In the rapidly expanding world of Internet of Things (IoT), the role of IoT gateways has become increasingly crucial. These gateways serve as the bridge [...]
As we delve into the world of IoT gateways, we will explore their role in facilitating data collection, analysis, and communication within disparate IoT ecosystems. [...]
How can IT services help with digital transformation? IT services play a crucial role in facilitating and driving digital transformation within an organization. Digital transformation [...]
In a world where efficiency and security are paramount, the management of Active Directory (AD) has become a critical element of IT administration. With its [...]
Best Practices For Securing Your Cloud Infrastructure As more and more organizations move their operations to the cloud, cloud security has become a critical concern. [...]
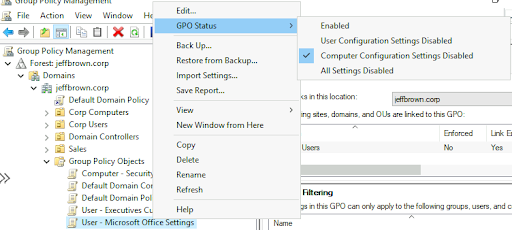
As the backbone of centralized management in Windows environments, Group Policies play a crucial role in maintaining security, enforcing settings, and ensuring consistency across an [...]
Unleashing the Power of Edge Computing in Network Infrastructure Edge computing is a paradigm that brings computation and data storage closer to the location where [...]
In the ever-evolving landscape of cybersecurity, organizations are constantly seeking robust solutions to fortify their digital infrastructure against an array of threats. At the heart [...]
How can organizations protect against common Active Directory attacks? In an increasingly digital world, the Active Directory (AD) has become a prime target for cyber [...]
Rhysida Ransomware Attacking Windows Machine Through VPN Devices and RDP Rhysida, a new ransomware group, hit its first victim in May 2023. They use their [...]