We’re currently living in an age where digital threats loom large. Among these, ransomware has emerged as a formidable adversary, disrupting businesses and individuals alike. [...]
The convergence of edge analytics and IoT gateways marks a pivotal shift in the landscape of data processing, offering unparalleled opportunities for real-time insights and [...]
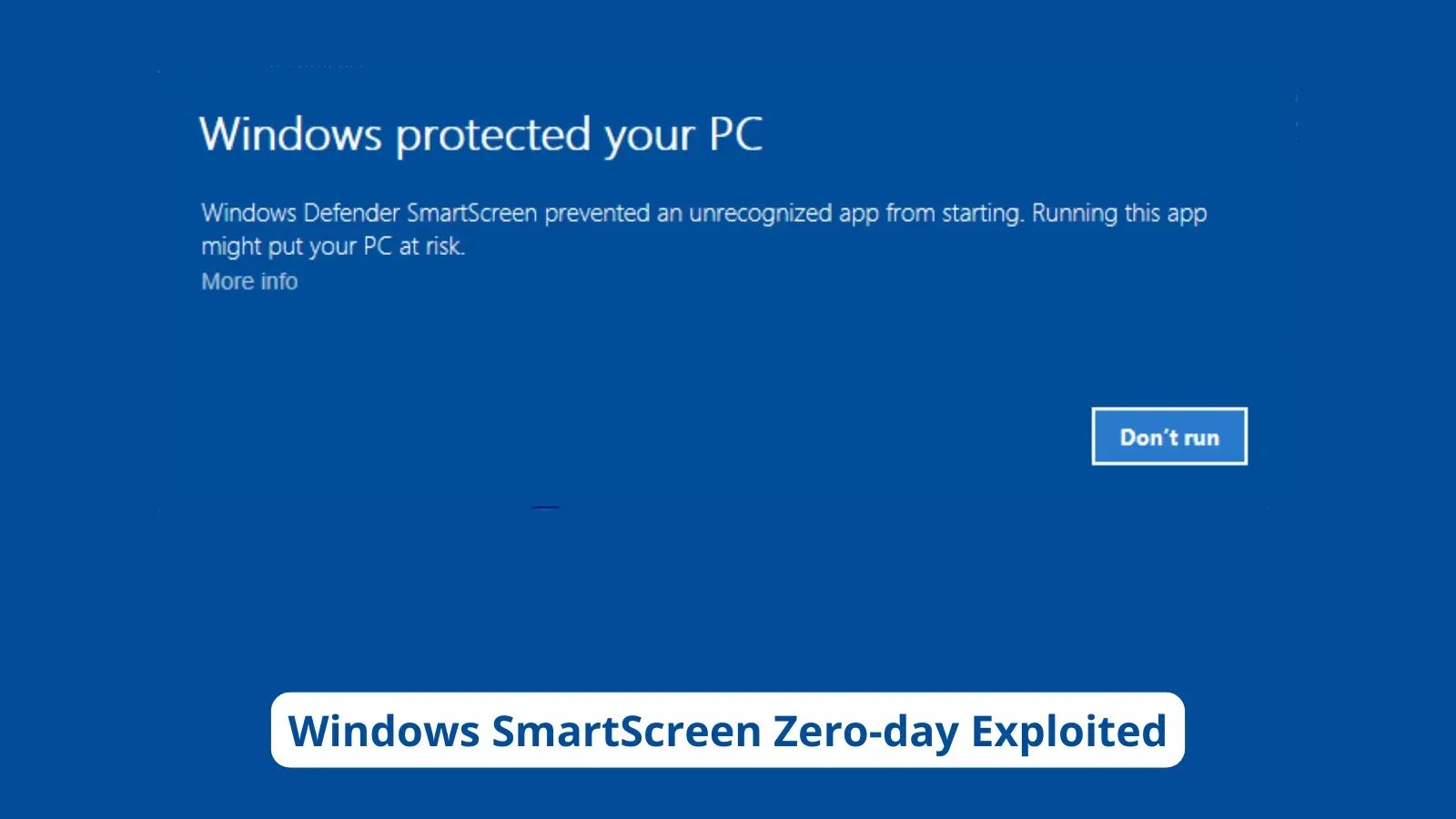
Hackers Exploiting Windows SmartScreen Zero-day Flaw to Deploy Remcos RAT Microsoft released multiple security patches as part of their Patch Tuesday, in which three zero-day vulnerabilities [...]
As industries increasingly adopt IoT solutions to drive innovation and streamline operations, the need for effective interoperability between devices using different communication standards has become [...]
OwnCloud Critical Vulnerability Exploited in the Wild Owncloud was discovered with a new vulnerability associated with exposing sensitive information to an unauthorized third party that [...]
What is Secure Access Service Edge (SASE) – A Managerial Guide For Network Security Secure Access Service Edge (SASE) is a cloud-based security service that [...]
In this article, we delve into the fascinating world of IoT communication protocols, exploring the common standards that enable IoT gateways to communicate with diverse [...]
What is Firewall-as-a-Service (FWaaS)? How Does It Work? A firewall serves as a barrier to unapproved network traffic. Additional organizational security policies are enforced to [...]
3 Critical Vulnerabilities Expose own Cloud Users to Data Breaches The maintainers of the open-source file-sharing software ownCloud have warned of three critical security flaws [...]
The interconnected nature of IoT devices presents both unprecedented opportunities and unparalleled challenges for businesses and consumers alike. With an array of devices collecting, transmitting, [...]