converge your vision and values
🔒 Security Operations Center (SOC)
Ensure your digital assets are protected with our proactive SOC services:
-
🛡️ Real-Time Threat Monitoring – Detect and respond to cyber threats instantly.
-
🧠 Security Intelligence & Analytics – Advanced analytics to spot hidden risks.
-
🚨 Incident Response & Management – Rapid containment and mitigation of attacks.
-
📋 Compliance & Reporting – Stay audit-ready with automated compliance tools.
✅ Protect your organization from cyber threats before they impact operations.
📡 Network Operations Center (NOC)
Maintain network uptime and performance with our expert NOC support:
-
📶 24/7 Network Monitoring – Continuous oversight to prevent downtime.
-
🔧 Fault Detection & Resolution – Immediate issue identification and remediation.
-
🖧 Infrastructure Management – Proactive care for routers, switches, and servers.
-
📊 Performance Reporting – Detailed dashboards and SLA metrics.
✅ Maximize uptime and keep your business online and connected.
⚙️ Integrated SOC/NOC Services
Unify security and network operations with a single trusted partner:
-
🔁 Seamless Coordination between security and IT ops teams
-
⏱️ Faster Response Times to both cyber threats and system outages
-
💰 Cost-Effective by reducing redundancy and enhancing efficiency
Expertise and Experience:
Highly Skilled Team: Our team consists of certified professionals with extensive experience in various IT domains.
Comprehensive Solutions:
End-to-End Services: We offer a wide range of services, including network management, cybersecurity, cloud solutions, and IT consulting.
why choose us

Our Cyber Security & Secure networking Services
Comprehensive Cybersecurity Solutions for Modern Businesses Protect your organization with end-to-end cybersecurity solutions from Teamwin Global. We defend your data, infrastructure, and people against today’s [...]
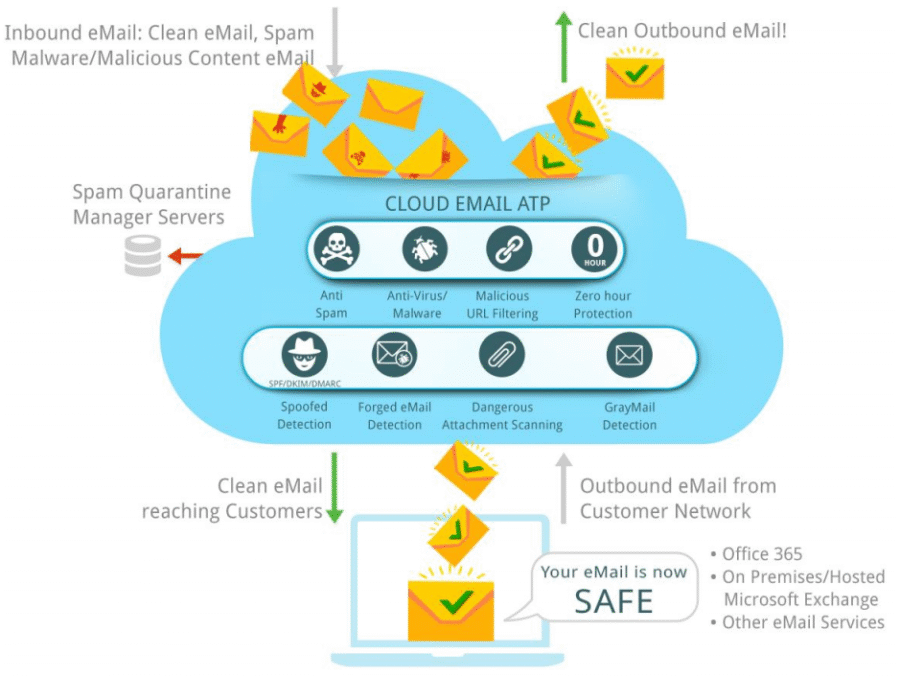
🛡️ Email Security Solutions | Advanced Protection from Phishing, Spam & Malware – Teamwin Global 📌 Overview Secure your organization’s most common attack vector — [...]
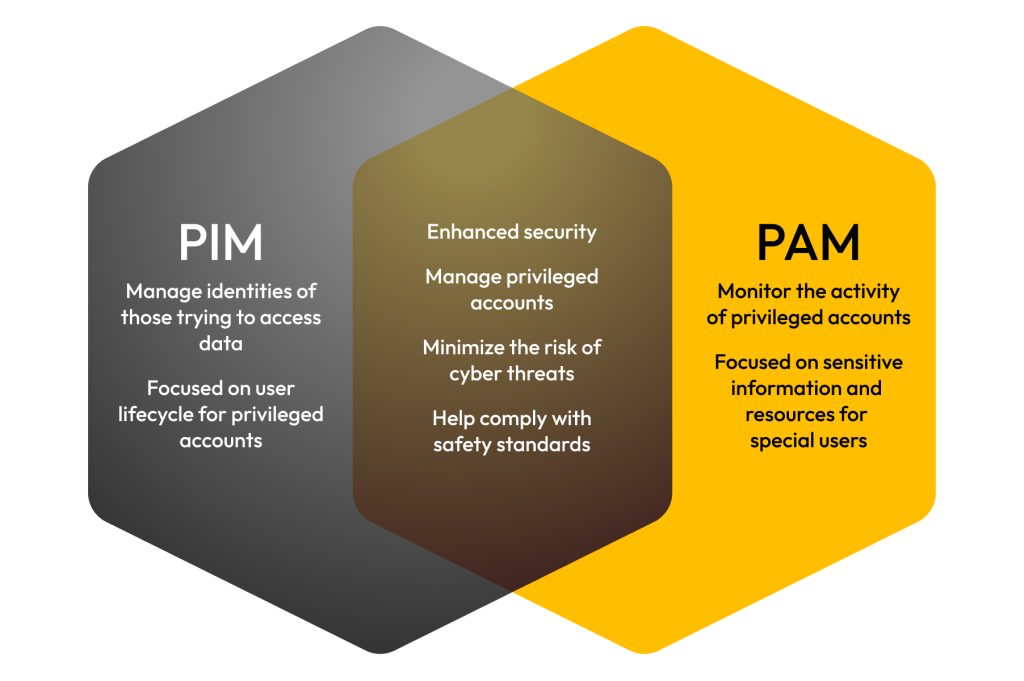
🛡️ PIM & PAM Solutions – Teamwin Global Secure, Monitor & Control Privileged Access.Protect critical assets with advanced Privileged Identity & Access Management solutions. 🔍 [...]
Articles from the latest news
Latest Tech Articles news
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Zyxel Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Systems Affected Zyxel devices 4G/5G [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in Trend Micro Apex One Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: CRITICAL Software Affected [...]
—–BEGIN PGP SIGNED MESSAGE—– Hash: SHA256 Multiple Vulnerabilities in VMware Products Indian – Computer Emergency Response Team (https://www.cert-in.org.in) Severity Rating: HIGH Software Affected VMware Aria [...]