solutions, and IT consulting.
why choose us
Our Cyber Security & Secure networking Services
At Teamwin Global, we provide end-to-end cybersecurity solutions built for today’s digital threats. Backed by industry leaders like Seqrite, CrowdStrike, and Microsoft, we help secure [...]
Structured Cabling & Managed IT Services by TeamWin TeamWin delivers trusted structured cabling services and networking solutions tailored for businesses of all sizes. Our expert [...]
Fast. Reliable. Future-Ready. 🧠 1. Introduction Brief overview of modern enterprise networking needs Importance of speed, reliability, and smart planning 🔀 2. 10G Network Switching [...]
Articles from the latest news
Latest Tech Articles news
Layer 2 Switching in Network Virtualized Environments In today’s complex network environments, understanding layer 2 switching is crucial, especially within network virtualization. This guide aims [...]
Unmasking Hackerbot-Claw: How CI/CD Misconfigurations Became a Cyber Battlefield for Microsoft and DataDog The landscape of software development and deployment has been dramatically reshaped [...]
In the rapidly evolving landscape of artificial intelligence, the ability to seamlessly transfer contextual information between platforms has remained a significant hurdle. Users investing time [...]






